- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Query -> Data Center Best Practice Antivirus Profile
- LIVEcommunity
- Discussions
- Cloud Delivered Security Services
- Threat & Vulnerability
- Re: Query -> Data Center Best Practice Antivirus Profile
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-20-2018 06:49 AM
Hi Community.
The below article states that "The Antivirus profile has decoders that detect and prevent viruses and malware from being transferred over six protocols: HTTP, SMTP, IMAP, POP3, FTP, and SMB":
A bit further down in the same article, the following can be read: "The reason to attach the best practice Antivirus profile to all security policy rules that allow traffic is to block known malicious files (malware, ransomware bots, and viruses) as they attempt to enter the network. "
Why would AV be enabled for ALL security policies that allow traffic, if it only has decoders for 6 protocols?
For instance, why would AV be enabled for a security policy using app=FTP, if AV does not have a decoder for this app=FTP?
Thanks.
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-04-2018 05:55 AM
Thanks bvandivier 🙂
Think it would be useful to update the admin guide, from the current "AV should be enabled "to all security policy rules that allow traffic", to "AV should be enabled to all security policy rules that allow traffic for Apps: HTTP, SMTP, IMAP, POP3, FTP, and SMB"
Cheers.
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-20-2018 11:28 AM
AV enforcement is per-protocol, and WF signatures are also configured separately per-protocol in the Antivirus profile.
AV will process for Security Policies configured to use it.
Answering your question: "Why would AV be enabled for a security policy using app=FTP, if AV does not have a decoder for this app=FTP?" ... AV would not be enabled for FTP traffic matching the security policy if the associated AV profile is not set to enfoce AV signatures for the ftp protocol.
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-21-2018 01:41 AM
Thanks Mivaldi.
1) AV enforcement is per-protocol -> I assume this is only for the following 6 protocols, right? From the admin guide:
"The Antivirus profile has decoders that detect and prevent viruses and malware from being transferred over six protocols: HTTP, SMTP, IMAP, POP3, FTP, and SMB"
2) If the above is correct, what is the below parragraph referring to, if there are only 6 decoders for AV? Why does the admin guide state that AV should be enabled "to all security policy rules that allow traffic", if there are only decoders for HTTP, SMTP, IMAP, POP3, FTP, and SMB?:
"The reason to attach the best practice Antivirus profile to all security policy rules that allow traffic is to block known malicious files (malware, ransomware bots, and viruses) as they attempt to enter the network."
3) What would be the use case of enabling AV in a security policy for an app that is not HTTP, SMTP, IMAP, POP3, FTP, and SMB, if AV does not have a decoder for it?
Thanks.
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-28-2018 01:46 AM
Can anyone with experience on this assist with this query? Thanks.
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-28-2018 08:42 AM
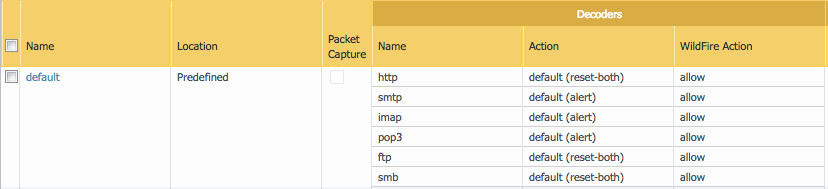
Ash83, we have the following Antivirus decoders (see picture below). If a security policy rule is not permitting http, smtp, imap, pop3, ftp, or smb traffic then there is no value in inspecting traffic using an Antivirus decoder. You've pretty much answered your own question. There is no harm in applying an AV Security Profile to a security policy rule that is not processing http, smtp, imap, pop3, ftp, or smb traffic as the decoder will never engage to inspect traffic if the traffic does not match one of these applications.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-04-2018 05:55 AM
Thanks bvandivier 🙂
Think it would be useful to update the admin guide, from the current "AV should be enabled "to all security policy rules that allow traffic", to "AV should be enabled to all security policy rules that allow traffic for Apps: HTTP, SMTP, IMAP, POP3, FTP, and SMB"
Cheers.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-04-2018 10:35 AM
You are mixing up 'applications' with 'protocols'.
For example, we have multiple apps that are not named web-browsing, that use the HTTP protocol and for which we can provide AV scanning.
To give you an example, when you say "AV should be enabled to all security policy rules that allow traffic for Apps: HTTP, SMTP, IMAP, POP3, FTP, and SMB", you are saying that HTTP is an app, and that is incorrect. We do not have an http app, the app is web-browsing.
This mixup is common with customers as well. If we documented "AV should be enabled to all security policy rules that allow traffic which use decoders: HTTP, SMTP, IMAP, POP3, FTP, and SMB", then that would be accurate, but would create a lot of confussion. You would be asking customers to be able to know which apps use which decoders.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-06-2018 09:05 AM
Thanks Mivaldi, great explanation.
I would personally prefer the admin guide to be as accurate as possible, to avoid any possible missunderstandings, and see the following sentence (as per your previous update): "AV should be enabled to all security policy rules that allow traffic which use decoders: HTTP, SMTP, IMAP, POP3, FTP, and SMB"
In order to complement that, and to have a complete picture, we (firewall admins) should ideally be also be able to see which decoder(s) is/are use per App. I do not think this is an option at the moment. I have not been able to find this information on applipedia. Is this information available somewhere else?
Thanks.
- 1 accepted solution
- 9455 Views
- 7 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- security profile malfunction detection in Threat & Vulnerability Discussions
- Thwarting the Theft of OAuth Session Tokens Using Secured Containerized Development Environments (CDEs) in Threat & Vulnerability Discussions
- Vulnerability protection in Threat & Vulnerability Discussions
- Zone protection flood thresholds in Threat & Vulnerability Discussions
- Reconnaissance Protection tresholds in Threat & Vulnerability Discussions