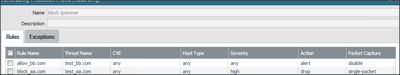
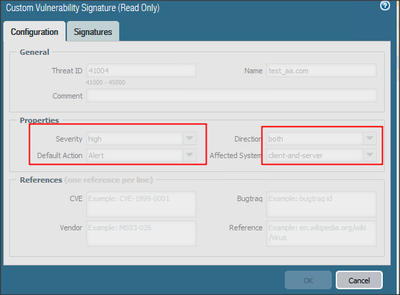
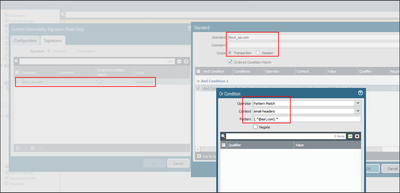
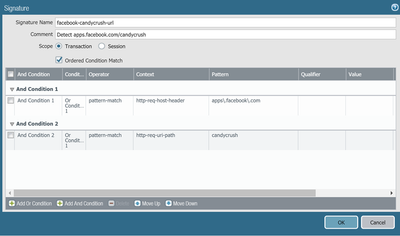
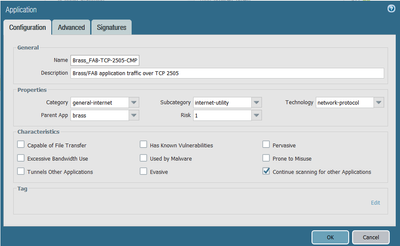
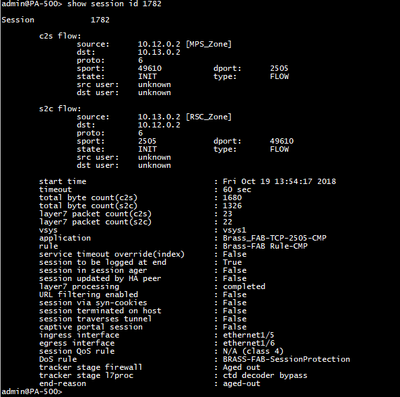
Welcome to the Custom Signatures discussion forum. This forum exists as a resource for security professionals to discuss the creation process of custom signatures in their PAN-OS appliance. Please feel free to engage with other community members and Palo Alto Networks staff. Ideas, questions, research, and observations regarding the process of custom signature creation are all actively encouraged.
For an introduction to the forum, please see the sticky!
Disclaimer:
This forum is provided for Live Community members to discuss and share information pertaining to custom signatures. Please use the information from this forum at your own risk and make sure to test and verify any signature and code presented here. For information on contacting Palo Alto Networks support, click here.