- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
SSL Decrypt on Virtual Wire deployment Certificate Issue (Chrome)
- LIVEcommunity
- Discussions
- General Topics
- SSL Decrypt on Virtual Wire deployment Certificate Issue (Chrome)
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
SSL Decrypt on Virtual Wire deployment Certificate Issue (Chrome)
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-25-2020 03:45 PM
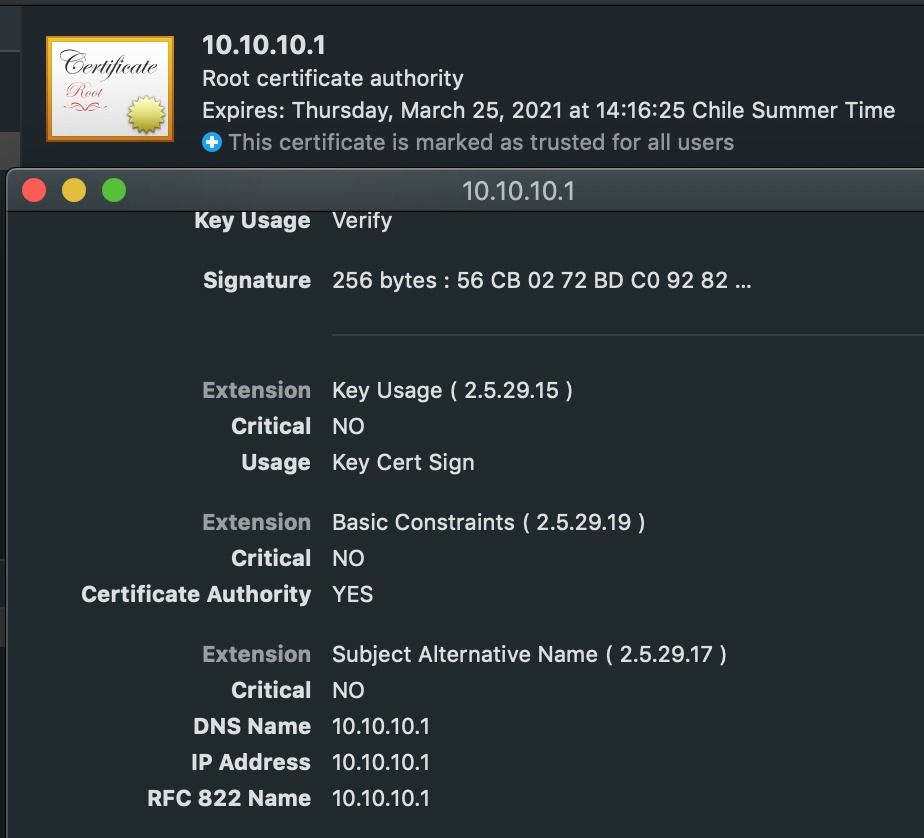
I have my PA-200 on virtual wire mode with Captive Portal using SSL Decrypt for all users with Self Signed Certificate.
When the users try to navigate on crhrome browser to internet they receive NET::ERR_CERT_COMMON_NAME_INVALID that doesn't permit to bypass for go to untrust site. When i manually enter a site that support http or another certificate method, is possible to navigate to the the unsafe site and Captive Portal works very well (Also I have Decryption profile and it also works)
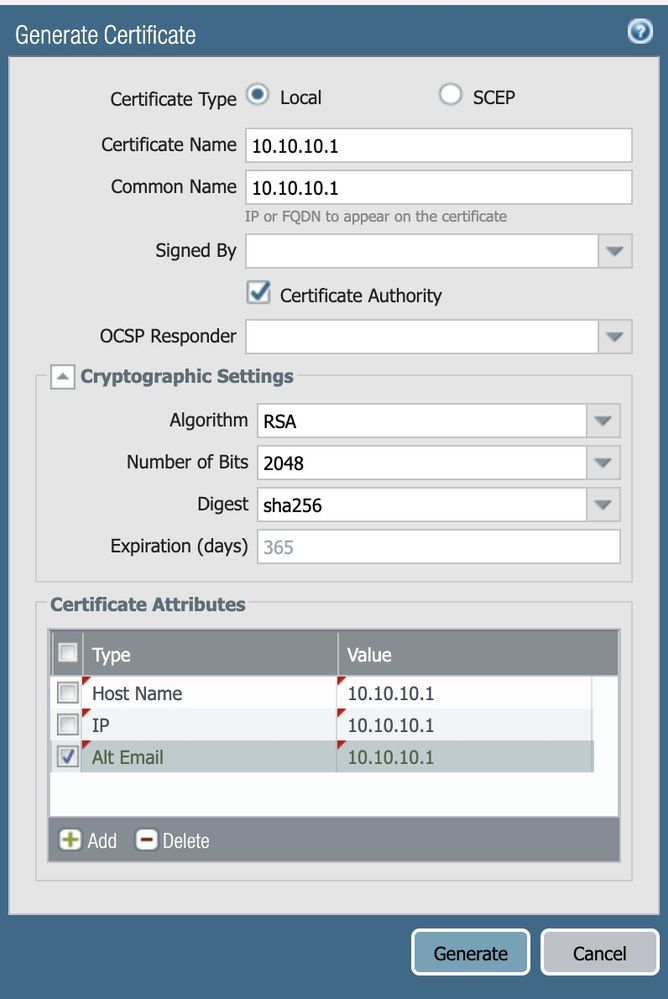
I read that it is common issue on Google, So I manually put a Subject Alternate name on attributes (host, ip, alt-email) to the Certificate, after export to the PC user like a root trust certificate but it doesn't works
On my case, all trust users takes DHCP IPs of the Router above the FW so default gateway is the router IP (virtual wire doesn't provide a FW IP) . I manually generate a certificate with the router IP but still doesn't works 😞
Any Idea or suggestion?
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-02-2020 08:06 AM
So, to confirm, you are able to get SSL Decryption working on your firewall with some sites?
The only way the SSL Decryption can work properly if the Firewall is the CA, and it generates SSL certificates on the fly for the client machine, in a "man in the middle" function. That CA (Certificate Authority) then is trusted by the client machine, allowing the traffic coming from the Firewall to be trusted, and the Firewall acts as the client to the Public site.
But this gets really muddy, really fast when the firewall is in VirtualWire mode with no IP.
Stay Secure,
Joe
Don't forget to Like items if a post is helpful to you!
- 3728 Views
- 1 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- GRPC status UNAVAILABLE in intelligent offload in VM-Series in the Private Cloud
- How does the Azure Virtual Network discovers that there is Palo Alto Gateway Interface in VM-Series in the Public Cloud
- Error log ": MLAV Server certificate validation failed. " received in Next-Generation Firewall Discussions
- Unable to reach Palo Alto - Global Protect Portal. in GlobalProtect Discussions
- Newsletter: Cloud Delivered Security Services, Oct-2025 in Advanced Threat Prevention Discussions