- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
PaloAlto WAN Interface segmentation
- LIVEcommunity
- Discussions
- General Topics
- PaloAlto WAN Interface segmentation
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-11-2018 07:04 AM
Hello
Please help me in this scenario
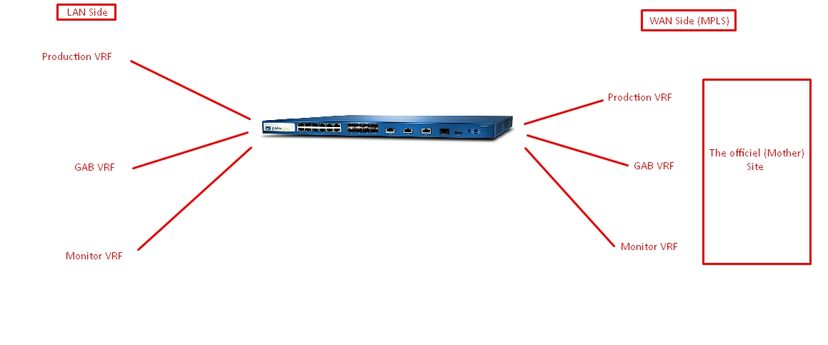
There is the big "Company Site" and the other branches point to this Site, there is an MPLS connection between the branches.
Our need is, the PaloAlto supports segmentation on the WAN part ? can we create a sub-interfaces in the connected interface (MPLS) at the big headquarters, and each sub-interface communicates with a VRF separately.
(NB: Our Client has in WAN side 3 VRF )
Ex:
GAB traffic is coming out of the WAN sub-interface by VRF GAB ...
Traffic production sub-interface WAN by VRF production ...
What I need just a confirmation that on the port Wan PaloAlto supports the segmentation? because in the LAN port I already create sub-interfaces and each sub-interface communicate with his VRF but that on the LAN port, I 'm not sure if the case for the WAN port.
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-11-2018 11:34 PM
The Palo Alto Networks firewall does not diufferentiate between lan or wan interfaces, only the technology 'mode' it is set to, so it supports layer2, layer3 or vwire (and some others but let's just stick to these)
So your MPLS provider will need to transform the traffic to match one of these technologies (we can't terminate mpls on the firewall)
All of these interface types are capable of supporting tagged sub interfaces where you segregate all connected networks using vlan tags
so if your WAN provider supports separating each VRF with a unique VLAN tag, you can perfectly create tagged subinterfaces on your 'wan' layer3 interface and even provide each VRF with it's own zone (if so desired) to provide ganular security zones per remote network
PANgurus - Strata & Prisma Access specialist
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-11-2018 11:34 PM
The Palo Alto Networks firewall does not diufferentiate between lan or wan interfaces, only the technology 'mode' it is set to, so it supports layer2, layer3 or vwire (and some others but let's just stick to these)
So your MPLS provider will need to transform the traffic to match one of these technologies (we can't terminate mpls on the firewall)
All of these interface types are capable of supporting tagged sub interfaces where you segregate all connected networks using vlan tags
so if your WAN provider supports separating each VRF with a unique VLAN tag, you can perfectly create tagged subinterfaces on your 'wan' layer3 interface and even provide each VRF with it's own zone (if so desired) to provide ganular security zones per remote network
PANgurus - Strata & Prisma Access specialist
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-12-2018 02:43 AM
Thank you very much brother, it was very helpful
- 1 accepted solution
- 2433 Views
- 2 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Unable to establish tunnel during Service Connection configuration (Details Added with Screenshot) in Prisma Access Discussions
- Step by Step Radius Configuration for PA-1410 in Next-Generation Firewall Discussions
- Palo Alto VM-Series Software Firewall Keeps Shutting Down in Ubuntu Desktop 24.04.2 LTS KVM in VM-Series in the Private Cloud
- IPSec tunnel over IPSec tunnel not working in General Topics
- Food for Thought - Data Redistribution during HA Failover - User-ID in General Topics