- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
How to parse op(cmd) results
- LIVEcommunity
- Community Legacy Content
- Automation / API
- Automation/API Discussions
- Re: How to parse op(cmd) results
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-25-2020 09:21 PM - edited 03-25-2020 09:23 PM
I am new to python. I am able to get results using op() method but not able to display or parse them to use meaningfully.
fw = pandevice.base.PanDevice('10.10.10.10',api_key='abcdefgh')
fwcmd = fw.op(cmd='show global-protect-gateway current-user',xml=True)
print(type(fwcmd),"\n\n")
print(fwcmd)
the result this yields is like
<class 'bytes'>
b'<response status="success"><result>\n\t<entry>\n\t\t<domain>abc</domain>\n\t\t<islocal>no</islocal>\n\t\t<username>xyz....................
I would want a result that looks something like this and be able to easily operate on those results.
Person ID: system
hostname: ABC-PAN
ip-address: 10.10.10.10
public-ip-address: unknown
netmask: 255.255.2255.0
default-gateway: 10.10.10.1
is-dhcp: False
ipv6-address: unknown
++
Above results i got using
import pandevice
from pandevice import base
fw = pandevice.base.PanDevice('10.10.10.10',api_key='abdefgh')
jpfw = fw.show_system_info()
for p_id, p_info in jpfw.items():
print("\nPerson ID:", p_id)
for key in p_info:
print(key + ':', p_info[key])
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-27-2020 06:40 AM
5 days for this small piece of code...might not be the best way...but got it working as i would like it to...and can now use it possibly for something
import pandevice
from pandevice import base
import xml.etree.ElementTree as ET
fw = pandevice.base.PanDevice('10.10.10.10',api_key='abcdefgh')
fcmd = fw.op(cmd='show global-protect-gateway current-user',xml=True)
str_xml = str(fwcmd,encoding='utf-8')
#print(str_xml)
xml_parser = ET.XMLParser()
xml_tree = ET.ElementTree(ET.fromstring(str_xml,xml_parser))
xml_root = xml_tree.getroot()
for elem in xml_root.iter():
if elem.tag != 'entry' and elem.tag != 'response' and elem.tag != 'result':
print(elem.tag,': ',elem.text)
else:
print('')
result looks like this where elem.tag is the string on left and elem.text is the string on right of ':'
domain : abc
islocal : no
username : xyz
primary-username : abc\xyz
computer : C_NAME
client : Microsoft Windows 10 Home , 64-bit
vpn-type : Device Level VPN
virtual-ip : 10.1.1.1
virtual-ipv6 : ::
public-ip : 2.2.2.2
public-ipv6 : ::
tunnel-type : SSL
public-connection-ipv6 : no
login-time : Mar.27 06:31:46
login-time-utc : 1585315906
lifetime : 7200
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-27-2020 06:40 AM
5 days for this small piece of code...might not be the best way...but got it working as i would like it to...and can now use it possibly for something
import pandevice
from pandevice import base
import xml.etree.ElementTree as ET
fw = pandevice.base.PanDevice('10.10.10.10',api_key='abcdefgh')
fcmd = fw.op(cmd='show global-protect-gateway current-user',xml=True)
str_xml = str(fwcmd,encoding='utf-8')
#print(str_xml)
xml_parser = ET.XMLParser()
xml_tree = ET.ElementTree(ET.fromstring(str_xml,xml_parser))
xml_root = xml_tree.getroot()
for elem in xml_root.iter():
if elem.tag != 'entry' and elem.tag != 'response' and elem.tag != 'result':
print(elem.tag,': ',elem.text)
else:
print('')
result looks like this where elem.tag is the string on left and elem.text is the string on right of ':'
domain : abc
islocal : no
username : xyz
primary-username : abc\xyz
computer : C_NAME
client : Microsoft Windows 10 Home , 64-bit
vpn-type : Device Level VPN
virtual-ip : 10.1.1.1
virtual-ipv6 : ::
public-ip : 2.2.2.2
public-ipv6 : ::
tunnel-type : SSL
public-connection-ipv6 : no
login-time : Mar.27 06:31:46
login-time-utc : 1585315906
lifetime : 7200
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-27-2020 07:04 AM
Glad you got it working! fw.op() will return an xml.etree.ElementTree by default, so turning it into a string and then having to re-parse it is a (small) waste. You're using a PanDevice object instead of the Firewall object, so I'd recommend changing that for clarity's sake. Then lastly you know what the result looks like, so you can use xml.etree.ElementTree.findall() to get there directly:
from pandevice.firewall import Firewall
import xml.etree.ElementTree as ET
fw = Firewall('10.10.10.10', api_key='abcdefgh')
result = fw.op(cmd='show global-protect-gateway current-user')
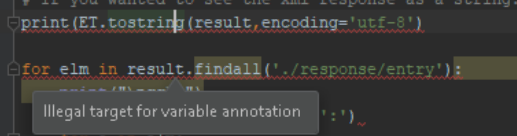
# If you wanted to see the xml response as a string:
# print(ET.tostring(result, encoding='utf-8')
for elm in result.findall('./response/entry'):
print(elm.attrib['name'] + ':')
for e in elm:
print(e.tag + ': ' + e.text)
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-27-2020 10:11 PM - edited 03-27-2020 10:24 PM
@gfreeman i tried your code but it did not work for me. I tried to check if event the for loop gets executed it did not print 'TEST'.
ET does not seem to like tostring/findall
fw = Firewall('10.10.10.10',api_key='abcdefgh')
result = fw.op(cmd='show global-protect-gateway current-user')
print(type('result\n'))
# If you wanted to see the xml response as a string:
#print(ET.tostring(result, encoding='utf-8')
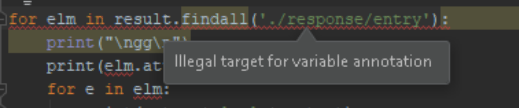
for elm in result.findall('./response/entry'):
print("\nTEST\n")
print(elm.attrib['name'] + ':')
for e in elm:
print(e.tag + ': ' + e.text)
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-29-2020 11:10 PM
Oops: './response/entry' should be './result/entry' and it should work.
I can't see what the code looks like above the print statement, but make sure you've removed xml=True from the fw.op(). You want xml=False (the default) because you want fw.op() to return an ElementTree, not a string or bytes or whatever.
- 1 accepted solution
- 6579 Views
- 4 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!