- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Troubleshooting User-ID from syslog listener
- LIVEcommunity
- Discussions
- General Topics
- Re: Troubleshooting User-ID from syslog listener
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Troubleshooting User-ID from syslog listener
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-08-2017 02:53 PM
I've configured my 5050's to be Syslog Listeners for a couple sources so that I can parse User-ID information out of them. I did so following this document here. I can see via the command
show user server-monitor state XXX
that I am receiving log messages, but so far none of the are registering "success messages". I'm having a hell of a time getting a packet capture to show the inbound Syslog messages so I can inspect that I am getting what I expect. Both pcap from the gui and tcpdump from the CLI isn't showing anything. Is there a way to just simply tail the underlying syslog file on the local 5050 to see what it is receiving?
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-08-2017 03:27 PM - edited 06-08-2017 03:28 PM
Hi,
We had Captive Portal issue recently, and palo was configured as syslog listener. TAC was doing a pcap from GUI in order to confirm the format of the syslog messages. So you are on the right way. Did you configure your syslog server to forward the syslogsto to palo, did you check if you can reach palo successfully from the syslog server? I believe your mgmt profile is attached to the correct interface with syslog options ticked.
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-08-2017 05:39 PM
Hi Geoff,
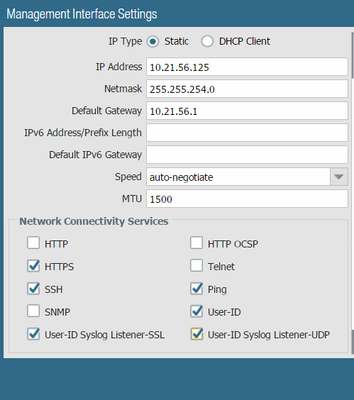
Have you enabled syslog listener on the management profile?
Once you have that committed, you are sure to receive SYSLOG packets in tcpdump. Maybe check/remove any filter you got while taking a tcpdump.
Run the following commands and check logs.
admin@anuragFW> debug user-id on debug
admin@anuragFW> debug user-id set userid syslog
admin@anuragFW> tail follow yes mp-log useridd.log
Then, to verify your regex/filter expression use the following commands:
admin@anuragFW> test user-id user-id-syslog-parse regex-identifier event-regex <value> username-regex <value> address-regex <value> log-string <value>
admin@anuragFW> test user-id user-id-syslog-parse field-identifier event-string <value> username-prefix <value> username-delimiter <value> address-prefix <value> address-delimiter <value> log-string <value
If you are having trouble figuring out which regex is not being read correctly, feed the log-string values different sections of syslog messages. That's just something you gotta play around and figure out. Some special characters need to be escaped while some will not be allowed.
You can post a sample of syslog messages and we could possibly look into it.
Hope this helps.
Regards,
Anurag
ACE 7.0, 8.0, PCNSE 7
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-11-2019 12:40 PM
@ansharma wrote:Then, to verify your regex/filter expression use the following commands:
admin@anuragFW> test user-id user-id-syslog-parse regex-identifier event-regex <value> username-regex <value> address-regex <value> log-string <value>
admin@anuragFW> test user-id user-id-syslog-parse field-identifier event-string <value> username-prefix <value> username-delimiter <value> address-prefix <value> address-delimiter <value> log-string <value
If you are having trouble figuring out which regex is not being read correctly, feed the log-string values different sections of syslog messages. That's just something you gotta play around and figure out. Some special characters need to be escaped while some will not be allowed.
Thank you! Those "test user-id" commands were exactly what I've been searching for. Trying to get a custom syslog filter working has been a pain, especially since the online regex tools say they work, but there's no logs on the PA200 to check if it's working or not.
You saved me a lot of desk-head interactions today. 😄
- 8494 Views
- 3 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- UserID mapping flags user unknown with single digit timeout secs in Next-Generation Firewall Discussions
- SYSLOG Issue after upgrade in General Topics
- After pushing content from Dev to Prod, we are seeing lot of errors in XSOAR in Cortex XSOAR Discussions
- Logging In PAN OS in General Topics
- DTRH: CIS Benchmarking - 3rd Party Data Ingestion | Data Parsing | Widgets & Dashboards in Cortex XDR Discussions