- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Quarantine not working
- LIVEcommunity
- Discussions
- Security Operations
- Cortex XDR Discussions
- Re: Quarantine not working
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-23-2020 09:52 AM
Hi Team
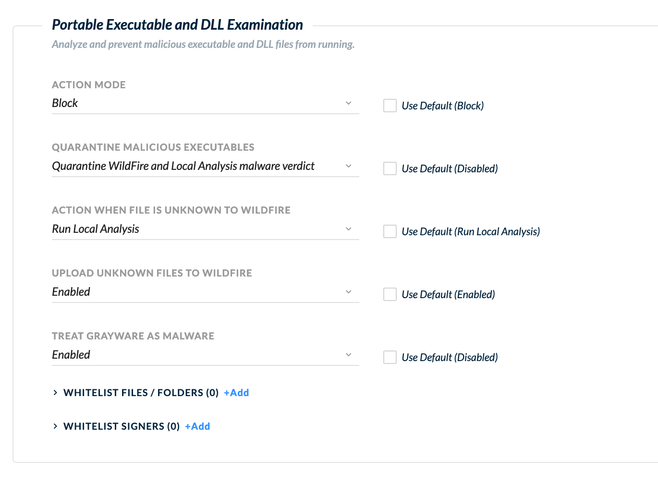
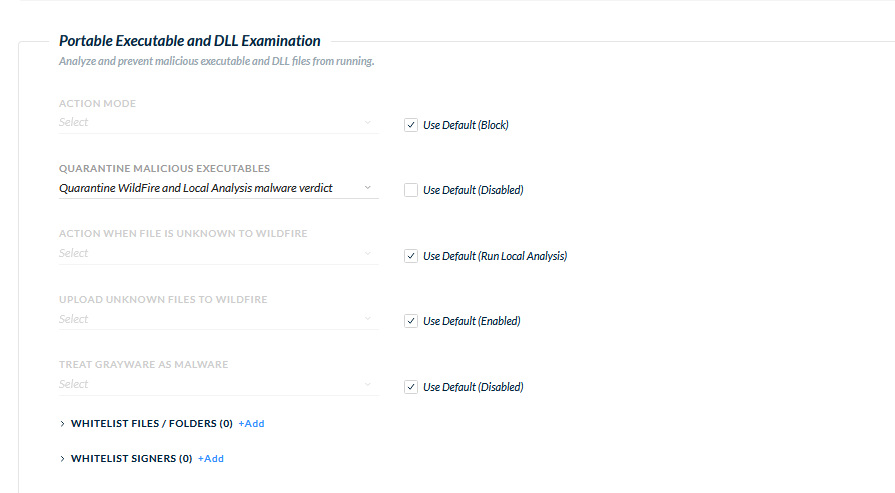
We have enabled quarantine for wildfire and local analysis malware verdict. When initiating malware scan from cortex xdr cloud t, the malware's are getting detected and but those are not getting quarantined.Can anyone advice is this how it works?
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-26-2020 11:05 AM
Next thing I would check is the agent logs after a quarantine attempt.
You can use this test PE to trigger a quarantine event. After the event is complete, open the log file, scroll to the bottom and look for any messages associated with the quarantine attempt.
David Falcon
Senior Solutions Architect, Cortex
Palo Alto Networks®
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-26-2020 10:27 AM
Can you post a screenshot of the Portable Executable and DLL Examination portion of your malware profile?
David Falcon
Senior Solutions Architect, Cortex
Palo Alto Networks®
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-26-2020 10:55 AM
Hi @Marsooq_A-
Just to confirm. When you go to Endpoint Management > Endpoint Administration, select an endpoint that is failing, right-click and select View Endpoint Policy -- can you see the profile with quarantine enabled applied to the specific machine?
David Falcon
Senior Solutions Architect, Cortex
Palo Alto Networks®
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-26-2020 11:02 AM
Yes , I could see the same profile in the policy and this has been confirmed several times.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-26-2020 11:05 AM
Next thing I would check is the agent logs after a quarantine attempt.
You can use this test PE to trigger a quarantine event. After the event is complete, open the log file, scroll to the bottom and look for any messages associated with the quarantine attempt.
David Falcon
Senior Solutions Architect, Cortex
Palo Alto Networks®
- 1 accepted solution
- 7878 Views
- 6 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Need help on this XSOAR Weird behavior on preprocessing scripts in Cortex XSOAR Discussions
- Fetched Integrations Objects in XSIAM 3.4 in Cortex XSIAM Discussions
- Sum number field in Cortex XSOAR Discussions
- Playbook stuck after upgrade in Cortex XSOAR Discussions
- XSIAM Dashboard in Cortex XSIAM Discussions