- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
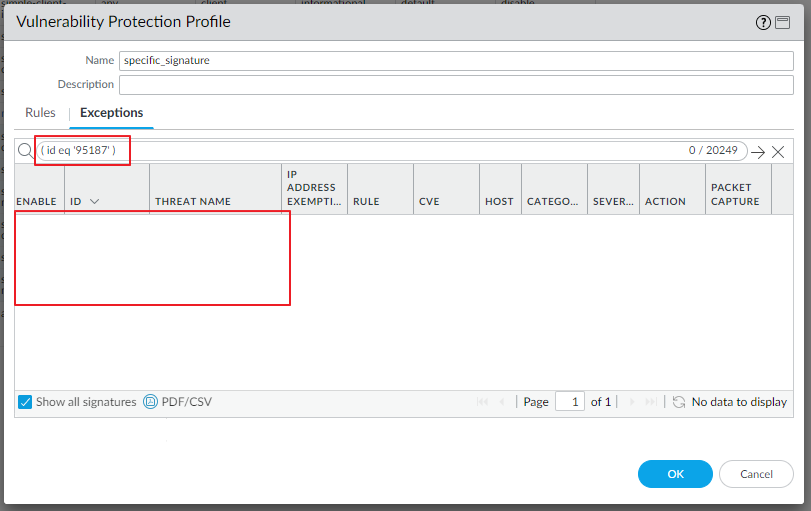
TID 95187 is not on my signature list
- LIVEcommunity
- Discussions
- Cloud Delivered Security Services
- Threat & Vulnerability
- Re: TID 95187 is not on my signature list
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-12-2024 02:12 AM
Hi,
The question is related to following vulnerability: https://security.paloaltonetworks.com/CVE-2024-3400
In this it said "Recommended Mitigation: Customers with a Threat Prevention subscription can block attacks for this vulnerability by enabling Threat ID 95187 (introduced in Applications and Threats content version 8833-8682)."
However, when I update content signature to the latest ( which is 8833-8682 ), and then try to create new vulnerability profile with specifying 95187 only, it does not shows me 95187.
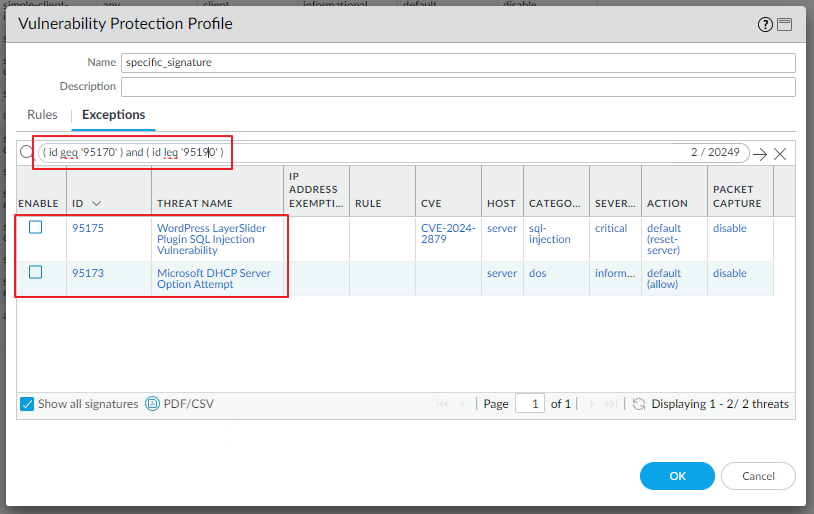
With ID range, the result is as below
I'm sure there is ID 95187 because I can check via CLI.
admin@PA-410> show system info | match app-version
app-version: 8833-8682
admin@PA-410> show threat id 95187
This signature detects malicious payload in HTTPS request.
critical
Unknown
https://docs.paloaltonetworks.com/pan-os/9-1/pan-os-admin/threat-prevention
admin@PA-410>
NOTE: I can replicate this condition with other platforms too.
How can I create this vulnerability profile for mitigation?
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-12-2024 04:41 AM
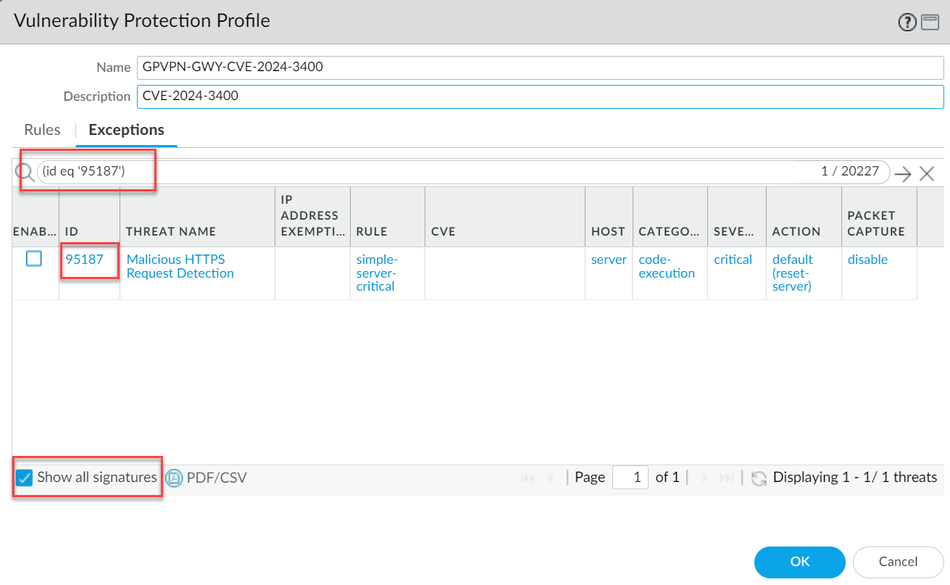
This is a GUI issue.
Once Applications and Threats content version 8833-8682 was installed, the signature (TID: 95187) is available on the firewall.
The severity of the signature is "Critical" and the default action is "reset-server". So, if you clone the strict/default vulnerability profile, or if you follow the best practice, then the signature is effective (enabled).
https://docs.paloaltonetworks.com/best-practices/internet-gateway-best-practices/best-practice-inter...
To fix the GUI issue, please try the followings and see if it works.
1. Go to "Device" -> "Dynamic Update" -> find the content version 'previously' installed -> "Revert"
2. Then, revert back to 8833
3. Refresh the browser page. (or try using another browser)
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-12-2024 03:41 AM - edited 04-12-2024 03:48 AM
I see the same thing.
Can someone confirm if this is is just cosmetic?
Because if you can't individually select the Threat ID, to me the question becomes:
If you create a Vulnerability Policy with the action 'reset-server' for ALL 'high' & 'critical' threat IDs, will the profile hit this 'hidden' threat or not?
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-12-2024 03:55 AM
Even I don't know this is cosmetic issue or not, I could find the way to show TID 95187.
Try following:
1. create sample profile from CLI. sample command is as below
# set profiles vulnerability "sampleconfig" threat-exception 95187 action reset-both
2. go back to your GUI. you can reuse "sampleconfig" profile or delete it if you don't need, then edit your existing profile with TID 95187
Even I could configure it, I still curious this protect my GP Gateway (hope this is cosmetic issue)
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-12-2024 04:17 AM
Thanks,
I can confirm your workaround works on a firewall (it didn't on the panorama)
It does look cosmetic but I have no way of testing it.
So, to be sure I went ahead and disabled Telemetry.
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-12-2024 04:41 AM
This is a GUI issue.
Once Applications and Threats content version 8833-8682 was installed, the signature (TID: 95187) is available on the firewall.
The severity of the signature is "Critical" and the default action is "reset-server". So, if you clone the strict/default vulnerability profile, or if you follow the best practice, then the signature is effective (enabled).
https://docs.paloaltonetworks.com/best-practices/internet-gateway-best-practices/best-practice-inter...
To fix the GUI issue, please try the followings and see if it works.
1. Go to "Device" -> "Dynamic Update" -> find the content version 'previously' installed -> "Revert"
2. Then, revert back to 8833
3. Refresh the browser page. (or try using another browser)
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-12-2024 05:14 AM
Tried on 2 different FWs.. same issue.. even the release notes does not state the threat ID
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-12-2024 05:20 AM
I've tried with the revert to the previously installed version and then got back to the 8833 and it didn't work in PAN-OS 10.2.7-h3 (I can't see the 8833 signatures in the GUI)
I could check in the GUI in a PAN-OS 10.1.6-h7 and the Threat ID is visible in the Vulnerability Profiles after receiving the 8833.
The TAC analyst indicates me the 8833 signatures are not visible in the GUI of 10.2 and above, and the way to confirm is the output of "show threat id 95187".
However, as some of you wrote in this post, I hope that is just a cosmetic issue because we don't know how can find out if it's working.
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-12-2024 05:34 AM
Did you also refresh the browser page or try another browser?
I could make it work in PAN-OS 10.2.7-h3.
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-12-2024 05:47 AM
You're right , I've tried some minutes ago and I can see the 95187 signature in PAN-OS 10.2.7-h3
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-12-2024 08:19 AM
running 11.1.2 and cant see the ID in pan or the firewall gui.
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-12-2024 09:21 AM
We see the required Vulnerability ID in all PA Firewalls that have at least A&T version 8833-868. Ultimately, this can be added to the policy already protecting a GPVPN Zone...although, having a Universal, new, Sec. Policy at the top, encompassing this CVE, might not be a bad additional protection layer.
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-12-2024 09:57 AM - edited 04-12-2024 09:58 AM
I tried the following, and it work for me.
1. download > install 8833-8682
2. download > install / revert to 8832-8674
3. Revert to 8833-8682
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-12-2024 11:36 AM
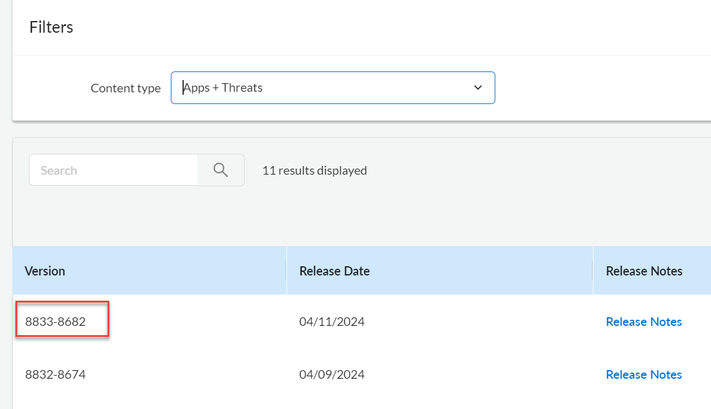
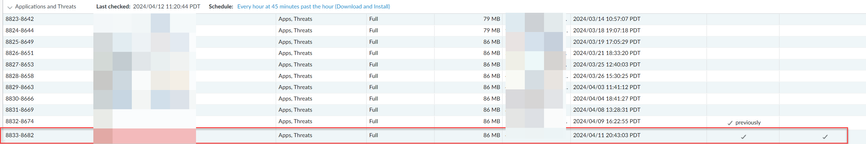
A good review. 👌 Although, we cannot see a reason to have "revert" A&T version as suggested to see the required CVE ID? The A&T version encompassing the required ID for this CVE, is already part of the latest, the only latest, A&T version available (as far as we can see in various support portals and Firewalls). If the PA is set to better practices, such as download & install A&T every 30-45 minutes (except for environments that needs to test all A&T versions before deployment), the CVE ID in question should already be available without any required "fix" or "revert." In fact, if the ID is missing, a manual install would be needed if the installed A&T version is not the latest shown .... as it seems to be the only latest A&T as of 11:00 PT today....so, if it's not already there, it should be installed, not reverted.
From the support portal:
From a PA Firewall:
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-12-2024 02:15 PM
We noticed this problem also on PanOS 10.2.6. We were able to see the Threat ID when opening a new in-private browser instance or having a colleague check for it. Seems to be cosmetic.
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-13-2024 11:28 AM
I had this issue on 10.2.7-h3, I installed 8834-8684 which came out yesterday and now its showing up in the Panorama Web GUI.
- 1 accepted solution
- 11953 Views
- 16 replies
- 1 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- TID 95187 is not on my signature list in Threat & Vulnerability Discussions
- EDL Dynamic Domain list that is allowed in Anti-spyware profile> DNS Polices is getting sinkholed in Threat & Vulnerability Discussions
- MineMeld sweet32/upgrade? in Threat & Vulnerability Discussions
- Community or News Group that has taken Snort signatures and converted them to PaloAlto in Threat & Vulnerability Discussions