- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
TI automation - architecture and hardening [part 1]
- LIVEcommunity
- Discussions
- General Topics
- Re: [HOWTO] Threat Intelligence Automation - MineMeld architecture and hardening
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
TI automation - architecture and hardening [part 1]
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-03-2017 04:25 AM - edited 08-31-2017 05:56 AM
Hi everyone,
I'm Giovanni Mellini and I work in ENAV (Italian Air Traffic Control provider) Security dept.
One of the topics I've been working on over the last few months is threat intelligence automation, or how to automatically integrate threat intelligence feeds into our near-real-time Information Security Operation Center SOC Splunk engine to reduce the time spent by SOC security analysts on IOC analysis.
I found in MineMeld the solution; MineMeld helped me to solve the challenges I had in the past while playing with IOC coming from various threat intelligence sources: collection automation, unduplication, aging and SOC integration.
I wrote a blog post - the first of a series I want to write- about the architecture design and hardening of MineMeld to:
- collect feeds from external sources
- make available the feeds to trusted sources (internal and external)
- put data collected into our SOC near-real-time engine built on top of Splunk
Hope this can be an useful resource for anyone like me is trying to be effective on TI automation.
Many tks again to Luigi Mori for its continued support.
Ciao
Giovanni
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-07-2017 10:35 PM
Thank you, I am looking forward to reading your next posts.
<<In the next posts I will cover:
- setup of the miners: STIX/TAXXI, MISP, csv etc;
- feeds export in csv format and SPLUNK integration;
- feeds export in TAXII format.>>
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-11-2017 08:13 AM
Topic covered: how I built the foundation of near-real-time integration of MineMeld with our Information Security Operation Center (i-SOC) custom SPLUNK application
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-14-2017 10:01 PM
HTTPS Configurations
Configure the server to disable support for 3DES suite & Disable insecure TLS/SSL protocol support (TLSv1)
$sudo vi /etc/nginx/sites-enabled/minemeld-web
ssl_protocols TLSv1.1 TLSv1.2;
ssl_ciphers 'ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES256-GCM-SHA384:DHE-RSA-AES128-GCM-SHA256:DHE-DSS-AES128-GCM-SHA256:kEDH+AESGCM:ECDHE-RSA-AES128-SHA256:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA:ECDHE-ECDSA-AES128-SHA:ECDHE-RSA-AES256-SHA384:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA:ECDHE-ECDSA-AES256-SHA:DHE-RSA-AES128-SHA256:DHE-RSA-AES128-SHA:DHE-DSS-AES128-SHA256:DHE-RSA-AES256-SHA256:DHE-DSS-AES256-SHA:DHE-RSA-AES256-SHA:!aNULL:!eNULL:!EXPORT:!DES:!RC4:!3DES:!MD5:!PSK';
$sudo sudo -u minemeld mm-supervisorctl restart minemeld-web
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-14-2017 10:46 PM
Tks for the config, I will test and update the post
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-14-2017 11:06 PM
@iThreatHunt wrote:
HTTPS Configurations
Configure the server to disable support for 3DES suite & Disable insecure TLS/SSL protocol support (TLSv1)
$sudo vi /etc/nginx/sites-enabled/minemeld-web
ssl_protocols TLSv1.1 TLSv1.2;
ssl_ciphers 'ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES256-GCM-SHA384:DHE-RSA-AES128-GCM-SHA256:DHE-DSS-AES128-GCM-SHA256:kEDH+AESGCM:ECDHE-RSA-AES128-SHA256:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA:ECDHE-ECDSA-AES128-SHA:ECDHE-RSA-AES256-SHA384:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA:ECDHE-ECDSA-AES256-SHA:DHE-RSA-AES128-SHA256:DHE-RSA-AES128-SHA:DHE-DSS-AES128-SHA256:DHE-RSA-AES256-SHA256:DHE-DSS-AES256-SHA:DHE-RSA-AES256-SHA:!aNULL:!eNULL:!EXPORT:!DES:!RC4:!3DES:!MD5:!PSK';
$sudo sudo -u minemeld mm-supervisorctl restart minemeld-web
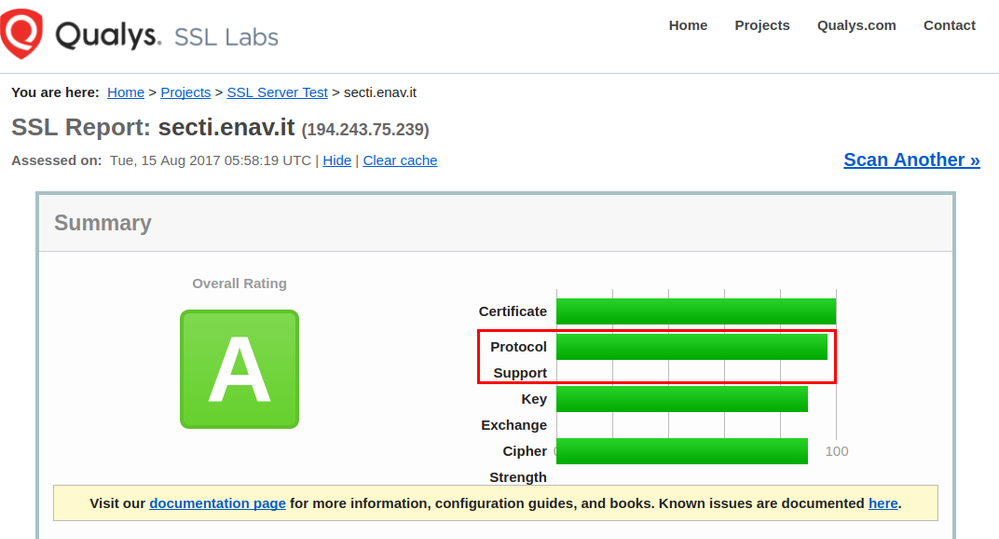
After applying your config I can get a little better rate on https://www.ssllabs.com test for "Protocol Support" because TLS 1.0 is disabled (note that the test don't say that TLS 1.0 is insecure).
Disabling 3DES disable the only one cipher suite considered WEAK, TLS_RSA_WITH_3DES_EDE_CBC_SHA (0xa). Great catch, to be honest I tried without success to find the right config. SO tks
Last note.
To apply the new config on nginx the following command don't works
$sudo sudo -u minemeld mm-supervisorctl restart minemeld-web
You need to restart the service nginx
# service nginx restart
Tks, I update my blog post
Giovanni
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-14-2017 11:33 PM
Oh, I am sorry. I think mimemeld-web services.
Thanks for correct command.
@soc_enav wrote:
@iThreatHunt wrote:
HTTPS Configurations
Configure the server to disable support for 3DES suite & Disable insecure TLS/SSL protocol support (TLSv1)
$sudo vi /etc/nginx/sites-enabled/minemeld-web
ssl_protocols TLSv1.1 TLSv1.2;
ssl_ciphers 'ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES256-GCM-SHA384:DHE-RSA-AES128-GCM-SHA256:DHE-DSS-AES128-GCM-SHA256:kEDH+AESGCM:ECDHE-RSA-AES128-SHA256:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA:ECDHE-ECDSA-AES128-SHA:ECDHE-RSA-AES256-SHA384:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA:ECDHE-ECDSA-AES256-SHA:DHE-RSA-AES128-SHA256:DHE-RSA-AES128-SHA:DHE-DSS-AES128-SHA256:DHE-RSA-AES256-SHA256:DHE-DSS-AES256-SHA:DHE-RSA-AES256-SHA:!aNULL:!eNULL:!EXPORT:!DES:!RC4:!3DES:!MD5:!PSK';
$sudo sudo -u minemeld mm-supervisorctl restart minemeld-web
After applying your config I can get a little better rate on https://www.ssllabs.com test for "Protocol Support" because TLS 1.0 is disabled (note that the test don't say that TLS 1.0 is insecure).
Disabling 3DES disable the only one cipher suite considered WEAK, TLS_RSA_WITH_3DES_EDE_CBC_SHA (
0xa). Great catch, to be honest I tried without success to find the right config. SO tks
Last note.
To apply the new config on nginx the following command don't works
$sudo sudo -u minemeld mm-supervisorctl restart minemeld-web
You need to restart the service nginx
# service nginx restart
Tks, I update my blog post
Giovanni
- 18522 Views
- 8 replies
- 3 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Building Cybersecurity Strategies: A Game of Digital Mahjong in General Topics
- After pushing content from Dev to Prod, we are seeing lot of errors in XSOAR in Cortex XSOAR Discussions
- Threat Vector, a Unit 42 Podcast, is Now on LIVEcommunity! in General Topics
- Join the Fuel User Spark Event on March 19: Dealing with Threats ! in General Topics
- AWS Reference Architecture, Subnet Sizes and Automation in VM-Series in the Public Cloud