- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Custom Signature to detect a PDF file
- LIVEcommunity
- Discussions
- Custom Signatures
- Re: Custom Signature to detect a PDF file
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Custom Signature to detect a PDF file
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-06-2019 06:13 AM
DISCLAIMER:
As with all custom signatures on this forum, this signature is being provided by the author as a result of enthusiasm for the product and to share ideas with the Palo Alto Networks security community.
It is:
- Not recommended for deployment in a production network of any kind without internal testing.
- Not a solution to any vulnerability.
- Not an official supported Palo Alto Networks signature
This write up is to help the Palo Alto Networks community with detecting a specific PDF file.
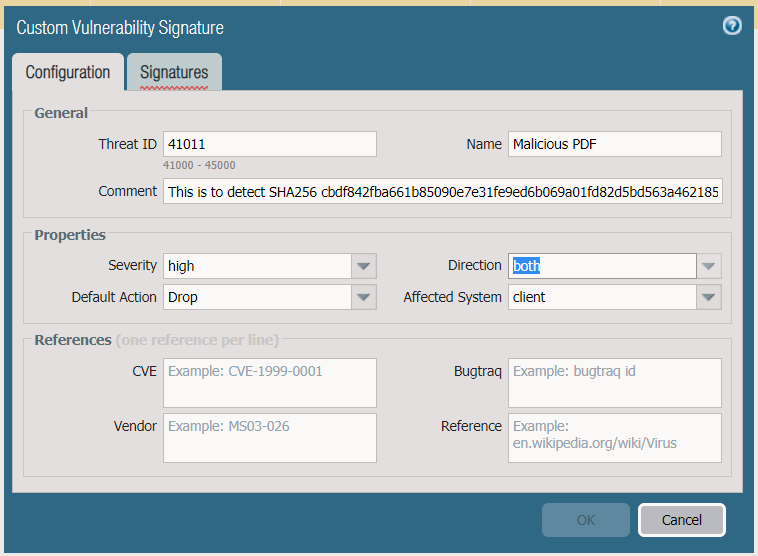
The sample signature was created on PAN OS Version 8.1.x :
SHA256: cbdf842fba661b85090e7e31fe9ed6b069a01fd82d5bd563a462185b53ab38e3
Go to custom signatures under objects, select custom vulnerability signature. Click add
Fill out the appropriate field under the configuration tab
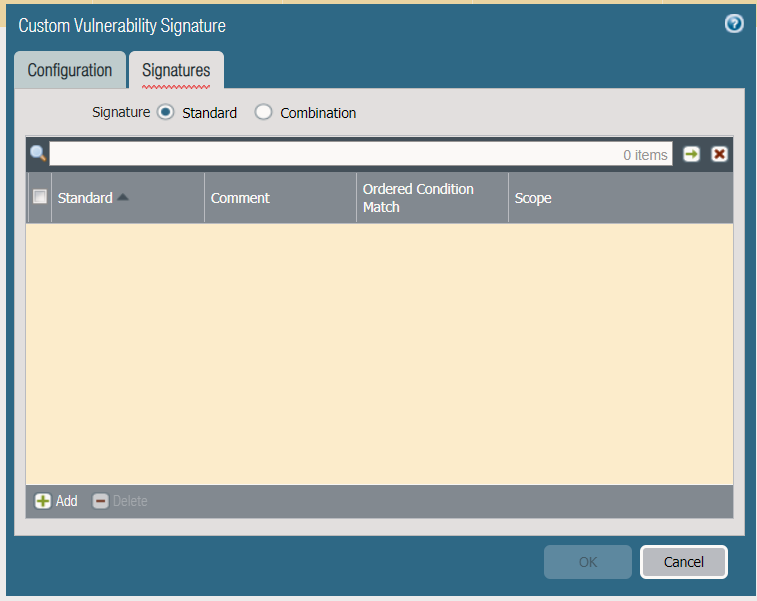
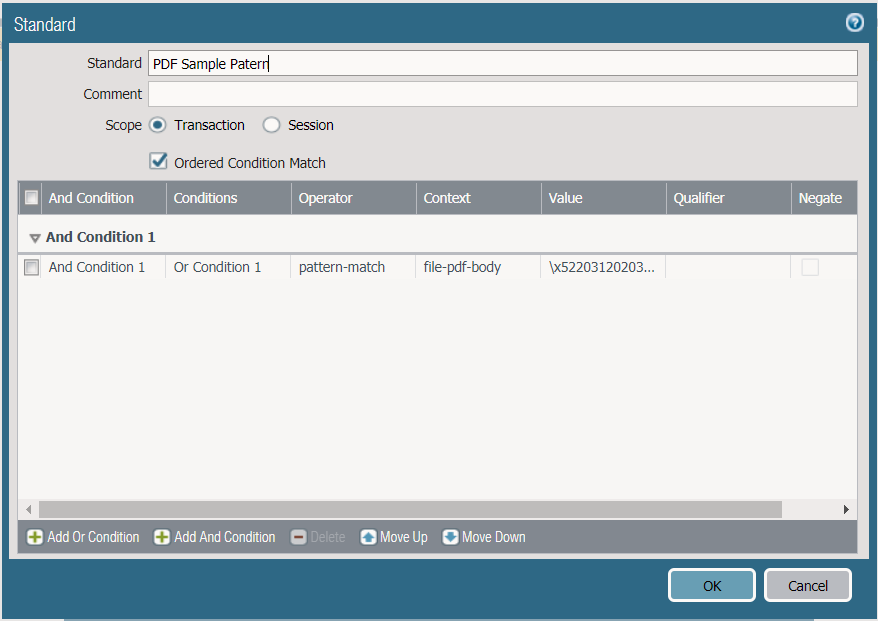
Open the Signature Tab
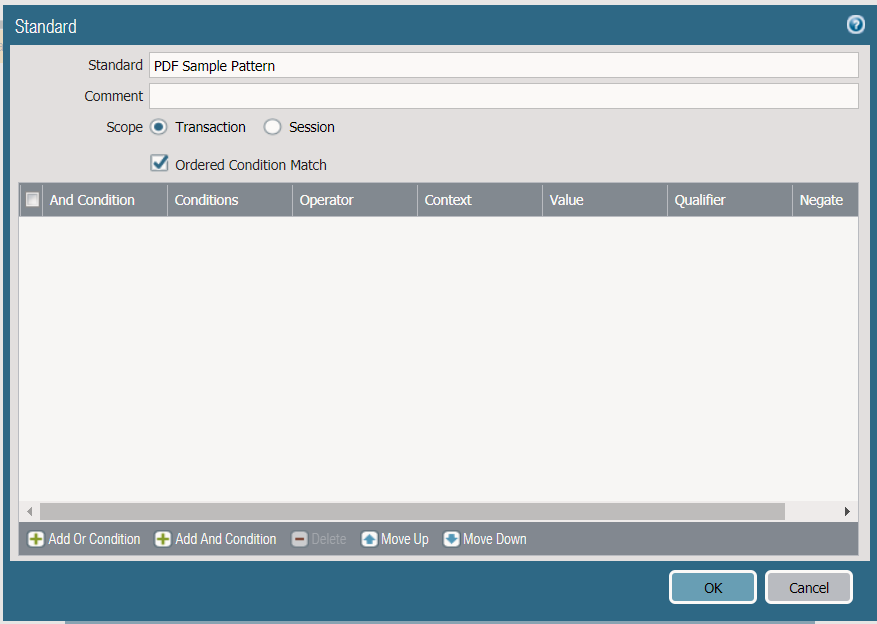
Select add at the bottom left
Since we only have one condition it doesn’t matter if we choose the ‘and’/’or’ condition
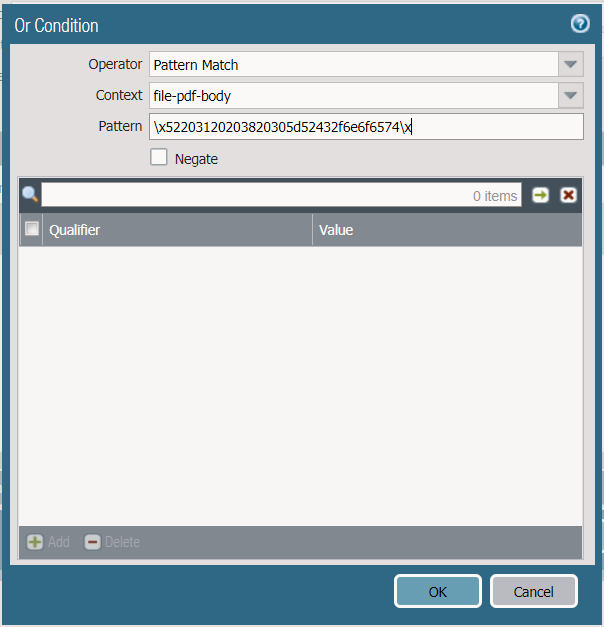
To determine a unique string the *NIX utility xxd was used in this case, however any hex editor will work for this purpose. The string was then converted to hex and used in a pattern match to detect the file. In this case the author of the file put what we believe to be their name in the file and that was used as a unique identifier.
5220 3120 2038 2030 5d52 432f 6e6f 6574
Once this custom signature is applied and a web browser is used to attempt to download the file the firewall will either block or alert on detection depending on the action you set.
**Warning** any custom signature should be fully tested to see if it works correctly, and for false positives.
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-25-2019 06:24 AM
dpharis, on another post it was stated that Palo Alto does not do signatures for specific hashes since the same malware can/will use different hashes. My question is if my org decides to do custom sigs for specific hashes, will it eventually hamper/degrade FW's performance say, after a couple thousand signatures?
Thanks!
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-25-2019 07:00 AM
Hello Bart,
Your research is correct. We do not create signatures for specific hash values because it is both inefficient, and easily bypassed with a minimal change to the original file.
The performance impact is difficult to determine in a hypothetical situation due to the limitless environmental variables. The short answer though is yes, there will be an impact to utilizing large numbers of custom signatures. If you intend to block a large number of files using customer signatures, instead of using hashes, we suggest you identify a unique character string in the file and utilize if after thorough testing, as this improves your changes of catching multiple variants of the same malware.
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-25-2019 07:13 AM
Copy that. Appreciate your quick reply!
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-23-2021 12:03 AM - last edited on 12-08-2021 09:07 AM by jdelio
- Open the Signature Tab.
- Select add at the bottom left.
- Since we only have one condition it doesn't matter if we choose the 'and'/'or' condition.
- To determine a unique string the *NIX utility xxd was used in this case, however any hex editor will work for this purpose.
- 11626 Views
- 4 replies
- 3 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- DNS req/res does not work with "transaction" scope in Custom Signatures
- Newsletter: Cloud Delivered Security Services, Oct-2025 in Advanced Threat Prevention Discussions
- How to specify multiple conditions for the "test custom-signature-perf" command in Custom Signatures
- Can Copilot help with writting of custom application or vunrability signatures on NGFW or Prisma Access? in Strata Copilot Discussions
- Article about custom Palo Alto signatures in Custom Signatures