- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Suspicious DNS Query - conficker
- LIVEcommunity
- Discussions
- General Topics
- Suspicious DNS Query - conficker
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Suspicious DNS Query - conficker
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-21-2013 12:26 PM
Hey,
Is there a way for not letting conficker fill up the threat logs? Or an easy way to filter them out? I have 1000+ logs from 1 host on just a few hours and it is getting hard to see the other threats... Even in the ACC, I get a list full of conficker, nothing else. This is caused by every conficker URL being identified as a different threat ID.
Kind regards,
Bob
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-21-2013 01:23 PM
Hi,
You can use the anti-spyware profile and add the exception for DNS queries not to be populated in the threat logs by choosing the action allow.
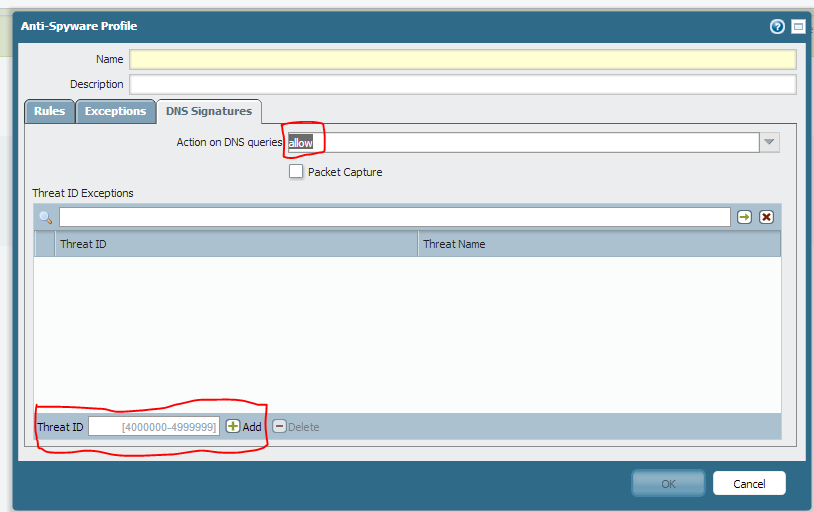
Associate the profile to the rule which the traffic is hitting.
Thanks,
Syed R Hasnain
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-21-2013 02:23 PM
So I would need to create a new rule above the one that allows it at the moment with source IP the infected clients (otherwise I would not know when other clients have it)?
Also, the conficker threat has a lot of threat ID's, so setting all DNS queries to all would make other threats not show up in the logs?
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-21-2013 03:27 PM
Hello,
Yes, you need to create a new rule above the one that allows it currently in order to apply the anti-spyware profile .
Below mentioned discussion may help you
Suspicious DNS Query - how to find source computer?
Thanks
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-21-2013 05:00 PM
Hi,
You can use individual threat IDS and add them in the exception and set the action for them as allow as shown above in the snap shot..So in this way you will not be doing for all the threats but just for some individuals not to be populated in the threat logs.
Thanks,
Syed R Hasnain
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-26-2013 10:59 PM
Using individual threat ID'is is not an option I believe, since conficker seems to have a lot of different threat ID's. I was trying to filter them out of my threat logs but after removing 20-30 of them, there were still a lot more that needed to be filtered out.
It seems there is no reasonable way to "group" the conficker threat and filter it out.
Since conficker uses a generic url and PA creates a different ID for each of them, the exception list would grow rapidly every day. I am not sure about this, but it seems logical.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-27-2013 07:42 AM
Hmmm, sorry, but disconnecting the affected system from the network and cleaning it is what I would consider the right approach..... And as a side effect the log entries will go away....
We are talking IT security right 🙂 ?
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-30-2013 12:04 AM
This was indeed the first thing that came to my mind, but in our case, hosts in the guest network are not controlled by our IT team.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-30-2013 02:23 AM
Just for clarification. You are not responsible for the guest network, but the traffic from the guest network is traversing your firewall ?
I would never allow a guest which is malware infected to use my network or traverse my firewall.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-30-2013 03:17 AM
The traffic is in an isolated vlan which can only access the internet, not other internal subnets. A strict policy is in place to ensure this. I see no reason why this network should not be behind the main firewall.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-30-2013 03:22 AM
Of course you should filter these clients aswell but one reason (to use a dedicated firewall for these clients that is) is to avoid a DDoS situation (from an infected client connected to this guest network).
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-30-2013 06:26 AM
gafrol: you have no idea where he works or what kind of network he's on. This is a common thing at universities, for example. The IT team isn't allowed to ride in on their high horse and grab a laptop, the most they can do is advise a student that they're infected.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-30-2013 06:58 AM
Even if it's a university, what could be against blocking malware traffic at the firewall level ?
I have made first hand experience with a university in Europe being disconnected from their Internet Link by the provider due to outbound malware traffic coming from the universities IP's....
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-02-2013 08:02 PM
I had this issue a year ago and it was a pain to see logs filled with conficker. The way i resolved this matter is by blocking .dll files. After i did that i haven't seen any conficker on my logs.
- 7328 Views
- 13 replies
- 1 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- How to escape a wildcard (*) in Cortex XDR Discussions
- Toutrial: Detecting Tor Traffic in XSIAM in Cortex XDR Discussions
- DNS sinkhole , some questions in General Topics
- RQL Query to search for suspicious activity on specific S3 Bucket in Prisma Cloud Discussions
- DNS Signatures in Advanced Threat Prevention Discussions



