
- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
When responding to a security incident, triage, analysis, enrichment and remediation all can be time consuming and error prone processes, especially when responding and managing these attacks requires security teams to reconcile data from multiple sources. Often, by doing so, valuable time is lost shuttling between screens and executing repeatable tasks while an attack continues to manifest.
Today we’ll look at how SOC teams are able to utilize the best of both XDR’s extended endpoint threat detection and response with XSOAR’s workflow automation, orchestration and threat intelligence capabilities to become more effective using the Palo Alto Networks Cortex XDR — Investigation and Response content pack.
Cortex XDR is a detection and response platform that natively integrates network, endpoint, and cloud data to stop sophisticated attacks. By standardizing the XDR incident response and automating response with the Cortex XDR — Investigation and Response content pack, Cortex XSOAR decreases the mean time to detect by automating the collection of enrichment data, and providing centralized tracking. The pack includes out-of-the-box Cortex XDR incident type views with incident fields and layouts to aid analyst investigations, which are all easily customizable to suit the needs of each unique organization.
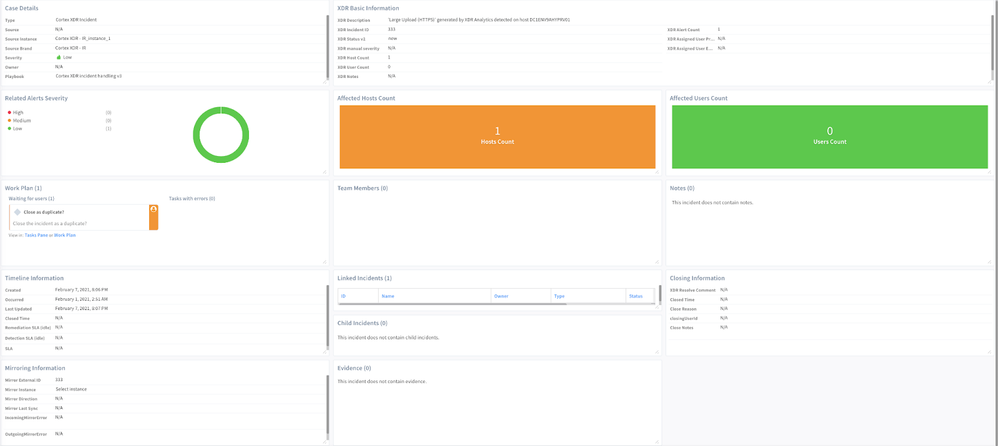
This content pack contains the Palo Alto Networks Cortex XDR Investigation and Response integration that enables direct execution of Cortex XDR actions within Cortex XSOAR. It also performs bidirectional incident updates between Cortex XDR and Cortex XSOAR. Plus, it enables the following workflows:
For more details on all the different playbooks options available within the XDR and XSOAR content pack, check out the blog “XDR + XSOAR: A Dynamic Duo”.
The playbooks included in this pack help you save time and keep your incidents in sync. They also help automate repetitive tasks associated with Cortex XDR incidents, such as:
It is without a doubt that the Cortex portfolio of products is designed to make the life of a security analyst better, faster and more efficient when it comes to detecting and responding to today’s security threats. The beautiful thing about the Cortex family of products is the ability to use each platform in conjunction with one another for maximum results.
Watch the video below for a detailed overview of the XDR and XSOAR Integration. For more information on the Cortex XDR Content Pack, visit our Cortex XSOAR Developer Docs.
Don’t have Cortex XSOAR? Download our free Community Edition today to test out this playbook and hundreds more automations for common use cases you deal with daily in your security operations or SOC.
Please Suggest Other Ideas or Vote!
If you like these ideas or would like to suggest other ideas, please collaborate with us through the Cortex XSOAR Aha page.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
| Subject | Likes |
|---|---|
| 2 Likes | |
| 1 Like | |
| 1 Like | |
| 1 Like | |
| 1 Like |
| User | Likes Count |
|---|---|
| 3 | |
| 2 | |
| 1 | |
| 1 | |
| 1 |




