- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Security policy not working with Group Mapping
- LIVEcommunity
- Discussions
- General Topics
- Security policy not working with Group Mapping
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-05-2019 06:03 PM - edited 02-05-2019 08:30 PM
I have configured LDAP group under Group Map settings.
I have added the ldap group there.
Then under security policy source user is any and under user i added that group name.
When i do sh user group list i see the group name and user ids under it.
when i try to reach the destination ip under that rule firewall denies that traffic.
Security rule
zone1 and destination is zone 2
I have enabled used id under zone 1
When i see deny in firewall i see my user id there
Any thoughts?
Help the community: Like helpful comments and mark solutions.
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-10-2019 09:05 AM
still working fine with user group
Help the community: Like helpful comments and mark solutions.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-05-2019 07:22 PM
@MP18 wrote:Traffic flow in firewall - zone1 then zone 2
Traffic has to come via Zone 1 to reach Zone2.
Security rule
zone 2 and destination is zone 3
Can you include a screenshot of the log and the security policy that you are talking about here? If I'm reading this correctly it sounds like what you are saying would make sense; if the security policy states traffic from 'zone 2' can reach 'zone 3' and then the log is identifying a source of 'zone 1' the policy shouldn't work for that traffic, as it doesn't match.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-05-2019 07:44 PM
Help the community: Like helpful comments and mark solutions.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-05-2019 07:46 PM - edited 02-05-2019 08:32 PM
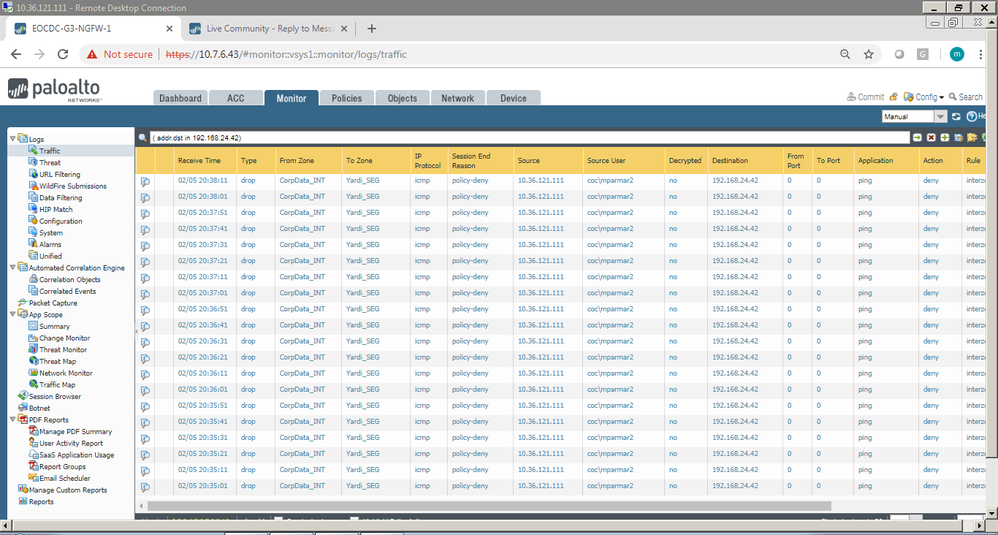
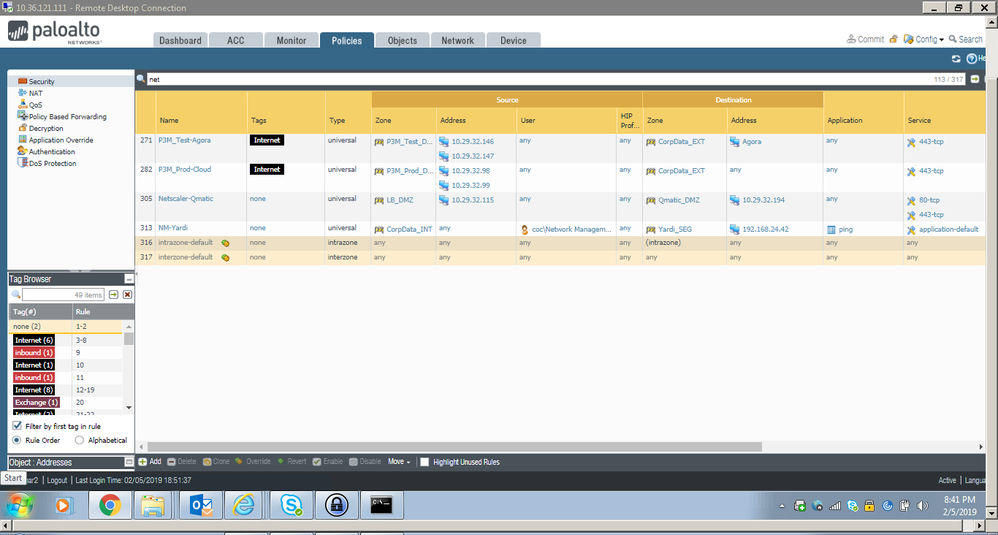
i have attached the screenshot.
same rule works fine if i just use my userd id instead of group name.
Also i have modified the traffic flow in earlier post sorry for that confusion.
Help the community: Like helpful comments and mark solutions.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-05-2019 08:05 PM
i tsested again by removing and adding the group name it worked now.
pretty strange behaviour sometimes it works and sometimes not
Help the community: Like helpful comments and mark solutions.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-06-2019 03:46 AM
Group-Mapping has default setting to poll the LDAP every 3600sec (one hour) to get the list of users for a given user group. I have seens lots of times when test user is put in the allowed user group on the AD and the user test his access immideately after that. But since the firewall is updating its information every hour, Palo Alto FW will not know that this user is already part the allowed group.
I am more interested in how do you optain the user id information? How do you perform the ip-to-user mapping, what is your source.
Other common issue I have seens is that ip-to-user mapping doesn't include the domain, while the user group-mapping does, and firewall again fail to match the user with the allowed user group.
Also what attribute are using to the username? For example user group-mapping is polling the UPN, but your ip-to-user mapping source is using CN
I would say a good start will be to compare the outpus from
> show user ip-user-mapping all
> show user group name <full-cn-of-the-allowed-group>
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-06-2019 04:48 AM - edited 02-06-2019 04:59 AM
For userid we are using user id agent running on windows.
So PA talk to those user id agents and get the mapping.
for group mapping we use ldap also we use domain name with it
I have already run those commands and not much i can find in them
idle timeout for user id agent is 4 hours.
In group mappings i see update interval to default ?
should i increase the value here to like 4 hours?
Help the community: Like helpful comments and mark solutions.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-07-2019 08:33 PM
Nothing is changed in the config.
Group mapping is working fine from last 3 days
Help the community: Like helpful comments and mark solutions.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-10-2019 09:05 AM
still working fine with user group
Help the community: Like helpful comments and mark solutions.
- 1 accepted solution
- 11839 Views
- 8 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- GlobalProtect Name Normalization issue in GlobalProtect Discussions
- Azure to OnPrem Connectivity issue in Next-Generation Firewall Discussions
- Decryption suddenly failed for all Webpages using Sectigo Certs in General Topics
- Prisma Access CIE and User-ID mapping not working for groups in Prisma Access Discussions
- GRPC status UNAVAILABLE in intelligent offload in VM-Series in the Private Cloud