- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
How to check certificate expiration date from API or CLI?
- LIVEcommunity
- Community Legacy Content
- Automation / API
- Automation/API Discussions
- Re: How to check certificate expiration date from API or CLI?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-17-2021 09:53 AM
Hello all,
Do you know if it is possible to check certificate expiration date from API or CLI for Firewall and Panorama.
Ideally also get all the certificate details. I haven't found a way.
Thanks
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-19-2021 09:14 AM
And the equivalent XML API call:
https://{{host}}/api?key={{key}}&type=op&cmd=<show><sslmgr-store><config-certificate-info></config-certificate-info></sslmgr-store></show>
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-19-2021 03:34 AM
Hi there,
On the firewall CLI try show sslmgr-store config-certificate-info will give you certificate details including expiry dates.
cheers,
Seb.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-19-2021 07:47 AM
Thank you.
Awesome, that's was exactly what I was looking for.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-19-2021 09:14 AM
And the equivalent XML API call:
https://{{host}}/api?key={{key}}&type=op&cmd=<show><sslmgr-store><config-certificate-info></config-certificate-info></sslmgr-store></show>
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-07-2021 02:03 AM
Hi,
I not found a sslmgr-store option on my panorama
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-07-2021 02:59 AM
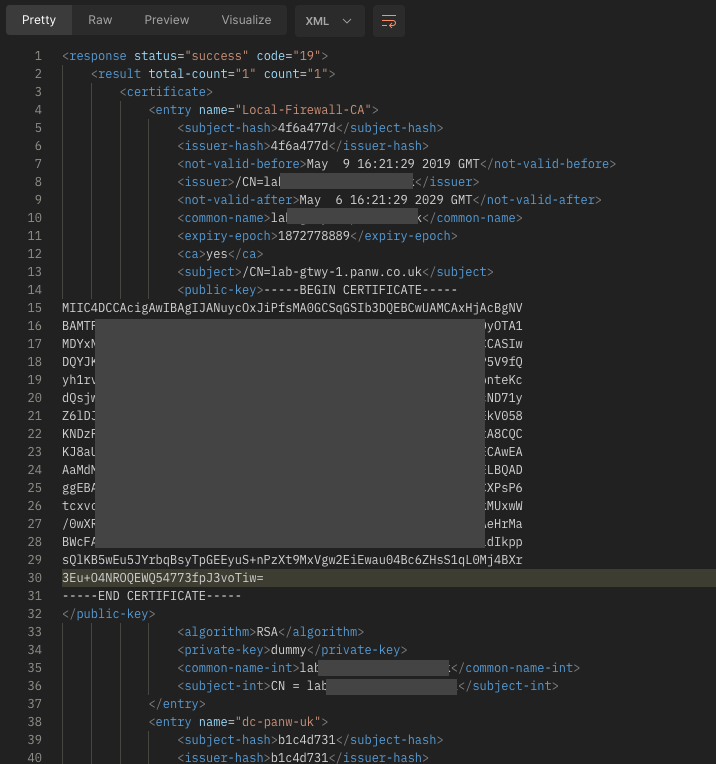
Hi @efurlan, another method is to look at the config, such as this example API call:
https://{{host}}/api/?key={{key}}&type=config&action=get&xpath=/config/devices/entry[@name='localhost.localdomain']/template/entry[@name='{{template-name}}']/config/shared/certificate
The response includes the expiry (and begin) dates:
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-07-2021 03:08 AM
You could also do the sslmgr command on a managed-firewall via Panorama:
https://{{host}}/api?key={{key}}&type=op&cmd=<show><sslmgr-store><config-certificate-info></config-certificate-info></sslmgr-store></show>&target={{ngfw-serial-number}}
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-05-2022 07:33 AM
Hi Jymmy,
Thank you for the post, I'm using exactly what you posted but looks like it does not send the certificate's name in the response. Do you have any suggestions about how to get a list of SSL Certificates installed?
Response:
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-07-2022 01:10 AM
Hi @FabioSouza, which command are you using, how are you using it (Postman, curl, etc), and is it to Panorama or NGFW directly?
It looks like you are using the "sslmgr-store" command from earlier in the thread, but maybe try the config command later in the thread (here) which includes certificate names in the response.
https://{{host}}/api/?key={{key}}&type=config&action=get&xpath=/config/devices/entry[@name='localhost.localdomain']/template/entry[@name='{{template-name}}']/config/shared/certificate- Mark as New
- Subscribe to RSS Feed
- Permalink
04-07-2022 01:51 AM
Sharing a script that utilises the Python API for anyone that may be interested.
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-07-2022 09:30 AM
@JimmyHolland I have the same question actually but I'm wondering what values do I need to substitute for the values I underlined below:
https://{{host}}/api/?key={{key}}&type=config&action=get&xpath=/config/devices/entry[@name='localhost.localdomain']/template/entry[@name='{{template-name}}']/config/shared/certificate
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-08-2022 05:06 AM
Hi @TigeRRR,
Good question. In my notation, anything inside {{ braces like this }} means replace with your own value.
- [@name='localhost.localdomain'] stays the same, this is a static value the same on every device.
- {{template-name}} is the name of your Panorama template where you are modifying certs or gathering cert info. My response was to someone asking about Panorama specifically.
Hope that helps?
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-08-2022 07:23 AM
Thank you! I understood that it was to be your own values but I wasn't sure what it was referring to, what if this was to be pulled directly from a firewall and not Panorama?
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-12-2022 05:50 PM
Hi guys,
this is a really great thread and I thank you all for your inputs.
I'm currently trying to develop a certificate expiry monitoring solution for the 'default trusted certificate authorities'.
All the provided paths in this thread relate to the 'device certificates' only.
I believe I require a path that would access 'default trusted certificate authorities' on vsys1.
Could someone please point me in the right direction on how I could achieve this?
It's been a frustrating process thus far, so any direction will be much appreciated.
Thanks guys!
- 1 accepted solution
- 45436 Views
- 23 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Ansible PFX Cert Upload not adding key in Automation/API Discussions
- Facing Error - [SSL: CERTIFICATE_VERIFY_FAILED] certificate verify failed (_ssl.c:618) in Automation/API Discussions
- Api check certificate validity in Automation/API Discussions
- How to check certificate expiration date from API or CLI? in Automation/API Discussions
- Fix not publicly-trusted certificate on gpcloudservice API in Automation/API Discussions