- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Why there are 2 threats of same name but different severity
- LIVEcommunity
- Discussions
- Cloud Delivered Security Services
- Threat & Vulnerability
- Why there are 2 threats of same name but different severity
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-06-2017 01:48 PM
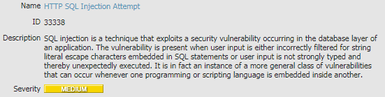
I see these alerts with same name and description, where as one is considered low and other as medium.
Why do they even have different ID's
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-24-2017 03:29 PM
They each have their own vulnerability signature, therefore a unique Threat ID. I see a total of 26 threats that are named "HTTP SQL Injection Attempt", 1-high, 23-medium, and 2-low in severity.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-24-2017 03:29 PM
They each have their own vulnerability signature, therefore a unique Threat ID. I see a total of 26 threats that are named "HTTP SQL Injection Attempt", 1-high, 23-medium, and 2-low in severity.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-30-2017 11:44 AM
So should blocking be done based on severity only?
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-30-2017 02:40 PM
I don't want to say based on severity "only", but for us it definitely helps simplify things so that everytime Palo Alto releases a new Threat ID we don't have to go configure a custom action for each one. We also don't feel comfortable using a default action of "alert" for a critical severity threat.
This is what we do... For critical, high, and medium threats we use "reset-both" action. For low threats we use "default" action (which uses the individual threat's action recommended by Palo Alto). For informational threats we use "allow" action. Then we use "exceptions" when we have a Threat ID we want configured differently than based on severity.
- 1 accepted solution
- 8031 Views
- 3 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Newsletter: Cloud Delivered Security Services, Oct-2025 in Advanced Threat Prevention Discussions
- Upgrade from Basic Threat Prevention to Advanced Threat Prevention in Advanced Threat Prevention Discussions
- Welcome to the Advanced WildFire Discussion Area! in Advanced WildFire Discussions
- Welcome to the Advanced Threat Prevention Discussion Area! in Advanced Threat Prevention Discussions
- Newsletter: Cloud Delivered Security Services, Aug-Sep, 2025 in Advanced WildFire Discussions