- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
No url filtering is configured, but show session can see url filtering enable
- LIVEcommunity
- Discussions
- General Topics
- Re: No url filtering is configured, but show session can see url filtering enable
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
No url filtering is configured, but show session can see url filtering enable
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-10-2022 08:05 AM
Hello
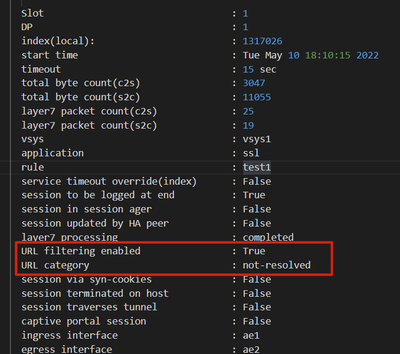
In pan-os 8.1.x, url filtering enable is not configured, but show session can see url filtering enable;
policy:
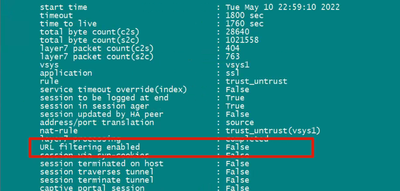
Other versions tested pan-os 10.1.x, url filtering fales:
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-11-2022 07:50 AM
Hi @ZhouYu ,
"show running security-policy" will not list if any security profile is applied on the rule. The "category" in this output is refering to custom URL category used as matching criteria.
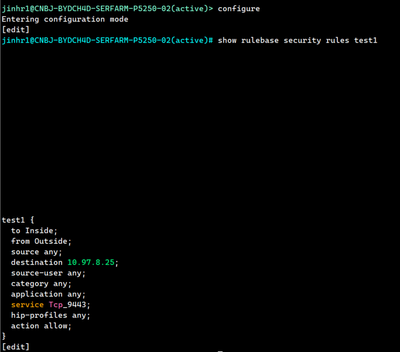
Can you please run and provide the output
> configure
# show rulebase security rules test1
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-11-2022 02:46 PM
Do this
> set cli config-output-format set
> configure
#show rulebase security rules Mahesh
set rulebase security rules Mahesh to Internal_EXT
set rulebase security rules Mahesh from Internal_INT
set rulebase security rules Mahesh source [ 10.36.121.85 10.36.121.183 ]
set rulebase security rules Mahesh destination any
set rulebase security rules Mahesh source-user coc\mparmar2
set rulebase security rules Mahesh category any
set rulebase security rules Mahesh application any
set rulebase security rules Mahesh service any
set rulebase security rules Mahesh action allow
set rulebase security rules Mahesh profile-setting profiles virus Base
set rulebase security rules Mahesh profile-setting profiles spyware DNS_Security
set rulebase security rules Mahesh profile-setting profiles vulnerability Base
set rulebase security rules Mahesh profile-setting profiles wildfire-analysis Base
set rulebase security rules Mahesh profile-setting profiles url-filtering Base
set rulebase security rules Mahesh log-setting Azure
set rulebase security rules Mahesh source-hip any
set rulebase security rules Mahesh destination-hip any
Regards
Help the community: Like helpful comments and mark solutions.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-12-2022 08:35 AM
Hello
I open case today;
=================
According to your captures, we can see below information while running the global counter.
url_db_request -------------- Number os URL database request
url_request_timeout -------------- The url category request is timeout
url_request_pkt_drop -------------- The number of packets get dropped because of waiting for url category request
As per the resolution in KB below, please adjust the value of timeout.
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000ClyeCAC#:~:text=By%20defau....
Moreover, as this PA-5250 appliance subscribes to the license of ‘PAN-DB URL Filtering’, the mechanism of Palo Alto Firewall for layer 7 traffic is always enable the URL filtering to inspect the packets, this is function as designed.
Thanks and please feel free to contact us if you need assistance.
- 2716 Views
- 4 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Identify Manual Cases Using Filter - Layout Rules in Cortex XSIAM Discussions
- Excel downloads being blocked in General Topics
- Not able to log XFF (Actual Client IP) in PaloAlto Logs even when we enable XFF and URL filtering profile in Palo's in Next-Generation Firewall Discussions
- High Data Plane Utilization During Business Hours in Next-Generation Firewall Discussions
- GlobalProtect VPN Client windows 11 crash in GlobalProtect Discussions