- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
SSL Decryption
- LIVEcommunity
- Discussions
- General Topics
- Re: SSL Decryption
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
SSL Decryption
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-04-2019 03:17 AM
Hi guys,
Nowadays I am playing with a PA-VM (no license) and decryption policy. Basically there are many articles and that explain how Decryption policy works and how to set it up. I have checked and double checked my setting and I cannot make facebook.com for instance work when I enable the Decryption.
Here are the rules:
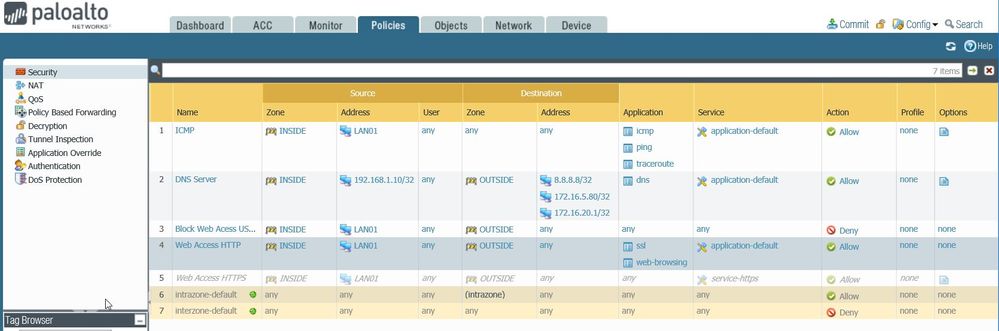
Cheers
Danilo
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-12-2019 12:06 PM
@SShnap wrote:
> I think they should release an application list update, which add working port 443 for web-browsing application.
>
> I also notice that once you decrypt traffic on 443-SSL it becomes 443-web-browsing, so policy rule that allow web-browsing on application-default will not work, because the application-default is 80.
>
> You need to create another policy to allow web-browsing application on 443 port.
I had to hold my tongue (well, fingers) because 9.0 hadn't been released yet, but now that it is available I can share this:
Now, in PAN-OS 9.0, if an application has a known secure port like web-browsing, your app-based allow rule will work with application-default when decrypting. Currently the app list is web-browsing, SMTP, FTP, LDAP, POP3, and IMAP. Palo Alto Networks can update that list as well via a content update.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-12-2019 01:28 PM
@gwesson Do not hold your fingers. 🙂
Great news! Tks
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-13-2019 12:34 AM
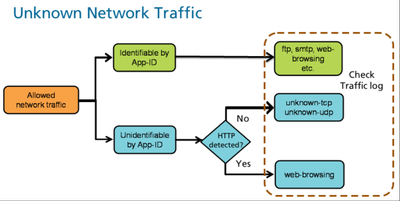
The web-browsing application is like last resort application. web-browsing will be used only if the firewall fail to match any other application, while the traffic contain HTTP protocol. See below:
Palo Alto firewall will match facebook application even if the traffic is not decrypted (in my personal limited observations), so I am guessing it is using the SNI from the server certificate. Without decryption the firewall will may fail to match the more specfic facebook apps, but it still will know that it is facebook related.
Same goes for google, dropbox, twitter and many more well known services that Palo Alto has create application for it.
- 13707 Views
- 18 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Prisma Access Explicit Proxy — Anti‑Spyware behavior when DNS bypasses Prisma (logging subtype + test methodology) in Prisma Access Discussions
- Unable to block download and upload for chatgpt and messengers in Next-Generation Firewall Discussions
- Decryption suddenly failed for all Webpages using Sectigo Certs in General Topics
- Chatgpt enteprise login only in Next-Generation Firewall Discussions
- web file blocking in Next-Generation Firewall Discussions