- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
SSL Decryption not working with Policy based forwarding
- LIVEcommunity
- Discussions
- General Topics
- Re: SSL Decryption not working with Policy based forwarding
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
SSL Decryption not working with Policy based forwarding
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-24-2019 04:24 AM - edited 01-24-2019 04:25 AM
I have configured SSL decryption with one ISP which is configured via default route and it is working fine. I have another ISP and I configured to forward internet traffic from particular endpoints (same trust zone) to 2nd ISP, for this purpose i created NAT and a PBF rule for those particular endpoints, scenario was working fine till now.
I want decrypt the outgoing internet traffic of 2nd ISP users as well, i created another decryption rule for those users by mentioning destination zone of 2nd ISP, but there is SSL error on end points.
Please help me in this regard.
Shuaib Khalid
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-24-2019 06:37 AM
Hey @Shuaib_Khalid,
The SSL error implies that the client is successfully getting decrypted but they aren't trusting the "Forward Trust" certificate that the firewall is presenting it.
Q1 - Where did you obtain the certificate from? Was it from Active Directory Certificate Server (or PKI equivalent) or self-signed on the firewall?
Q2 If from PKI, is the machine part of the domain, and have you pushed out this cert to "Trusted Root Certification Authorities" folder via GPO?
If self-signed, the certificate needs to be installed again in the Trusted Root Certification Authorities folder for the local machine.
Q3 - If the certificate marked as CA? Certificate authority?
Cheers,
Luke.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-25-2019 04:58 AM
Hi Luke,
Thank for responding on the query, below are answers of your questions.
Q1 - Where did you obtain the certificate from? Was it from Active Directory Certificate Server (or PKI equivalent) or self-signed on the firewall?
Ans: Certificate is self singed generated from Palo Alto
Q2 If from PKI, is the machine part of the domain, and have you pushed out this cert to "Trusted Root Certification Authorities" folder via GPO?
Ans: I have manually imported the certificate on testing machines in Trusted Root of all browsers
If self-signed, the certificate needs to be installed again in the Trusted Root Certification Authorities folder for the local machine.
Q3 - If the certificate marked as CA? Certificate authority?
Ans: Yes, the certificate is marked as CA.
When i put testing machin on ISP 1 there no certificate error, decryption is succesfull and i got proper application detection but when i put the same machine on ISP 2 it gives SSL error.
Some Important points:
I have one SSL certificate on the firewall and two decryption policies for ISP1 and ISP2 users.
ISP1 is configured with default route while traffic is forwarding to ISP via PBF
Both ISPs are in different untrust zones
Source Zone is same
If i disable SSL decryption policy for ISP2 then browsing was succesfull
Any guess??
Shuaib Khalid
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-25-2019 05:09 AM
Can you take a screenshot of the certificate message you are getting? Is it something like Unknown Certificate authority?
If you then click the padlock in chrome -> certificate -> certification path. Are any certificate(s) in this path showing as red X?
That would mean they are not imported into the Trusted Root CA Store.
PBF should not break forward proxy.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-28-2019 06:23 AM
Shuaib Khalid
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-28-2019 06:26 AM
Hi Luke,
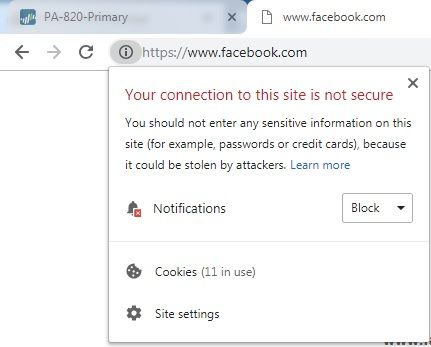
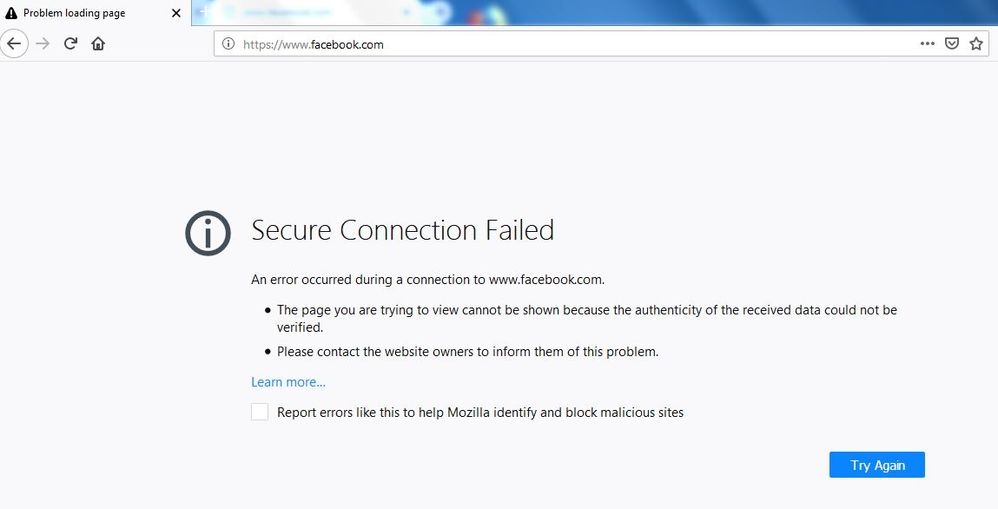
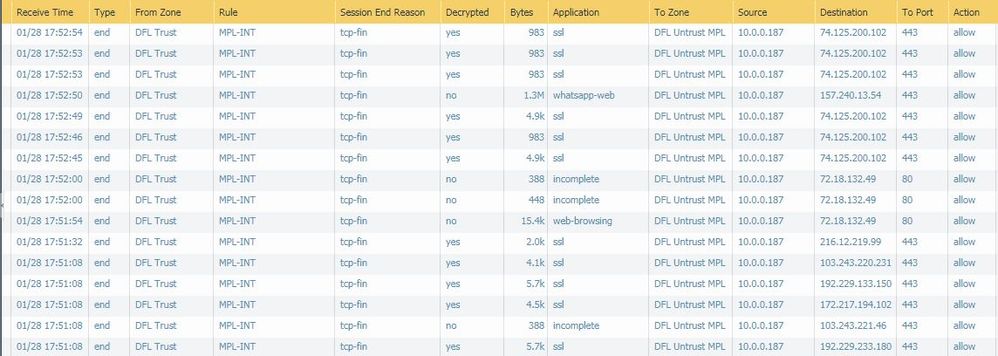
Appologize for delayed response, i have attached some screenshots in above message mentioning the SSL error in Chrome & Firefox, i have also attached traffic logs for ISP1 (Succesfull Decryption) and ISP2 (Unsuccesfull Decryption).
Note: Non SSL sites are working fine on ISP2.
Shuaib Khalid
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-28-2019 06:28 AM
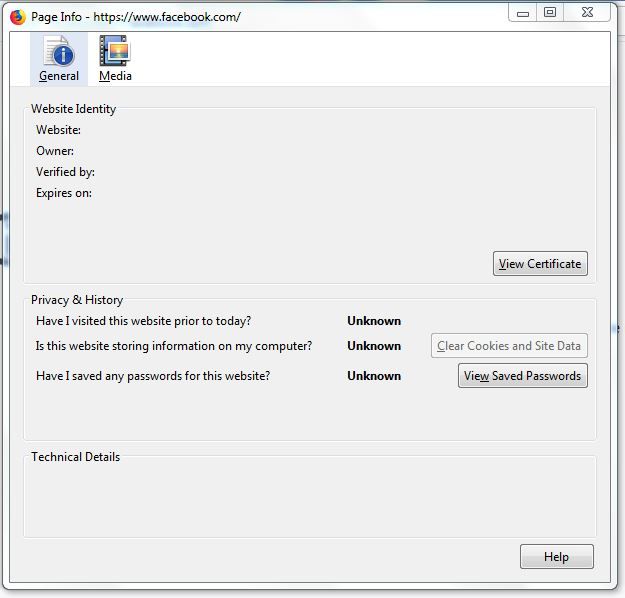
What do you see if anything, when you click on "View Certificate" ?
Regards ... Leslie
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-28-2019 07:00 AM
Nothing happens on clicking "View Certificate".
Shuaib Khalid
- 5487 Views
- 7 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- "More runtime stats" not loading when Advanced routing is enabled in Next-Generation Firewall Discussions
- PA-415-5G not working with fresh T-Mobile SIM in General Topics
- DHCP Relay over SDWAN issue in Advanced SD-WAN for NGFW Discussions
- Log forwarding from Cloud NGFW in Azure to Log Analytics Workspace for Sentinel in VM-Series in the Public Cloud
- Not able to log XFF (Actual Client IP) in PaloAlto Logs even when we enable XFF and URL filtering profile in Palo's in Next-Generation Firewall Discussions