- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
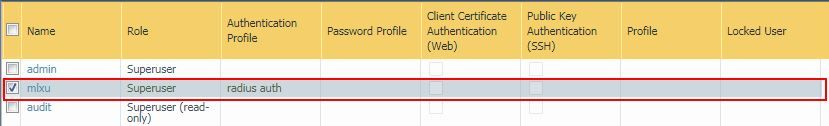
radius authentication issue
- LIVEcommunity
- Discussions
- General Topics
- radius authentication issue
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
radius authentication issue
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-18-2020 06:58 PM
After the device PA-500 is upgraded from 7.1 to 8.1.15, the radius authentication of the user name and password of the device fails, and we can only log in to the device through local authentication. After performing Radius-related configuration according to the configuration guide, the account login still prompts "invalid account or password"
log as follow:
2020-07-16 17:42:25.589 +0800 debug: _authenticate_initial(pan_auth_state_engine.c:2377): Trying to authenticate (init auth): <profile: "", vsys: "", policy: "", username "mlxu"> ; timeout setting: 180 secs ; authd id: 6848127346889719896
2020-07-16 17:42:25.589 +0800 debug: _get_auth_prof_detail(pan_auth_util.c:1060): admin user thru WebUI "mlxu"
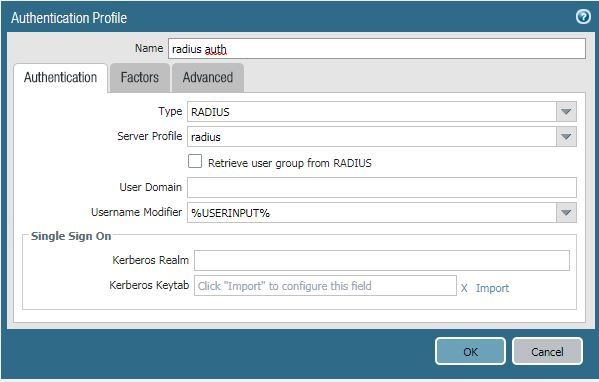
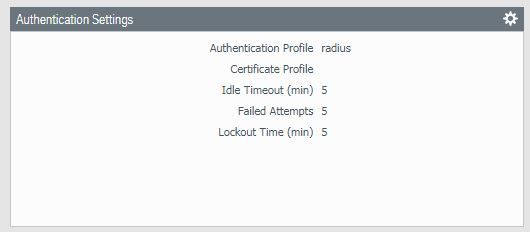
2020-07-16 17:42:25.589 +0800 debug: _get_admin_authentication_profile_by_name(pan_auth_util.c:554): Got auth prof "radius auth" for admin user "mlxu"
2020-07-16 17:42:25.590 +0800 debug: _get_auth_prof_detail(pan_auth_util.c:1081): admin user thru WebUI "mlxu" auth request without vsys: try "shared" any way
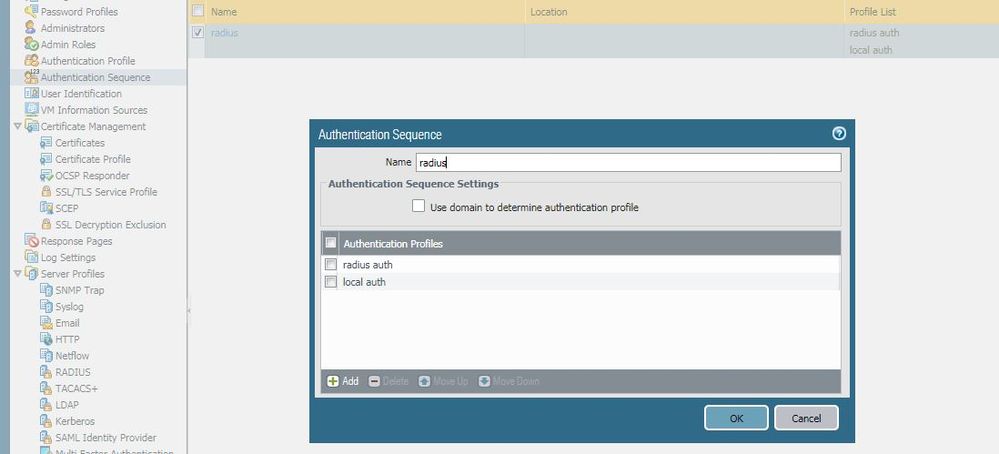
2020-07-16 17:42:25.590 +0800 debug: _get_authseq_profile(pan_auth_util.c:860): Auth profile/vsys (radius auth/shared) is NOT auth sequence
2020-07-16 17:42:25.590 +0800 debug: _retrieve_svr_ids(pan_auth_service.c:645): could not find auth server id vector for radius auth-shared-mfa
2020-07-16 17:42:25.590 +0800 debug: add_info_from_auth_profile_to_request(pan_auth_util.c:1024): MFA is not configured for the auth profile. No mfa server ids for the user "" (prof/vsys: radius auth/shared)
2020-07-16 17:42:25.590 +0800 debug: _authenticate_initial(pan_auth_state_engine.c:2566): Keep original username, i.e., whatever end-user typed, "mlxu" in request->username
2020-07-16 17:42:25.591 +0800 debug: pan_auth_cache_user_is_allowed(pan_auth_cache_allowlist_n_grp.c:662): This is a single vsys platform, group check for allow list is performed on "vsys1"
2020-07-16 17:42:25.592 +0800 debug: _authenticate_by_localdb_or_remote_server(pan_auth_state_engine.c:1823): Authenticating user "mlxu" with <profile: "radius auth", vsys: "shared">
2020-07-16 17:42:25.592 +0800 debug: _retrieve_svr_ids(pan_auth_service.c:648): find auth server id vector for radius auth-shared
2020-07-16 17:42:25.602 +0800 debug: pan_authd_radius_create_req_payload(pan_authd_radius.c:230): username: mlxu
2020-07-16 17:42:25.604 +0800 debug: pan_make_radius_request_buf(pan_authd_radius_prot.c:383): RADIUS request type: CHAP
2020-07-16 17:42:25.624 +0800 debug: pan_authd_radius_parse_resp_payload(pan_authd_radius.c:285): resp_code = RAD_ACCESS_REJECT
2020-07-16 17:42:25.624 +0800 debug: pan_auth_service_recv_response(pan_auth_service_handle.c:1612): Got response for user: "mlxu"
2020-07-16 17:42:25.624 +0800 debug: pan_auth_response_process(pan_auth_state_engine.c:4290): auth status: auth failed
2020-07-16 17:42:25.625 +0800 debug: pan_auth_incr_failed_attempt(pan_authd_db.c:171): increase failed attempt for user: mlxu
2020-07-16 17:42:25.626 +0800 debug: pan_auth_response_process(pan_auth_state_engine.c:4469): Authentication failed: <profile: "radius auth", vsys: "shared", username "mlxu">
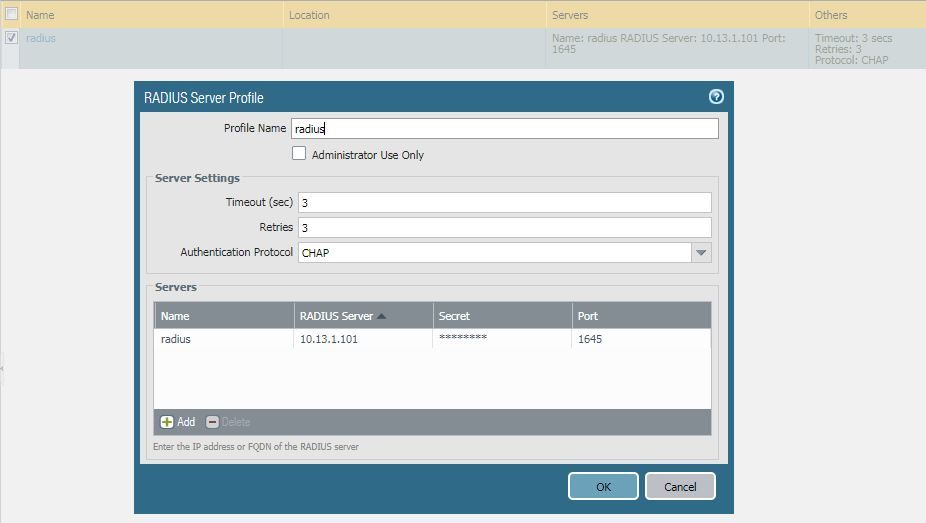
2020-07-16 17:42:25.641 +0800 failed authentication for user 'mlxu'. Reason: Invalid username/password. auth profile 'radius auth', vsys 'shared', server profile 'radius', server address '10.13.1.101', auth protocol 'CHAP', From: 10.33.73.121.
2020-07-16 17:42:25.641 +0800 debug: _log_auth_respone(pan_auth_server.c:268): Sent PAN_AUTH_FAILURE auth response for user 'mlxu' (exp_in_days=-1 (-1 never; 0 within a day))(authd_id: 6848127346889719896)
2020-07-16 17:42:25.642 +0800 debug: sysd_queue_wr_event_add(sysd_queue.c:915): QUEUE: queue write event already added
2020-07-16 17:42:34.768 +0800 debug: pan_auth_request_process(pan_auth_state_engine.c:3350): Receive request: msg type PAN_AUTH_REQ_REMOTE_INIT_AUTH, conv id 51, body length 2384
2020-07-16 17:42:34.768 +0800 debug: _authenticate_initial(pan_auth_state_engine.c:2377): Trying to authenticate (init auth): <profile: "", vsys: "", policy: "", username "mlxu"> ; timeout setting: 180 secs ; authd id: 6848127346889719897
2020-07-16 17:42:34.769 +0800 debug: _get_auth_prof_detail(pan_auth_util.c:1060): admin user thru WebUI "mlxu"
2020-07-16 17:42:34.769 +0800 debug: _get_admin_authentication_profile_by_name(pan_auth_util.c:554): Got auth prof "radius auth" for admin user "mlxu"
2020-07-16 17:42:34.769 +0800 debug: _get_auth_prof_detail(pan_auth_util.c:1081): admin user thru WebUI "mlxu" auth request without vsys: try "shared" any way
2020-07-16 17:42:34.769 +0800 debug: _get_authseq_profile(pan_auth_util.c:860): Auth profile/vsys (radius auth/shared) is NOT auth sequence
2020-07-16 17:42:34.769 +0800 debug: _retrieve_svr_ids(pan_auth_service.c:645): could not find auth server id vector for radius auth-shared-mfa
2020-07-16 17:42:34.770 +0800 debug: add_info_from_auth_profile_to_request(pan_auth_util.c:1024): MFA is not configured for the auth profile. No mfa server ids for the user "" (prof/vsys: radius auth/shared)
2020-07-16 17:42:34.770 +0800 debug: _authenticate_initial(pan_auth_state_engine.c:2566): Keep original username, i.e., whatever end-user typed, "mlxu" in request->username
2020-07-16 17:42:34.770 +0800 debug: pan_auth_cache_user_is_allowed(pan_auth_cache_allowlist_n_grp.c:662): This is a single vsys platform, group check for allow list is performed on "vsys1"
2020-07-16 17:42:34.771 +0800 debug: _authenticate_by_localdb_or_remote_server(pan_auth_state_engine.c:1823): Authenticating user "mlxu" with <profile: "radius auth", vsys: "shared">
2020-07-16 17:42:34.771 +0800 debug: _retrieve_svr_ids(pan_auth_service.c:648): find auth server id vector for radius auth-shared
2020-07-16 17:42:34.772 +0800 debug: pan_authd_radius_create_req_payload(pan_authd_radius.c:230): username: mlxu
2020-07-16 17:42:34.772 +0800 debug: pan_make_radius_request_buf(pan_authd_radius_prot.c:383): RADIUS request type: CHAP
2020-07-16 17:42:35.013 +0800 debug: pan_authd_radius_parse_resp_payload(pan_authd_radius.c:285): resp_code = RAD_ACCESS_REJECT
2020-07-16 17:42:35.013 +0800 debug: pan_auth_service_recv_response(pan_auth_service_handle.c:1612): Got response for user: "mlxu"
2020-07-16 17:42:35.013 +0800 debug: pan_auth_response_process(pan_auth_state_engine.c:4290): auth status: auth failed
2020-07-16 17:42:35.014 +0800 debug: pan_auth_incr_failed_attempt(pan_authd_db.c:171): increase failed attempt for user: mlxu
2020-07-16 17:42:35.015 +0800 debug: pan_auth_response_process(pan_auth_state_engine.c:4469): Authentication failed: <profile: "radius auth", vsys: "shared", username "mlxu">
2020-07-16 17:42:35.017 +0800 failed authentication for user 'mlxu'. Reason: Invalid username/password. auth profile 'radius auth', vsys 'shared', server profile 'radius', server address '10.13.1.101', auth protocol 'CHAP', From: 10.33.73.121.
2020-07-16 17:42:35.019 +0800 debug: _log_auth_respone(pan_auth_server.c:268): Sent PAN_AUTH_FAILURE auth response for user 'mlxu' (exp_in_days=-1 (-1 never; 0 within a day))(authd_id: 6848127346889719897)
2020-07-16 17:42:49.425 +0800 debug: pan_auth_request_process(pan_auth_state_engine.c:3350): Receive request: msg type PAN_AUTH_REQ_REMOTE_INIT_AUTH, conv id 52, body length 2384
- 4002 Views
- 1 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Global Protect Connectivity Issue in GlobalProtect Discussions
- Okta Verify window behind GP login window fix in GlobalProtect Discussions
- SilverFort compatibility with Panorama VM-Series in General Topics
- PA Global Protect in GlobalProtect Discussions
- [SOLVED] - NGFW The Connection To Global Protect On The IPads Times Out!! in GlobalProtect Discussions