- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
ISP ping going out via different interface
- LIVEcommunity
- Discussions
- Network Security
- Next-Generation Firewall Discussions
- Re: ISP ping going out via different interface
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
ISP ping going out via different interface
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-19-2023 10:35 PM
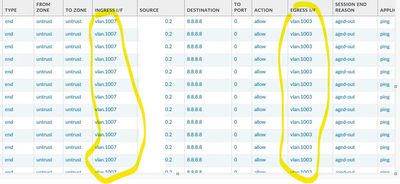
I am facing a very strange issue. Thee are four ISP connected to PA. All are VLAN interfaces.
While doing a ping to 8.8.8.8 or any public IP from the vlan interface IP it works fine except for one ISP.
For one ISP if a ping a initiated from vlan.7 the traffic goes out via vlan.3. attached a screenshot.
Ping is initiated from PA cli - ping source <int ip> host 8.8.8.8
Please note you are posting a public message where community members and experts can provide assistance. Sharing private information such as serial numbers or company information is not recommended.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-20-2023 09:21 PM
Hello @ceapen01
Hi, check if you have
ECMP that could be balancing the traffic.
Or check if you have any PBF policy that is forcing that traffic flow through that other interface.
Check that by any chance at virtualrouter level is not set an explicit route against that destination.
Another thing the PBF will not manipulate the traffic coming from the FW, that is to say in this case the IP source of vlan 7 that you mention, it will always use the route with the best metric (the one with the lowest metric).
Check if the same thing happens with an end equipment, an endpoint of vlan 7 and you will get better conclusions of the behavior.
Regards
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-21-2023 02:45 AM
Thank you
ECMP that could be balancing the traffic.
>>I didn't understand this point
Or check if you have any PBF policy that is forcing that traffic flow through that other interface.
>>No PBF
Check that by any chance at virtualrouter level is not set an explicit route against that destination.
>>As there are four ISP, four default routes exist with different metric
Another thing the PBF will not manipulate the traffic coming from the FW, that is to say in this case the IP source of vlan 7 that you mention, it will always use the route with the best metric (the one with the lowest metric).
Check if the same thing happens with an end equipment, an endpoint of vlan 7 and you will get better conclusions of the behavior.
>>endpoint of vlan 7 gets internet and ping. No issues.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-21-2023 09:07 AM - edited 01-21-2023 09:08 AM
As already mentioned PBF will not be applied to traffic sourcing from firewall itself.
If you ping from public IP to next hop then you can expect traffic to go out from same interface (because it stays inside same subnet).
If you ping from public IP to IP on the internet then you must have static route configured towards that public IP.
Otherwise Palo will look at static routes.
If multiple 0.0.0.0/0 routes have same metric (ECMP is enabled) then source interface is chosen based on ECMP settings.
So Palo will not care that you ping from specific vlan IP. Path is chosen based on virtual router configuration.
Palo Alto Networks certified from 2011
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-22-2023 12:59 AM - edited 01-22-2023 01:00 AM
there are different static routes to 0.0.0.0 with different metrics. I can see ping to 8.8.8.8 from vlan 7 is now taking the interface with lowest metric (vlan3).
Is there any method such that ping to 8.8.8.8 from vlan 7 interface wd only egress through vlan 7 only.
**furthermore i can this is only happening with vlan 7. If ping from vlan 4 or 5, traffic egress via that interface only.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-22-2023 08:05 AM - edited 01-22-2023 08:06 AM
No.
Traffic always uses interface with that has lowest metric route.
You need more specific static route towards 8.8.8.8 to send traffic towards 8.8.8.8 out from vlan 7 (if vlan 7 don't have lowest metric) for traffic sourcing from the firewall.
For traffic passing firewall (sourced from workstations/servers) you can use either static route or PBF (PBF is checked first and if no PBF then virtual router is checked for routing decision).
Palo Alto Networks certified from 2011
- 4168 Views
- 5 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Unable to reach Palo Alto - Global Protect Portal. in GlobalProtect Discussions
- PAN-OS 10.2.17 HA A/P - Mgt interface reported as duplicate IP of data interface in Next-Generation Firewall Discussions
- Issues with SSH and Telnet access only on the passive firewall. GUI access is working fine. in Next-Generation Firewall Discussions
- DNS-Proxy vs management dns queries in Next-Generation Firewall Discussions
- ION Security Stack in Advanced SD-WAN for NGFW Discussions



