- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Using application-default with application override
- LIVEcommunity
- Discussions
- General Topics
- Re: Using application-default with application override
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-28-2013 02:26 PM
According to product help for application-default: The selected applications are allowed or denied only on their default ports defined by Palo Alto Networks. This option is recommended for allow policies because it prevents applications from running on unusual ports and protocols, which if not intentional, can be a sign of undesired application behavior and usage. Note that when you use this option, the device still checks for all applications on all ports, but with this configuration, applications are only allowed on their default ports/protocols.
When I use an application override rule, can I still use application-default or do I need to use ANY?
- Labels:
-
App-ID
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-29-2013 07:16 AM
Generally speaking, "Application Override" is a tool you can use to override what application the firewall detects. In your case here, the firewall is already detecting the application properly as AS2, so you don't need to use an Application Override. Keep in mind that all of Palo Alto's "AppIDs" are running on all ports at all times - so it has the ability to detect the AS2 application even on port 5060.
However, if you create a rule that says "permit outbound AS2 on application-default", that won't work because you're running this application on a non-standard port. Your suggestion of creating a security policy rule that permits application AS2 on a custom service port (5060) are correct. That would achieve what you're looking for - allowing AS2 on port 5060 and nothing more.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-28-2013 02:32 PM
When you create a custom application you can also specify the default ports that the application will use. When you create or modify a custom application navigate to the Advanced tab and under the Defaults section you can define the default port definitions.
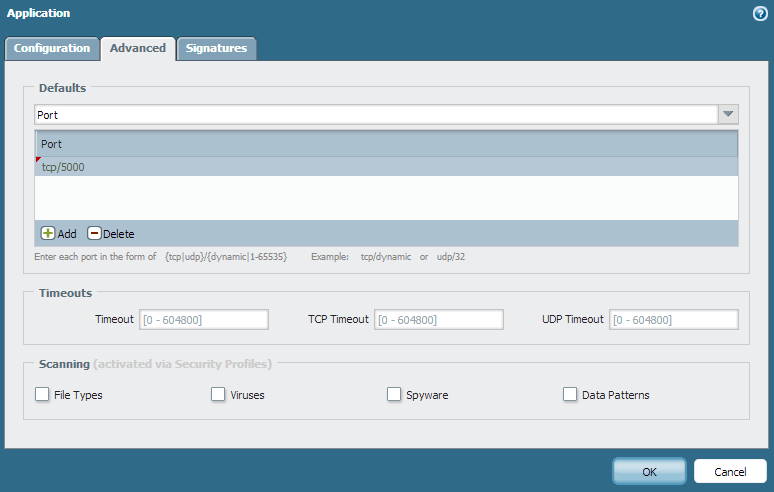
When the security policy is defined with the custom application, and service is set to application-default, the firewall will use the application's defined default ports.
Hope this helps.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-28-2013 02:35 PM
With Application Override,firewall would be bypassing Signature based application Identification.
If the Custom-App defined includes the default ports used by the application,you should be able to use app-default.
I would suggest using any as the traffic is already being allowed based on ports.
ref : https://live.paloaltonetworks.com/docs/DOC-1071
-Ameya
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-28-2013 02:36 PM
Hi,
When you are using application override you are create a customer app with a port number defined in it.
Moreover you also create an services and select that particular service in that application.
Since when app override is created it does not pass through firewalls app engine i think it would be best to either user any or define the service.
Hope this helps
Thank you
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-29-2013 06:34 AM
These posts are helpful. I'll go into a bit more detail to see how others would go about it. We use EDI to send information to and from our mainframe with vendors. The EDI uses the AS2 application with Palo Alto detects. However our port is not in the list of default ports for the application. The default ports for this app are 80,443,4080,5443. We use TCP 5060. I was first thinking an application override policy and give a different port to the app, but based on the comments above that may not be such a good idea. I can see using ANY as the service, but that could potentially open other ports. In this case would it be better to use something like:
For traffic coming from outside to inside to my EDI server, set the application to AS2. Since my port is 5060 do not use ANY but create a custom service for 5060. This way I am only allow AS2 on 5060 and nothing more?
Would this be a better option?
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-29-2013 07:16 AM
Generally speaking, "Application Override" is a tool you can use to override what application the firewall detects. In your case here, the firewall is already detecting the application properly as AS2, so you don't need to use an Application Override. Keep in mind that all of Palo Alto's "AppIDs" are running on all ports at all times - so it has the ability to detect the AS2 application even on port 5060.
However, if you create a rule that says "permit outbound AS2 on application-default", that won't work because you're running this application on a non-standard port. Your suggestion of creating a security policy rule that permits application AS2 on a custom service port (5060) are correct. That would achieve what you're looking for - allowing AS2 on port 5060 and nothing more.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-29-2013 07:19 AM
Perfect! This is a big help. Thanks for your input!
- 1 accepted solution
- 9822 Views
- 6 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Address Group and Tag limitations in General Topics
- From Template Stack Override in Advanced SD-WAN for NGFW Discussions
- False Positive (Generic.ml) in VirusTotal
- Correlating a file path to application inventory in Cortex XDR Discussions
- Cortex XDR Tenant Auto-Upgrade 3.17 → 5.0: UI mixed theme, AI pages stuck loading, Marketplace/Playbook Catalog empty + ingestion quota warning in Cortex XDR Discussions



