- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Clientless VPN - Application is not accessible
- LIVEcommunity
- Discussions
- Network Security
- Next-Generation Firewall Discussions
- Re: Clientless VPN - Application is not accessible
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Clientless VPN - Application is not accessible
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-12-2023 12:46 AM
Hello All,
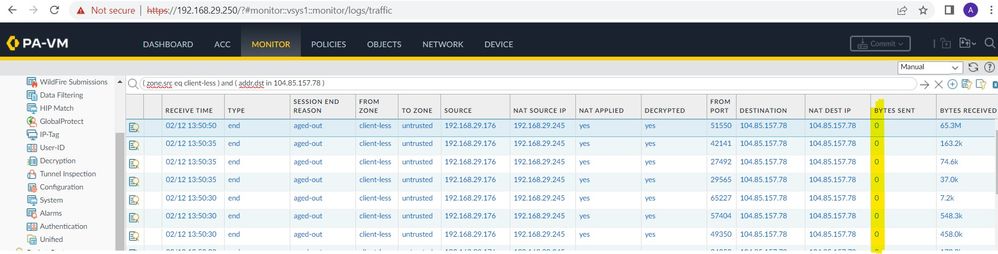
This is my topology I have configured Clientless VPN hosting two application as, paloaltonetworks.com (external-application) and amazon.forest.in (internal hosted application). But i am unable to access the application that hosted inside. In this question have attached my configuration also. other than that there is no sent byte for clientless-VPN traffic also.
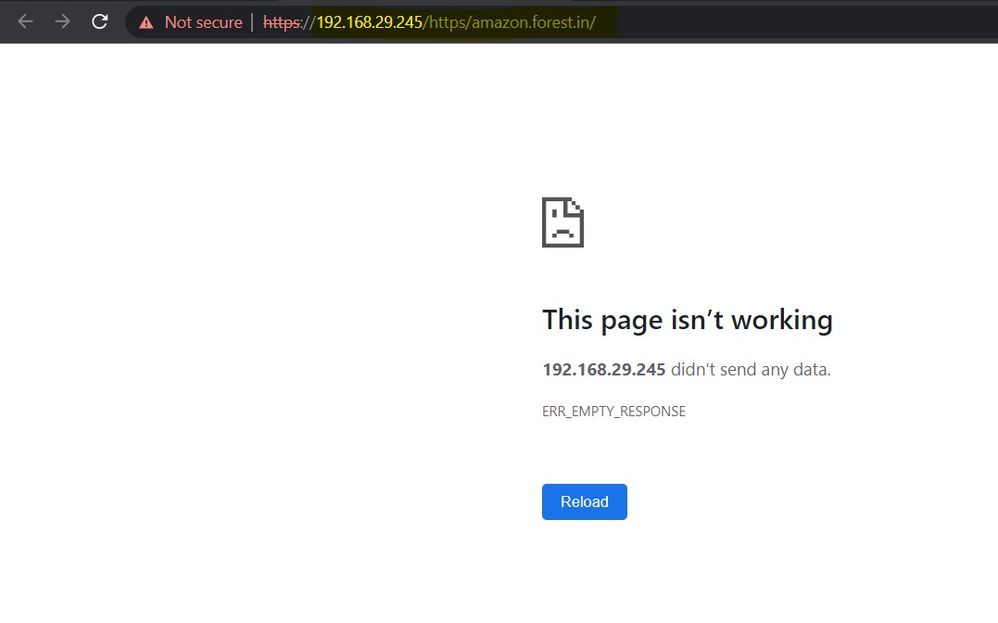
ISSUE NOTE : 1.External Application working but there is no sent bytes
2.Internal Application not accessible
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-14-2023 12:20 PM - edited 02-14-2023 12:24 PM
This sigfnals a routing issue or DNS issue as 0 bites are send. Check if the DNS resolution is working for the Palo Alto as maybe the routing or Service route is wrong (palo alto by default uses the managment):
https://docs.paloaltonetworks.com/pan-os/10-1/pan-os-networking-admin/service-routes
Also check the config:
Finally just check the global counters, tcdump for drops and the security policy:
Also there are a lot of articles for debuging web issues for clientless vpn and try using different browsers:
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000PPizCAG
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000PLSiCAO
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-20-2023 01:17 AM
Hello, Did you test the DNS resolution and routing are correct ? If so using another browser as your error seems to be seen a lot for chrome browser and then finally doing tcpdump/pcap capture for the rewrite action to see how Palo Alto rewrites the HTTP/HTML content and you can find this from the links I shared and also using Fiddler to see how direct access to application looks like without the Clientless VPN and with it and to compare.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-06-2024 11:03 PM
I am having different issue, not sure if this is only for me or other users as well. If my issue is faced by everyone then I am not sure how clientless VPN is helpful.
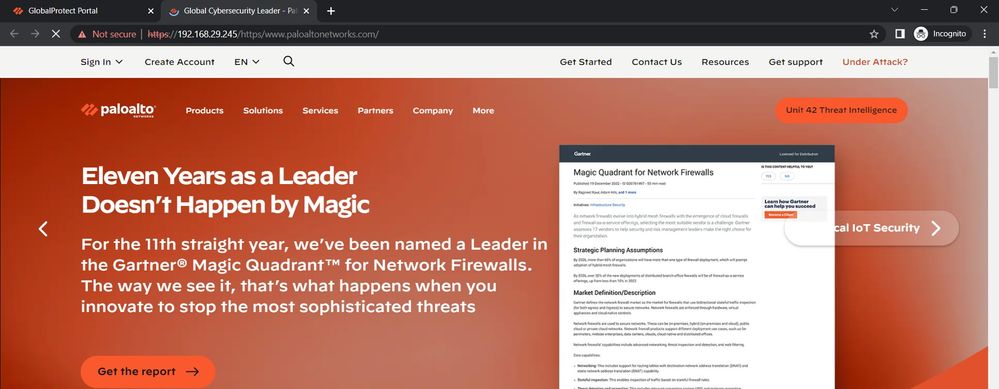
So I will take example of above images:
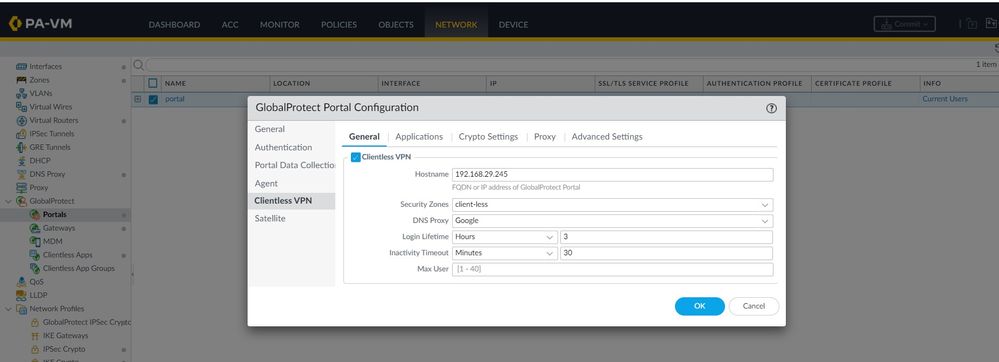
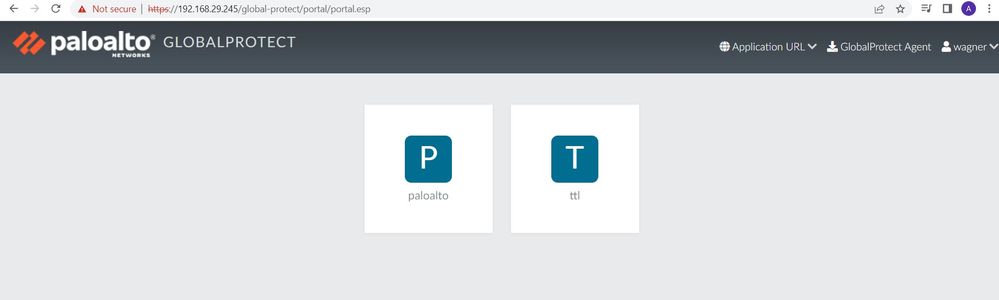
User logs in to Clientless VPN at https://192.168.29.245 and on portal page, user clicks on Palo Alto tile. This opens a new tab with URL as https://192.168.29.245/https/www.paloaltonetworks.com/ , as shown in above image.
Now the issue is - On the Palo Alto page if I click on any link(for example 'Sign in', then it takes to login page. However on the browser URL appears to be https://signin.palolaltonetworks.com not https://192.168.29.245/https/signin.paloaltonetworks.com .
Former URL is not going via firewall rather it goes directly from user machine to the webpage, how can I ensure any link on the page is prefixed by VPN portal "https://192.168.29.245"?
Support isnt able to solve the problem from past 1 week. I am using stable PAN-OS 11.1.3 and Clientless app version 98-260(latest).
Thanks.
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-19-2024 11:42 PM
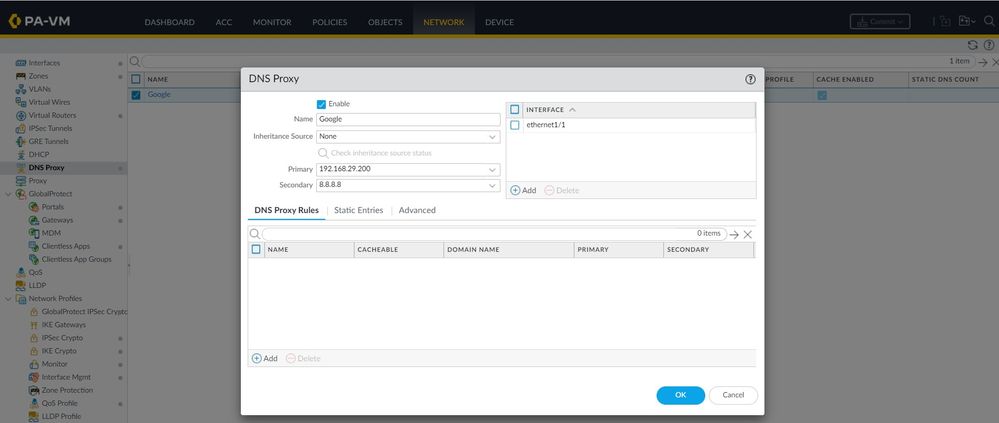
Support seems right to me as if traffic does not go through the firewall then it can't resolved from the firewall side as it seems that your web app design and DNS is the one that needs some reconfiguration. Nowadays DNS servers can return different IP addresses for DNS requests based on the source IP address/network of the client, so your DNS can return the firewalls IP address (you may need to change the SSL cert in that case on FW to have the CN as the fqdn) or you can direct traffic to the firewall and use static entries option.
How to Configure DNS Proxy on a Palo Alto Networks Firewall - Knowledge Base - Palo Alto Networks
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-20-2024 08:29 AM - edited 11-20-2024 08:31 AM
Maybe also as the User authentication is in SAML or Oauth it can't be rewritten as it is not css, html or javascript, which seems normal to me.
If the auth is SAML/OAUTH SSO you can configure the NGFW to be IsP SAML (if the app is SAML IsP then the the same thing should be done from the firewall) for example as when the user has the SAML assertion then it shouldn't be an issue to log into the backend and there to be no authentication need on the backend.
If this does not work may need to disable the authentication for when the source ip is the firewall as the NGFW can still forward the username to the app in a header https://docs.paloaltonetworks.com/pan-os/11-1/pan-os-admin/user-id/deploy-user-id-in-a-large-scale-n... and the NGFW will do authentication for the user https://docs.paloaltonetworks.com/globalprotect/10-1/globalprotect-admin/globalprotect-clientless-vp...
- 3984 Views
- 5 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- High Data Plane Utilization During Business Hours in Next-Generation Firewall Discussions
- gov.in Website not accessible in Next-Generation Firewall Discussions
- When GlobalProtect exceeds Login Lifetime cannot reset/access the application in GlobalProtect Discussions
- Redirecting from 3rd party auth provider back to GlobalProtect Clientless VPN application in GlobalProtect Discussions
- Can Copilot help with writting of custom application or vunrability signatures on NGFW or Prisma Access? in Strata Copilot Discussions