- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
What is still missing or needs to be improved in PA Next Generation Firewalls ?
- LIVEcommunity
- Discussions
- General Topics
- Re: What is still missing or needs to be improved in PA Next Generation Firewalls ?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
What is still missing or needs to be improved in PA Next Generation Firewalls ?
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-16-2011 03:56 PM
Hi, will like to understand the oppinion from the PAN community about the features that are still missing or needs to be improved.
Will appreciate if you can specify by functionality like :
FIREWALL
Must Have : A,B,C
Nice to Have : D,E,F
Thks
Mario
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-14-2013 01:48 AM
I would like to have something more to organize the view on ruleset, because the more rules we get the more difficult it is keeping the overwiew. We are using zones, tags and webgui but it is to less.
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-14-2013 03:56 AM
- SPEED. Five minutes to COMMIT a URL to a filter? Twenty minutes to reboot? My Microsoft ISA 2004 booted faster. A URL filter took ten seconds at most.
- Same request as others: Better documentation with real examples.
- Better logging for VPN! I want to know when user JSmith logged on and when she logged off the VPN.
- REDUNDANT POWER SUPPLIES!!! Over 99% of my servers have dual power supplies. Edge switches have dual power supplies. Minimum is to have a modular power supply design with a secondary empty slot. Those that don't need/want the supply simply don't order it.
- Better interface into Active Directory. The PAN-AGENT sucks. If there are multiple users on a computer I cannot get reliable logs for Internet monitoring.
Great comments!!
Documentation needs real examples in every section. Tired of searching on Communities.....
PAN-AGENT sucks. Multiple users confuses it badly.....
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-17-2013 07:44 PM
egearhart wrote:
but please for the love of packets improve your QA process! Test all the features in the product! Test all the features when every major release comes out!
I love your turn of phrase, and 100% agree with your sentiment.
QA of late has *sucked*. Documentation and QA are my two biggest bugbears with PAN.
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-18-2013 12:52 AM
IPSEC VPN IKEv2
IPSEC VPN Phase-1 Authentication RSA-Signature
Throughput report backwards from directly Paloalto (not any snmp, etc)
embryonic/half-open tcp session values on zone protection / DDOS rule
QOS with Link aggregation
802.1x support
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-19-2013 12:13 PM
Nice to have: Ability to select the threat action from a threat log message - i.e. If a threat is logged ("alert"), the administrator can open the threat log and select a new action such as "block" or "reset" etc. The new action is updated in the corresponding threat profile.
MUST HAVE: SSD's for the win!!! :smileycool: all models
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-25-2013 06:51 AM
Management interface improvements - look into features of FMT 2.0!
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-25-2013 04:13 PM
This should be an easy one. From the GUI, I should be able to get the properties of an Ethernet interface. The only way I know how to do that is via the CLI command show interface ...
Mike
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-26-2013 12:01 AM
Which properties are you missing ? in 4.11 you can hover over the red/green interface icon & it pops up the speed / duplex ?
Things I would like to see (I run 4.1.11h1 mostly):
- The ability to log implicit rules so I can get rid of the explicit block all at the end of my policy which causes it to generate a screen full of warnings - or add an option to turn off the generation of spurious warnings on commit.
- Port Panorama to HyperV for more deployment options. Panorama should be free IMHO.
- Improved logging for high profile events like a reboot so I dont have to guess why the box restarted.
- Better QC ; I would much rather have a slower release of new features & better testing to ensure that existing features are not broken.
- Allow me to customise the messages generated when dropping SMTP with a Data Filter rule. At the moment it sticks in something about Blocked by PaloAlto firewall which is undesirable.
- SSD upgrade options for all the older hardware so I dont have to replace everything to get rid of my 15 min commit time....
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-26-2013 04:33 PM
msullivan wrote:
This should be an easy one. From the GUI, I should be able to get the properties of an Ethernet interface. The only way I know how to do that is via the CLI command show interface ...
Mike
What, you mean like this?
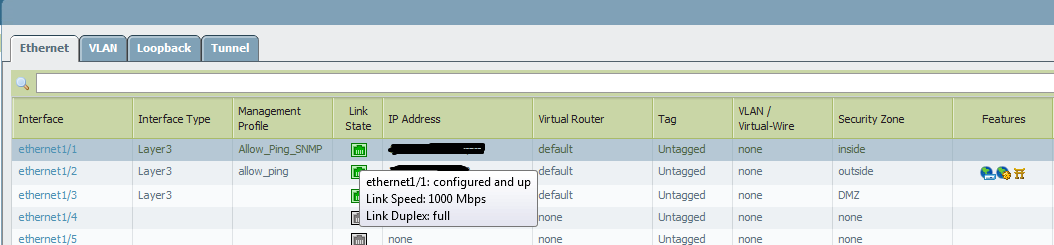
Shows the interface properties pretty well, from where I'm sitting.
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-14-2013 12:23 PM
Regarding Speed... Would it be possible somehow to offload some of the computation effort during a commit to the client browser (JavaScript)? I know the PA is a security device...but maybe some less critical parts... or maybe there are techniques where the PA could verify that code hasn't been altered on the client...? Just a thought.
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-19-2013 09:58 PM
oschuler wrote:
Regarding Speed... Would it be possible somehow to offload some of the computation effort during a commit to the client browser (JavaScript)? I know the PA is a security device...but maybe some less critical parts... or maybe there are techniques where the PA could verify that code hasn't been altered on the client...? Just a thought.
*Horrible* idea. Java is about as secure as a broken padlock. Doing this would completely remove the use of the PAN device for security by opening it to god knows what kind of hacks.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-21-2013 08:59 AM
I would definitely agree with the test GlobalProtect comment. There are so many bugs that the client it is virtually unusable with my staff. Compared to other solutions on the market, SonicWALL, Cisco, and CheckPoint are leaps and bounds ahead. GlobalProtect doesn't even compare or rank with these. There are times it takes it 30+ seconds to connect when CheckPoint takes less than 2. Sometimes users have to connect 10-15 times before it finally occurs. All we ever get it "open a support call" or "submit an enhancement." Typical response. It seems that Palo Alto doesn't put much effort into fixing the product. I would figure that an enterprise-class product would behave differently, especially for the price they charge! Simply get a competitors VPN product and PAN will see that theirs cannot keep up.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-21-2013 11:17 AM
I agree with you,connecting should be quickly. Also ssl vpn clients should have a reserved/static ip option.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-21-2013 03:20 PM
We had a similar issue. GP clients took 30 sec+ to connect. For a fix please see https://live.paloaltonetworks.com/message/22957#22957
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-22-2013 06:49 AM
darren.g Java and Javascript are two different things, just want to point that out. Although trusting a browser client's Javascript interpreter to verify firewall policy is a rather cray idea, I agree.
oschuler If the policy build could be pushed to the client in a secure way and then signed and pushed back to the PA appliance this would feasibly work. I don't know of a good way to do that without something like a Java applet though, which would make the PA admin implementation much "fatter" by requiring a Java applet
- 48877 Views
- 82 replies
- 1 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Palo Alto Networks PA- 450 Next‑Generation Firewall to maintain uninterrupted BSNL SIP trunk services in the event of a primary internet link failure. in Next-Generation Firewall Discussions
- High Availability Latency / Bandwidth Requirements in General Topics
- Performance impact of using higher DH group for site-to-site VPNs in Next-Generation Firewall Discussions
- Terminal server from a single IP address, the firewall cannot distinguish which user generated which traffic! in Next-Generation Firewall Discussions
- VM-Series Next Generation Firewall in Azure in VM-Series in the Public Cloud



