
- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
At Palo Alto Networks, we’ve just announced the integration between the VM-Series virtual firewall and the new Oracle Cloud Infrastructure (OCI) Flexible Network Load Balancer. This powerful integration unleashes scalable and high-performance security for customers without complexities that traditionally come with inserting third-party virtual appliances in public cloud environments.
I’ll deep dive into challenges that normally come with deploying third-party appliances in public clouds and how this integration and how the integration with OCI addresses these problems.
The VM-Series virtual firewall delivers prevention-based protection for workloads, applications, and data on OCI. VM-Series augments OCI native network security controls by protecting against exploits, malware, known and unknown threats, and data exfiltration.
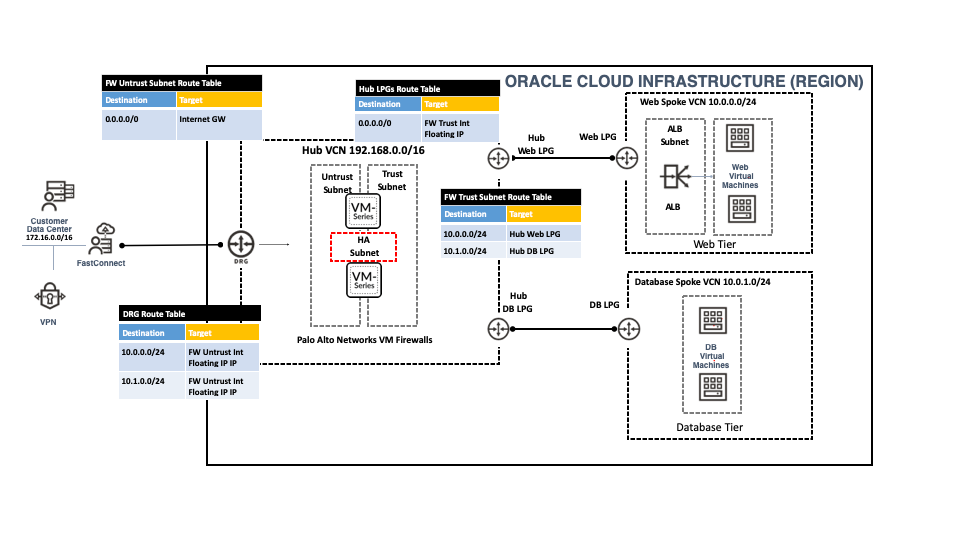
Until now, most customers deployed VM-Series in Active-Passive HA mode in every Application OCI Virtual Cloud Network (VCN) where applications reside. Another option was to deploy VM-Series into its own VCN. To protect traffic between application VCNs, administrators could route inter-VCN traffic to the VM-Series VCN. This design, recommended by Palo Alto Networks, is known as the Hub and Spoke configuration and is shown in figure 1. In either architecture design, only one VM-Series firewall is active in a VCN.
While this method has effectively protected applications and data on OCI, it introduced challenges which required customers to make two trade-offs:
Trade-off #1 - Scale & Performance
This option limits customers to scale beyond a single active VM-Series firewall Per OCI Availability Domain to route the traffic through the VM-Series firewall for Outbound and East-West traffic.
Trade-off #2 - Configuration Complexities
The customer has to manage the life cycle and policy of VM-Series running in each application VCN. Also beside that they have to maintain dynamic groups and policies to support Active-Passive HA configuration.
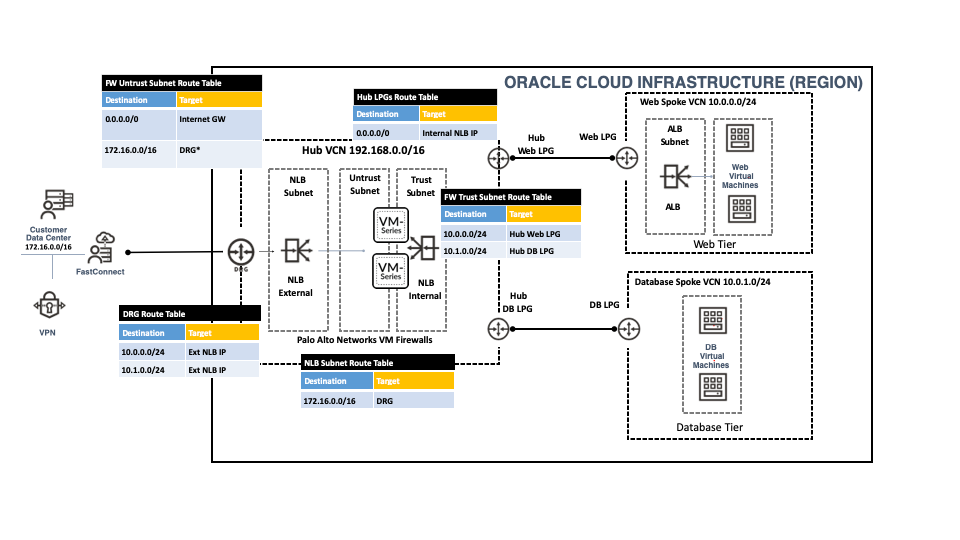
With the OCI Flexible Network load balancer launch, customers can now deploy and scale VM-series firewalls on OCI.
The OCI Flexible Network Load Balancer is a non-proxy load balancing solution that performs pass-through load balancing of layer 3 and layer 4 (TCP/UDP/ICMP) workloads. It offers an elastically scalable regional VIP address that can scale up or down based on client traffic with no minimum or maximum bandwidth configuration requirement. Additionally, it provides the benefits of flow high availability, source/destination IP address, and port preservation.
The integration between the OCI Flexible Network LoadBalancer and VM-Series firewall will alleviate the above tradeoff concerns. Customers will be able to deploy VM-Series in Active-Active mode behind a single regional IP address, simplify their network connectivity and automate network security at scale. It will also enable customers to manage firewalls and security policies centrally. With this integration, customers still take advantage of the great capabilities offered by VM-Series including layer 7 visibility and threat protection for both encrypted and unencrypted traffic.
Figure 2 illustrates how using the OCI Flexible Network Load Balancer integration with VM-Series simplifies your OCI Hub and Spoke environments. You can continue to use a centralized security VCN as you did previously. But now, you can leverage the OCI FLexible Network LoadBalancer to scale and load-balance traffic across the stack of VM-Series firewalls in your centralized security VCN.
The VM-Series firewall integration with OCI Flexible Network Load Balancer offers the following benefits:
With the new integration between VM-Series firewall and the OCI Flexible Network Load balancer, customers can augment cloud network security with three use cases:
To get hands-on experience with this integration, try out VM-Series in your OCI environment from our Oracle Cloud Marketplace listing and learn how to configure VM-Series with the flexible network load balancer.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
| Subject | Likes |
|---|---|
| 2 Likes | |
| 2 Likes | |
| 2 Likes | |
| 1 Like | |
| 1 Like |




