- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Consuming user group in GlobalProtect SAML Authentication
- LIVEcommunity
- Discussions
- Network Security
- GlobalProtect Discussions
- Re: Consuming user group in GlobalProtect SAML Authentication
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Consuming user group in GlobalProtect SAML Authentication
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-16-2017 02:15 PM
A bit of background: We are an all-Google G Suite company. We do not have internal LDAP servers. Everyone auths to Google. We are using PA 3060s as our firewalls and VPN systems.
We are getting ready to turn on SAML authentication for GlobalProtect. We are using Google as our IdP.
I've gotten it working, but I want to make policy decisions based on the user group that we are returning in the SAML assertion.
In Google, I have a user attribute with a "role" specified for each user, and then we are passing this back to the firewalls via a attribute mapping in our SAML App definition in Google.
Within the SAML authentication profile in the firewalls, I have set the User Group attribute to "role", and when I connect to the portal through Burp Suite, I see a SAML "role" attribute being returned from Google and asserted to the firewalls.
However, I have not found a way to use this "role" attribute in client IP pool assignments or in making policy decisions. I have tried making a local group that matches the "role" value, but that does not work.
Has anyone done this, or have any insight on this?
Regards,
Mark
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-16-2017 04:17 PM
Hi @mtsujihara
I don't know it this user-group-mapping fof SAML users is possible. Probably not because the default group-mapping in the WebUI requires an LDAP profile.
But may be you should give this a try for the creation of groups and containing users: https://www.paloaltonetworks.com/documentation/80/pan-os/xml-api/pan-os-xml-api-request-types/apply-...
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-08-2018 12:55 AM
Hi @mtsujihara
Could you please show me how to configure PA using Google SAML as IdP?
Thank you in advance,
Regards,
Army
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-17-2018 12:34 AM
I've gotten GSuite SAML2.0 working and have GSuite configured to send the user's "Department" as the "group" attribute. In the PA, I have the "User Group Attribute" set the "group". As the OP says, I don't see that I can use the "group" value anywhere (policies, etc).
Has anyone gotten this to work?
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-17-2018 10:11 AM
The firewall won't let you use that attribute the same as you would with an LDAP group. The link that @Remo provided describes how you could probably script this to assign users to different groups using the xml-api and how you would format the input file that you would need to put together for this.
I would recommend reaching out to your SE and setting up a feature request.
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-17-2018 11:55 AM
It depends on how much you really need this group mapping for SAML authenticated users ... it will be a bit of work
- Set up a webserver
- Create a log forwarding profile for system logs that applies for global protect login and logout logs and send these logs to your webserver
- Create a web application on your webserver that processes these http request with the logs from your firewall
- For every log that the webserver receives your web application needs to push that information to the firewall API to create dynamic User-IP-Group mappings and also delete them when a user logs out
4 "simple" steps and you have implemented what you need 😛
But I recommend the feature request anyway ...
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-05-2020 12:37 AM
I dont know if this is still an issue for you, but i had a similar problem with Azure AD, so in the end created a secure LDAP connection to it and in the LDAP Group configuration changed the username to be email and that has worked both on Global Protect and Security rules.
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-03-2020 05:49 AM
Have anyone successfully implemented Group-Mapping with G-Suite?
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-05-2020 01:39 PM
Nope, still struggling with this same issues. SAML authentication works great, but group information sent int he SAML assertion is not accessible in policy rules. In my case, we have access to LDAP, but wanted to use SAML to be able to add Duo two factor authentication with a usable UI. Opened a case with support, maybe all of us are wrong.
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-05-2020 07:09 PM
For what its worth, support confirmed that there is no group support with SAML authentication. They referenced a prisma document: https://docs.paloaltonetworks.com/prisma/prisma-access/prisma-access-panorama-integration/authentica... which does state:
"You can’t use group information that’s retrieved from the SAML assertion in either security policies or the agent client configuration in the portal and gateways. If you have a requirement to configure user group-based policies and configuration selections, you must Enable Group Mapping and retrieve the user group information from the LDAP server using Group Mapping Settings."
However I did find an unsupported workaround at least in 8.1. If you can do LDAP group mapping but want to use SAML authentication (which is what we want to support multifactor), then if you send over the SAML username in the form <domain>\<username> , it will match up to the AD/LDAP user and use the group mappings from LDAP, this may be what Ozamir references above.
This is no help for people who want to use Google exclusively.
It is definitely an incomplete implementation since the SAML configuration supports both an "Access Domain Attribute" and a "User Group Attribute" but it does not use either one for global protect. (These are only used for Mgmt SAML authentication).
Hope this information helps someone else.
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-16-2020 08:25 AM
Hi There
I had the same issue with SAML and LDAP group memberships, I'm using DUO with global protect and my intend was to customize the application based on group memberships.
I used @JohnWade solution and under authentication profile I changed username attributes from user.username (as DUO instruction) to <domain>\<username> and it is working great.
thank you for the help.
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-19-2020 12:50 PM
All you need is the Metadata after configuring the app for your portal/gateway in the Google IDP. You need two different apps for Portal and gateway if the addresses are different, unlike in Okta google doesn't support multiple URLs in a single app.
goto SAML identity> create a server profile by importing the metadata.
create an Authentication profile and call the SAML server profile you created.
goto your portal and gateway > authentication> Set it to the authentication profile you created. Commit the changes.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-16-2020 08:47 AM
We did this with Azure AD as well.
Out basic setup is as follows:
- Configure the LDAP Server profile for the on-premise AD infrastructure (Base DN is in the following format "DC=domain,DC=local" )
- Configure SAML IdP to work with Azure AD
- Configure Group-Mapping using the LDAP profile. On the "User and Group Attributes" tab, we swapped "Primary Username" to be "userPrincipleName" and "Alternate Username 1" to be "sAMAccountName"
This way the SAML username attribute matches the LDAP username attribute - On the GlobalProtect side, we specified the group in the configs in the following format: "CN=User Group Name,OU=org unit,DC=domain,DC=local"
When we tried it in the "domain\group name" format, we had no success, but we found a post on reddit that suggested trying either format to see what works in your environment. Apparently the format is dependent on how your AD infrastructure is setup.
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-06-2020 04:46 AM
Hello,
This is indeed an excellent workaround, tested here also in 8.1. Thanks for this information, it's really useful.
Usually, we rely on our Active Directory, which is old enough to be primarily based on the SAM Account Name, which is what the NGFW is looking for by default, in the following format : Domain\SAMAccountName (ie. acme\doej)
We began using Okta to authenticate our GlobalProtect users for non-Windows or non-Domain devices, but it was impossible to use the "groups" attribute from the SAML assertion in the GlobalProtect configuration.
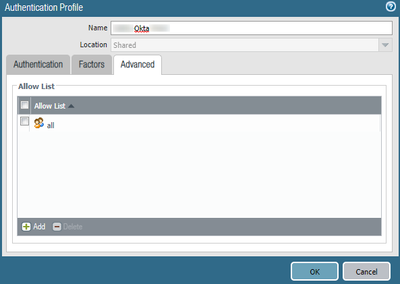
We opened a case with TAC, and the answer was the following : this attribute can only be used in the "Allow List" of the Authentication Profile, but nowhere else :
In order to make this work, the username sent by Okta in the assertion must be the same as the username that the NGFW understand by default, that is, the "Domain\SAMAccountName". This is not an easily available option in Okta.
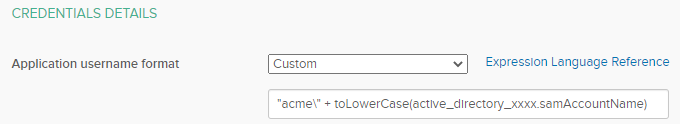
In the GlobalProtect app in Okta :
- Edit the "Sign On" settings
- Find "Credentials Details" section
- Select "Custom" in the "Application username format"
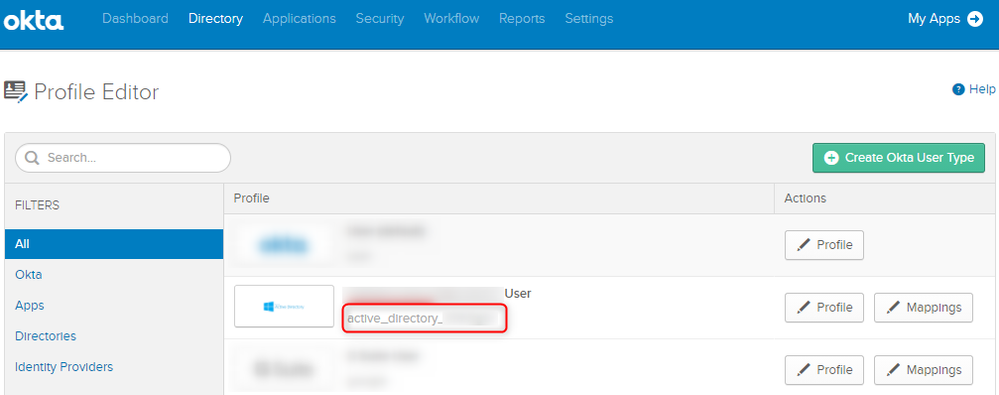
- Fill the field with this syntax : "yourdomain\" + toLowerCase(active_directory_xxxx.samAccountName)
Please note that the "active_directory_xxxx" must match your directory ID, that you can find in the
This only works, however, if you have an LDAP server somewhere... With Okta, I know there is a way to use it as an LDAP server, which might do the trick, like described in this link : https://help.okta.com/en/prod/Content/Topics/Directory/LDAP-interface-main.htm
With all this combined with a bit of Group-Mapping, you could tinker this to work as expected ! 🙂
It's unfortunate that PAN does not seem to want to integrate a wider use of the group attribute of the SAML Assertion. It complexifies the use of SAML, with little to no documentation... 😞
- 41573 Views
- 25 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- GlobalProtect Cert+SAML in GlobalProtect Discussions
- Global Protect Portal / Clientless VPN does not recognize SAML username after update to 10.1.14-h20 in GlobalProtect Discussions
- Global Protect Connectivity Issue in GlobalProtect Discussions
- Okta Verify window behind GP login window fix in GlobalProtect Discussions
- PA Global Protect in GlobalProtect Discussions