- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
NAT Bidirectionnal,IPSEC NAT-T and secondary address problem
- LIVEcommunity
- Discussions
- General Topics
- Re: NAT Bidirectionnal,IPSEC NAT-T and secondary address problem
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-07-2012 08:37 AM
Hello,
I am trying to have a Cisco router establishing an IP SEC Tunnel behind a pao alto firewal configured in L3 Mode.
The tunnel should be established on a secondary address on a sub interface
Eth 1 Public, Two Sub interface 1.666 and 1.667
eth1.666 address is x.y.z.131/25
and need the tunnel on x.y.z.132 then I do NAT 1-1 rule with option bidirectionnal The source of the tunnel is 10.35.3.253 on eth2.500
The IKE exchange begin but stop in the middle.
If I use x.y.z.131 no problem, it works.
But I need the 131 address for other things.
What should I do for the NAt 1-1 to accept the secondary address ?
Jean-Luc
- Labels:
-
Configuration
-
Networking
-
Troubleshooting
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-07-2012 09:46 PM
Is the Cisco establishing the VPN tunnel with the Palo Alto firewall or the firewall is just in a pass through stage for ipsec traffic?
It somehow appears from the description the tunnel is terminating on the firewall. Correct me if I am wrong.
If that is the case and from the description of the two ip-addresses in use , you can use the the feature of secondary ip-address on the interface and not the sub-interfaces.
What I mean is the following:-
Trust Zone:- Internal corporate network
Untrust Zone:- Outside World
VPN zone :- tunnel is in this zone. (VPN users)
From above, 10.30.6.59/24 is the interface address. However the VPN ike-gateway address can be set as a secondary ip-address on the interface as 10.30.6.110/32 as seen above.
Tunnel will be in VPN zone:-
NAT rule should look like the following:-
One rule for the trust users and one for the VPN users (Ip-pool)
Also make sure you have security rules from VPN to Trust and the other way around.
And there is no explicit deny rule in the security rule base.
Let me know if this helps.
Regards
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-07-2012 10:28 PM
Hello,
The PA-200 is just pass-through.
And the problem is that the response is not correctly forwarded to the Cisco router. The IKE exchange get stuck in the middle :
From one side it says : MM_NO_STATE and from the other MM_SA_SETUP.
I will make a schema and post it.
could it be related to the two public link on the same physical interface ? If absolutely necessary I can ask to have the the two sub interface on two physical one.
thnaks trying to help
Jean-Luc
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-07-2012 10:43 PM
Jean,
If that is the case, we would like see the configuration and review logs on the firewall.
Does the second sub-interface have the ip-address in the same subnet as the first?
Regards
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-07-2012 10:44 PM
Hello,
Here is the schema:
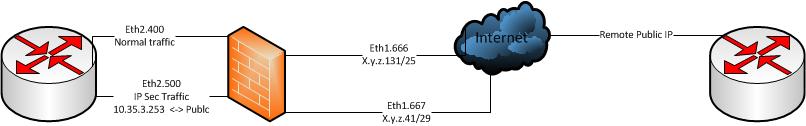
Hope this can help understanding.
I prefer to terminate the tunnel on the cisco router because we have vrf-lite configuration on it. And if we terminate the VPN on the Palo-Alto, they will not be vrf-aware
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-09-2012 07:06 AM
Bug from ISP, excuse for the trouble
Jean-Luc
- 1 accepted solution
- 6490 Views
- 5 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Asymmetric Routing - Palo Edge Firewall Active/Passive to Nexus Core in General Topics
- PAN-OS 11.1.13 Predefined reports displaying IPv4 addresses in IPv6 format in General Topics
- Prisma Browser – First-Time Login Issue Assistance Required in General Topics
- GlobalProtect Agent constantly 'Not Responding'. in GlobalProtect Discussions
- Windows Clients – Captive Portal Not Triggering with GlobalProtect Always-On Enabled in General Topics



