- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
not-resolved URL for s3.us-central-1.wasabisys.com
- LIVEcommunity
- Discussions
- Cloud Delivered Security Services
- Threat & Vulnerability
- not-resolved URL for s3.us-central-1.wasabisys.com
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-20-2022 02:23 PM
That appears to be categorized as "Online Storage and Backup" in the URL filtering. You can test for your self here:
https://urlfiltering.paloaltonetworks.com/
As for why your particular firewall is having a problem resolving that, it could be a number of things. See the following to debug:
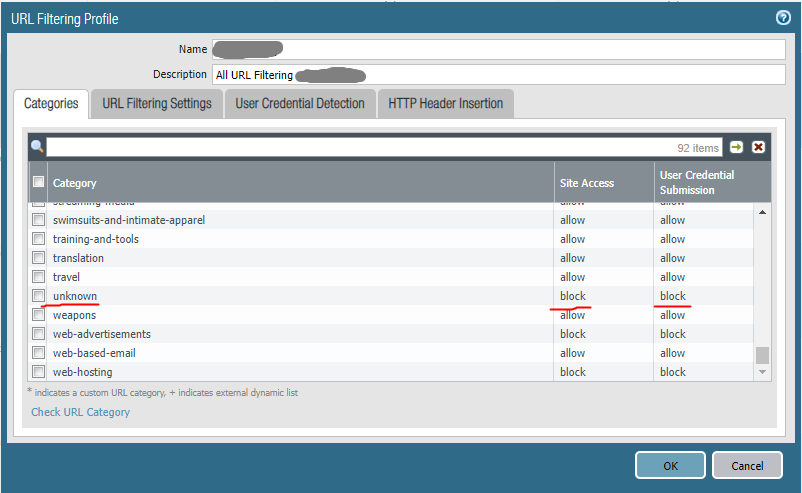
The default Objects->Security Profiles->URL Filtering profile treat not-resolved as "Allow". So I would guess you are using a custom URL Filtering profile which has that category set to "Block". As a bypass, you could also create a custom URL Category with that URL and add it as Allow in your custom URL Filtering profile.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-20-2022 02:38 PM
Thank you. I did. I think it is an issue with the firewall communication or a bug in our currently running firewall version (9.1.9).
I added it to the exclude allow-list until we upgrade our firewall and see that resolved this issue.
Thank you,
Victor
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-20-2022 03:40 PM
We have been running 9.1.14-h4 for some time and haven't had any issues with it. We did have problems when upgrading the URL filtering from PAN-DB to Advanced URL though as we have "not-resolved" and "unknown" blocked by default and that prevented the database from getting updates initially. Once we bypassed those categories temporarily the url-cloud could connect and download the initial database, at which point the categories could be blocked again and updates happened normally.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-20-2022 03:50 PM
Hi, We have the same situation. We have advanced URL filtering and now switching over from a standard local database to online when the license is expired from the standard and gets switched to the advanced one. Could you describe how to fix this issue? Disabled that two categories? Thanks in advance get more detailed descriptions.
Victor
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-20-2022 04:32 PM
Yes... determine which Policy->Security rule is affecting your outbound traffic from the PA to the internet and what its URL Filtering rule is. This will be highly dependent on how you have your PA setup... but it is probably coming out your PA management interface (see Device->Setup->Services->Service Route Configuration->URL Updates I think). This probably goes out to the internet thru some general outbound Security policy like:
name = Internet Access
srczone = Trusted
srcaddr = CorpIPs,MgmtIPs,VPNIPs
dstzone = Untrusted
Actions = Allow, URLFiltering=CorpFilter
Look at Objects->Security Profiles->URL Filtering->"CorpFilter" allow and block status. The "not-resolved" and "unknown" categories need to be set to "allow" to initially download the URL database.
You should be able to initiate a license check again and the PA will download/initialize the new URL database. Verify with "show url-cloud status" in the CLI, it should show a very new database version. If it shows database version 000.00.00.000 your system hasn't successfully downloaded the database yet. Once the URL database updates, the URLs should be known again and categorized correctly, so you can change not-resolved/unknown back to "block" if you so desire.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-20-2022 04:57 PM
Hi Adrian,
I very much appreciate your taking the time to put into the details. I think we are fine with the download of the latest URL DB. Here is the CLI result without any changes to the firewall:
show url-cloud status
PAN-DB URL Filtering
License : valid
Current cloud server : serverlist.urlcloud.paloaltonetworks.com
Cloud connection : connected
Cloud mode : public
URL database version - device : 20221020.20358
URL database version - cloud : 20221020.20358 ( last update time 2022/10/20 16:48:02 )
URL database status : good
URL protocol version - device : pan/2.0.0
URL protocol version - cloud : pan/2.0.0
Protocol compatibility status : compatible
I think our issue is in some bug in this version of what we have, 9.1.9.
We will upgrade the FW tomorrow night to 10.1.6-H6 to see if that resolves this type of issue. I will try to follow up if I can confirm it.
Thanks again,
Victor
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-20-2022 05:11 PM
Hmmm... yeah your url-cloud status looks fine. The docs say you need 9.0 or later and content release (Apps and Threats) 8390-6607 or later. I don't see anything specific for PAN-OS versions other than CN devices are not supported.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-20-2022 05:20 PM
Here is what I looked up was a similar issue, and this is what we got from the technical support:
"After reviewing the information gathered we found that we are possibly facing a Known issue for Pan-OS versions and Starting from PanDB 2.0, where url_data with num==0 will be allowed. PAN-173469.
In case of 9.1 this issue has been fixed on 9.1.13"
Best regards,
Victor
- 5229 Views
- 8 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!