- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Custom Admin Template Examples for GP Admin and Network Engineer?
- LIVEcommunity
- Discussions
- Network Security
- Panorama Discussions
- Custom Admin Template Examples for GP Admin and Network Engineer?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Custom Admin Template Examples for GP Admin and Network Engineer?
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-13-2021 04:31 PM
So recently we (as in voluntold lol) decided to get rid of our dedicated Cisco L3 devices and move the L1 (VMWire) only FW's into L3 as a "cost saving measure". Won't get into how much I hate this but the decision has been made. Also this entire thing is managed via Panorama so don't need "do local FW overrides of templates". Also virtual systems not an option in many cases as the majority are low end small site models (i.e. 800's and down) hence don't need to get into "spin up a virtual system and control it that way" discussions.
Anyways anybody have a config snippet they want to share for setting up the following two custom admin roles?
1) GP Admin - Needs access to the FW running GP (not all of them, just one), the ability to configure it all, maintain it, etc (via Panorama templates) but NOT anything else in Panorama or the FW.
2) Ditto but Network Engineer - I.e. needs access to the virtual routers, L2/L3 configs, interface configs, routing tables, etc but not stuff like admin database, authentication setup, security policy or objects, etc.
The built-in rolls are ill equipped for this and I know how do do via effective superuser via Device Templates/Admin a per FW / virtual system level but I'm looking for more fine tuned than that i.e. "Just every function GP needs and nothing more" or "Every function a network engineer would need to treat the PA like a L3 device but nothing more"
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-18-2021 05:39 AM
Thank you for posting question @PeterT
I believe that Access Domain together with Custom Admin Roles can give you that level of granularity you are looking for.
I would suggest to go to: Panorama > Access Domain > Add new Access Domain
Then select Template where all Global Protest is configured, limit Device Context to Firewalls where Global Protect configuration is pushed. Below is an example:
Then navigate to Panorama > Admin Roles > Add new Admin Role and limit Device Group & Template only to Global Protect configuration. Below is an example:
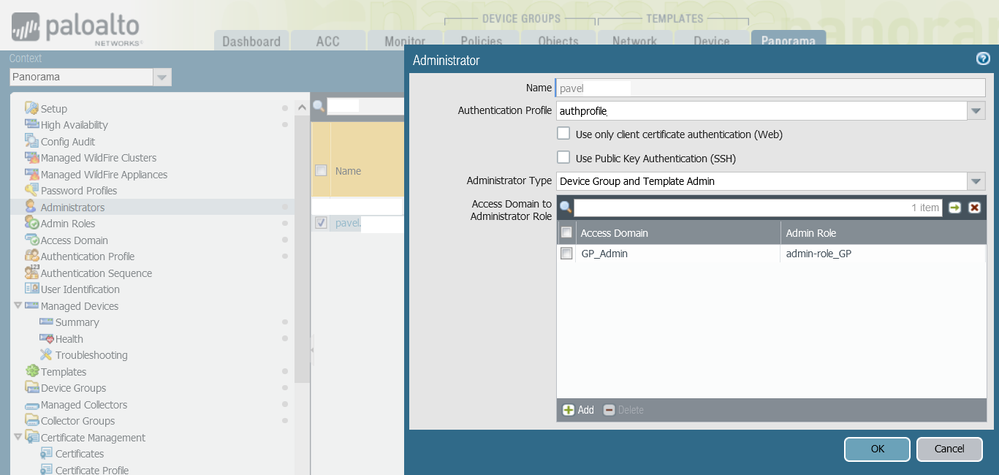
Then link Global Protest Access Domain and Admin Role together in the account. Below is an example:
Once the admin assigned to Global Protect role logs is, he will be able to see and manage only corresponding configuration:
Exactly the same configuration can be replicated for Network Administrator role by changing setting in Access Domain and under Admin Role.
Kind Regards
Pavel
- 2494 Views
- 1 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!