- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
URL Filtering - How does it work exactly with Service interaction
- LIVEcommunity
- Discussions
- General Topics
- Re: URL Filtering - How does it work exactly with Service interaction
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-03-2019 05:08 PM
So let me start here fundementally all I'm trying to do is something like "Computer Y can access MS updates and nothing else" and my three pointers were:
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000ClbvCAC
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000ClHXCA0
Also as an asside let me say 1) i really hate how often PA KB's conflict each other or do things differently, i.e. is it really that hard to deconflict (i.e. check the URI's listed; yes I understand somebody just went * for one of them) and 2) Why people never do anything in Panorama as it makes following examples / screenshots a PITA; like simpy show/list both ways.
Anyways generally speaking what I want to know, and a search didn't really say anything, is exactly when does URL filtering kick in. Does it kick in after a Service="ssl" or Service="web-browsing" match? Does it kick in regadless of service context the first time it thinks it sees HTTP (or HTTPS)? Basically what is the interaction between "service" and "URL categories". For example if I say "service=web-browing deny; URL Catgory=allow list google.com" does it still let me to google? If say "service=webex allow; URL Category=webex_category deny" does it allow webex.com or not? The specific interaction between those two times when licensed for both is pretty unclear to include OOP. What if I HTTP to a non-standard port, does URL filtering still kick in if it sees HTTP on port 48123? etc. Like I get the context of URL filtering IF service=web-browing (or service=ssl) when they are complimentary but not when it's they are dependency services or the OOP interactions when they conflict.
Fundementally in Panorama (to the point) I assume I'm just making a rule that says "allow service=web-browsing/ssl; block-categories all (67) allow list *.microsoft.com" which should work as long service doens't override it. Either way documentation on this could be clearer.
Lastly (since I'm here) do you EVER have to update the PAN-DB URL FIltering database (Device->licenses) or is this just a one time thing when you first activate your license never to have to do it again until it expires or you wipe the box? It's the only license with an active/download status field hence I've always wondered on that given I can always 'download now' which I find odd as it suggetts it's something you may need to occasionally do but at the same time, it's not a dynamic update. I assume it just autoupdates somehow or it queries real time? LIke I've never understood on teh URL filtering side how those updates are handled.
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-03-2019 07:05 PM
Here you go.
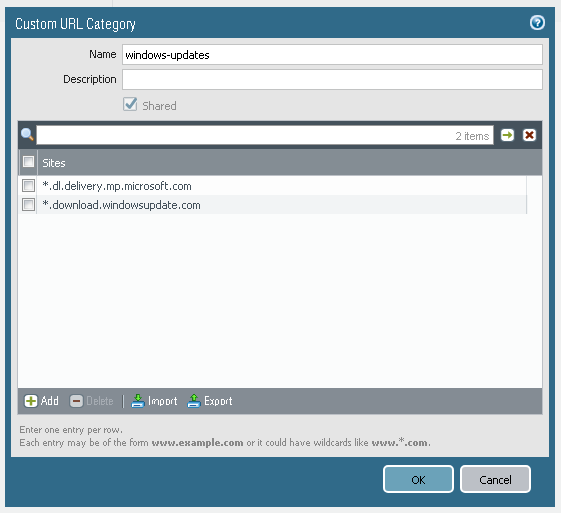
Ruleset that permits Windows Updates.
PANDB download now button will download seed file.
All other updates are dynamic. You do it only once.
Palo Alto Networks certified from 2011
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-03-2019 07:05 PM
Here you go.
Ruleset that permits Windows Updates.
PANDB download now button will download seed file.
All other updates are dynamic. You do it only once.
Palo Alto Networks certified from 2011
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-03-2019 08:54 PM
Will test it out tomorrow and cool as a practical matter but any ideas or can point a doc that explains the interaction and OOP between services and url filtering or hell how URL filtering even works in details .. would help with other issues down the road I think.
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-04-2019 07:25 AM
You mention service many times and then refer to web-browsing or ssl.
I think you mix up with application.
Because service column specifies regular tcp or udp port. Regular Layer 4.
In my example top rule permits traffic if application is identified as ms-update.
Palo always tries to identify application based on signature or heuristics.
If application signature does not identify this traffic as ms-update then second rule will permit web-browsing or ssl on their regular port (application-default) if it is going to URLs that are specified in custom url category called windows-updates.
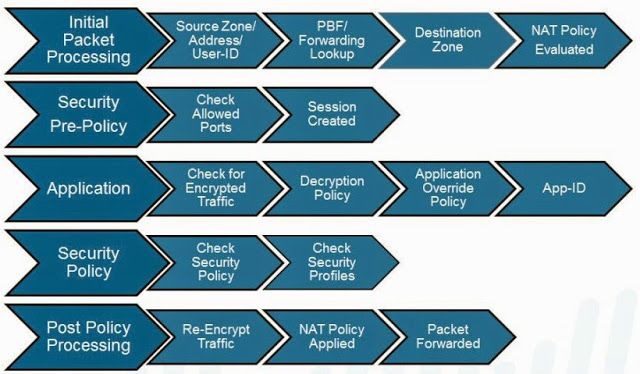
Simple packet flow in Palo
And detailed packet flow
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000ClVHCA0
Palo Alto Networks certified from 2011
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-04-2019 07:28 AM
web-browsing traffic:
SYN
SYN-ACK
ACK
HTTP GET - Palo get's URL and checks the category.
Server sends back website - Palo shifts application from insufficient-data to web-browsing
In case of SSL URL is received from data on certificate. So if cert says *.google.com Palo can't identify if user went to mail.google.com or maps.google.com
To get detailed URL categorization you need to decrypt SSL.
https://urlfiltering.paloaltonetworks.com/query/
Palo Alto Networks certified from 2011
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-04-2019 08:51 PM
Thanks for great explanation!
Help the community: Like helpful comments and mark solutions.
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-11-2019 05:26 PM
So I'm reading that but not groking the flow exactly even the detailed one. Let me walk you through where my brain is going and ask you clarify:
On your first rule it would seem to me that it would allow the source to access the entire web as well including non-MS updates since "web-browsing" is an implicit dependencie of ms-updates (show predefined application ms-update) though I'm not going to lie, my brain has had a hard time groking implicity-use and use applications when it comes to rule evaluation. So my source going to playboy.com would be allowed I assume because of the URL filter "any" coupled with the implicit-use web-browsing for the ms-update application-id, i.e. I feel you still need the the URL filter rule even w/ application=ms-update because of that.
Lets take that a step farther, lets say rule1 = "deny application=ms-update url=windows-update" and rule2 = "allow application=ms-update url=any", in that scenario which rule triggers if I send ms-update to "ninja.com"? Does rule1 trigger because ms-update ignores URL categories regardless of implicit-use so denies it simply based applicatoin-id or does rule2 trigger because implicit-use will get it past rule1?
What I'm trying to figure out (and I can't tell even from the detailed) is the interaction between URL category and application, i.e. are they treated independent of each other (i.e. can I use a URL category w/ app-id SSH for example to block a FQDN) or is URL category a subdependency ONLY of the single application web-browsing and use with any other application (even implicity-use) ignores it.
- 1 accepted solution
- 10201 Views
- 6 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- URL Category Change Request for www.intusjuntsparlament.com in General Topics
- Why do the same Windows Server data collected using XDRC and WEC agents show different statuses in the following fields? in Cortex XSIAM Discussions
- Excel downloads being blocked in General Topics
- Questions Regarding Output Difference in "show ctd-agent status security-client" Command in General Topics
- Please tell me about the new feature "BGP Filtering and Route Metric Support for Prisma Access" in Prisma Access 6.0. in Prisma Access Discussions