- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Rule Hit Count in BPA Report
- LIVEcommunity
- Community Legacy Content
- Best Practice Assessment
- Best Practice Assessment Blogs
- Rule Hit Count in BPA Report
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Printer Friendly Page
A New Feature in the Best Practice Assessment (BPA)
We have recently added a new feature in the BPA tool to process rule hit count (rules that have traffic flowing).
What is the Rule Hit Count?
You can now filter your security policies in the BPA to see only policies that are passing traffic. You can also see when the rule was last hit and the policies with the most traffic. If a security policy has not been used for the last 90 days, then we suggest it is an unnecessary policy. If that policy is weak, then it is a compromise to the network and should be deleted.
Who can access the Rule Hit Count?
All customers with firewalls on PAN-OS 9.0 or later running a BPA report will see this feature.
Why is the Rule Hit Count important?
It can be challenging to increase your adoption of capabilities on security policies when you have multiple firewalls and multiple security policies within each of these firewalls. Often there are security policies in the rulebase that are not being used for extended periods. These policies may have been added for various reasons, such as temporary rules or rules migrated from previous devices but are no longer necessary.
To ensure the most effective adoption of capabilities, we should focus feature adoption on necessary policies and the policies with the most traffic rather than waste time adding capabilities on unused policies. The new Rule Hit Count feature provides easy visibility only into the security policies that are passing traffic. The focus can then be on securing these policies.
How do we secure these policies?
The first step is to increase the adoption of various capabilities on security policies via App-ID adoption, credential phishing capability within a URL Filtering profile, IPS features such as anti-virus, anti-spyware, and vulnerability protection, WildFire, and others.
Example – Traffic Hit Rule
In the example below, we can see where to find the option to select only security policies that are passing traffic via "Enable Traffic Hit Rules (Last 90 days)." (see Figure 1)
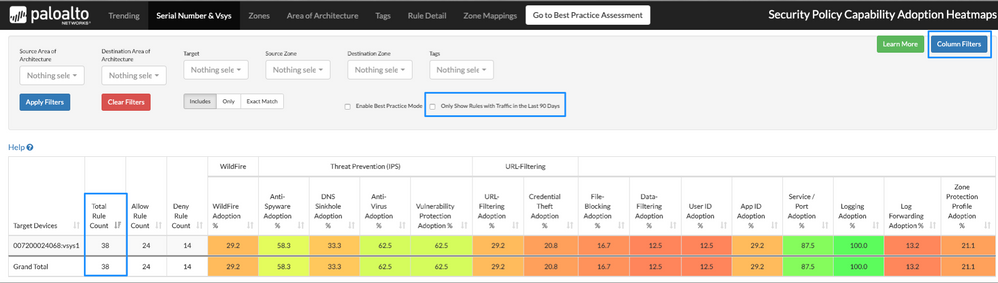
Initially, the total rule count is 38, and there are 24 allow rules. (see Figure 2)
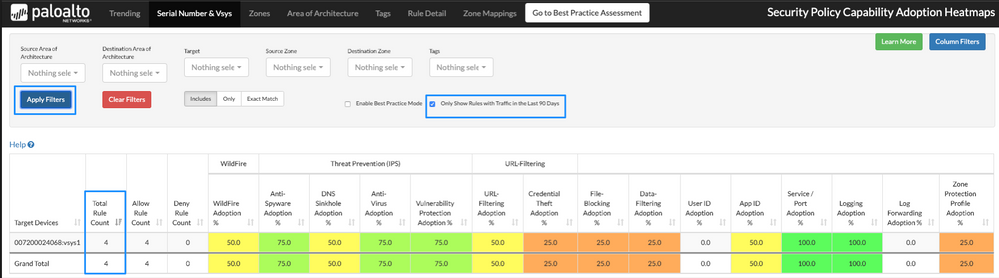
Once we select the checkbox for “only show rules with traffic in the last 90 days,” the number of rules decreases to four. This indicates that only four rules are actually passing traffic. We can now focus on increasing capability adoption on those four rules.
Zones Tab View
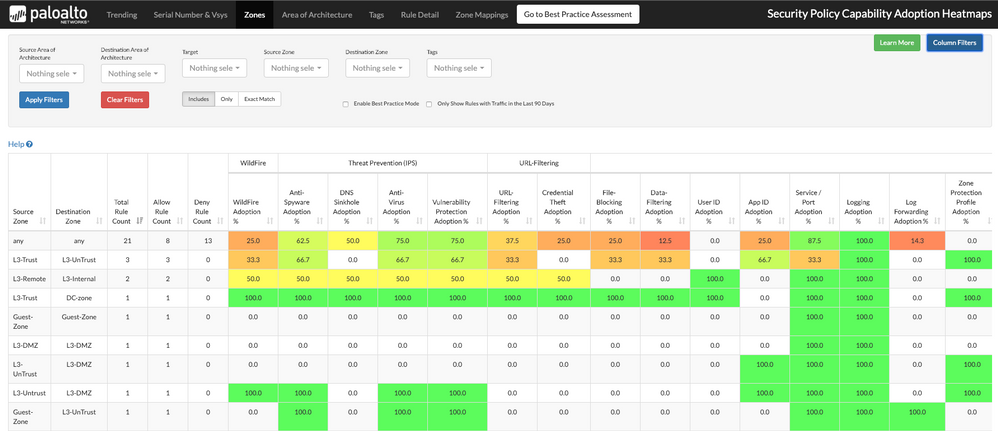
In a different view under the Zones tab, you may also see how it looks before applying the filter "Enable Traffic Hit Rule (Last 90 days)." (see Figure 3)
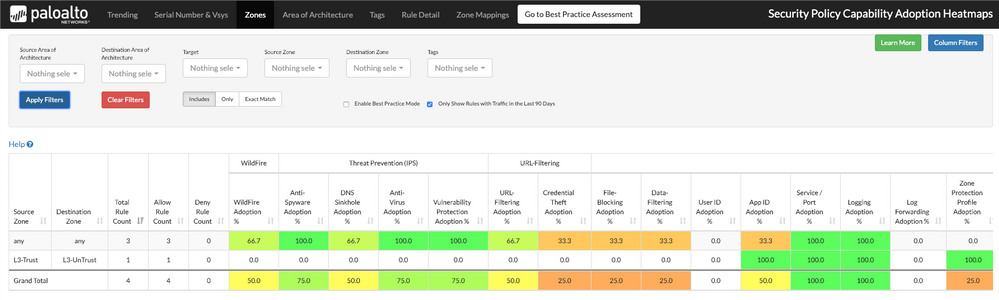
Shown below, is how the results will look after applying the filter. (see Figure 4)
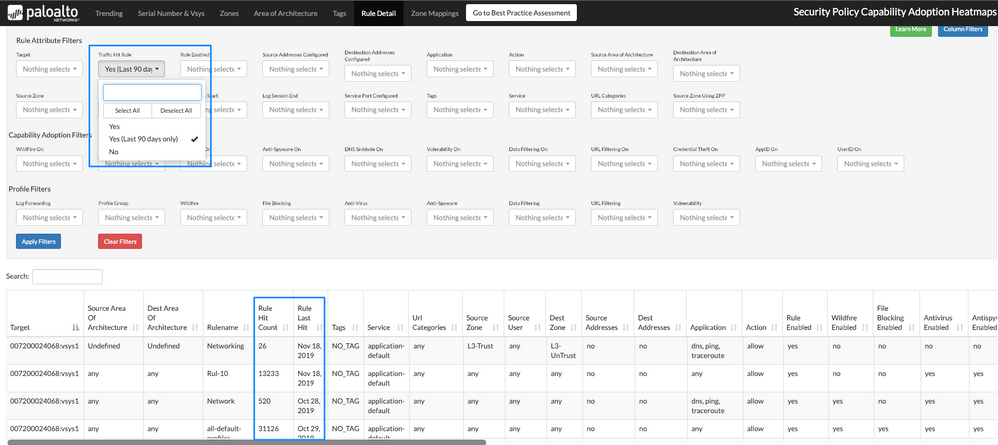
Rule Detail Tab
We can also use the "Rule Detail" tab to use filters and identify all security policies that have rule hits. We added two new columns for Rule Hit Count and Rule Last Hit, which help identify unused rules with a hit count being zero. If the rule has been used, we can see the last time they have been hit and when traffic has been flowing through it. (see Figure 5)
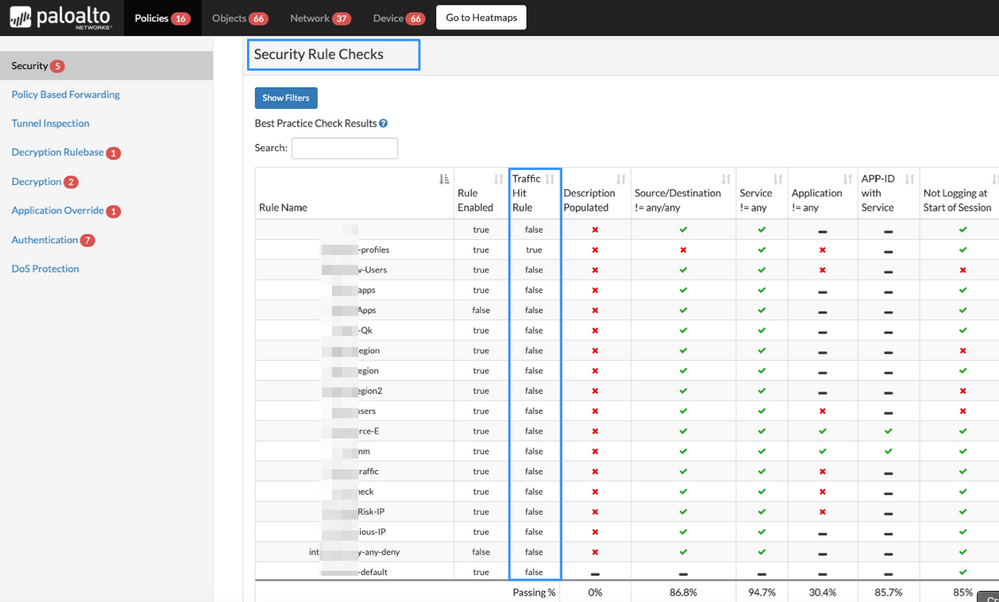
We have also added a new column in the BPA report for Security Rule Checks to identify rule hit policies and different best practice checks that needs to be reviewed. To find it, go to Component > Policies > Security Rule Checks. (see Figure 6)
- 4614 Views
- 0 comments
- 3 Likes
-
Best Practice
1 -
Best Practice Assessment
12 -
Best Practices
1 -
BPA
13 -
Community
1 -
Firewall
1 -
NGFW
1 -
Panorama
1 -
Tools
1 -
URL Filtering
1 -
Zero Trust
1
- Best Practice Assessment Executive Summary Overview in Best Practice Assessment Blogs
- Configuration Wizard Release Notes Version 1.4.0 in Configuration Wizard Release Notes
- Configuration Wizard Release Notes Version 1.3.0 in Configuration Wizard Release Notes
- Configuration Wizard Additional Best Practice Checks Support (Version 1.1.0) in Configuration Wizard Frequently Asked Questions
- BPA Release Notes v5.1 in Best Practice Assessment Release Notes




