- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Primsa Sase Web Security
- LIVEcommunity
- Discussions
- Secure Access Service Edge
- Prisma Access Discussions
- Primsa Sase Web Security
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Primsa Sase Web Security
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-25-2023 05:45 AM
Hi all
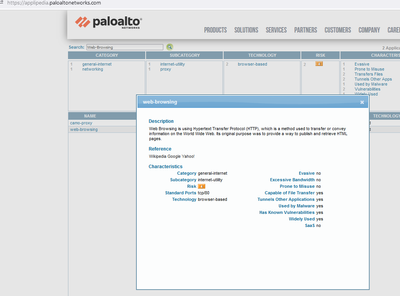
I am trying to understand the Prisma Access Cloud Managed Web Security policies. There are options to match on users or services. But how is traffic identified as "Web" if all settings are left to default. And will Web Security policy take precedence over Security Policy configured in the same folder?
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-08-2024 12:38 PM - edited 01-08-2024 12:39 PM
To get an answer from someone inside Palo Alto better contact your sales manager. From what I can tell it is doing app identification as even If you have not created application override Palo Alto still does basic app identification, so auto matching web-browsing and ssl and app shift when decrypted to web-browsing does not seem complex.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-09-2024 12:49 AM
@nikoolayy1 This is not related to the question. The query is about the Prisma Access Cloud based web policy
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-09-2024 02:38 AM
Prisma Access in the background uses Palo Alto Firewalls. I think that it is not the virtual edition but some form of container based but still the same code with the same functions and it does not matter if it is not managed by Panorama but in the cloud.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-10-2024 08:32 AM
Also for SAAS App ID Prisma Access and the firewalls use App-ID Cloud Engine (ACE) https://docs.paloaltonetworks.com/pan-os/10-2/pan-os-admin/app-id/cloud-based-app-id-service if you are interested in this.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-10-2024 09:46 AM
I am using Prisma Access SASE and have wondered the same thing. The best resource I have found is here: https://docs.paloaltonetworks.com/network-security/security-policy/administration/web-security/rule-...
Web Access Policies are applied before Security Policies. I generally prefer security policies for their granularity, but sometimes it's hard to create a security policy that doesn't violate some "best practice", in which case I fall back on Web Access Policies.
- 3947 Views
- 6 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!