- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Enable Access to Office 365 with MineMeld [Updated]
- LIVEcommunity
- Articles
- General Articles
- Enable Access to Office 365 with MineMeld [Updated]
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
on 08-01-2018 07:44 AM - edited on 11-04-2024 05:43 PM by JayGolf
Note: Palo Alto Networks made an end-of-life announcement about the MineMeld™ application in AutoFocus™ on August 1, 2021. Please read this article to learn about our recommended migration options.
Overview
As customers migrate to Office 365, they find themselves whitelisting a range of App-IDs for the various workloads they might use the Office 365 product sets, such as Skype for Business, OneNote, Exchange Online and so on. Because Microsoft publishes Office 365 over a huge range of URLs, and IP addresses, a security admin would be tempted to simply allow access in policies to a destination of any, and this gets complicated when the Office 365 App-IDs tend to have dependencies on explicitly allowing web-browsing and SSL. It would be preferable to configure external dynamic lists and reference that in our security policies, and as it happens, Microsoft dynamically publishes a fully up-to-date list of all IPs, URLs and ports used by each of the 17 components of Office 365 every hour that we can use! This article will take you through setting up the open source MineMeld utility to parse this data into EDLs for PAN-OS to consume, and creation of a couple of example security policies for your environment
Step 1. Deploy MineMeld
First, visit the MineMeld Resource Page and select the article (from the top right) about installing and running MineMeld appropriate to your environment. NOTE: if using the VMWare desktop instructions (read Running MineMeld On VMWare Desktop), you can go ahead with the "Super fast setup," but please download the cloud-init ISO and mount it on first boot. Assuming an IP comes via DHCP and you have internet access, your VM will automatically be updated to the latest version of MineMeld.
Make note of MineMeld's IP address (from an ifconfig) as you’ll need it for the web interface in the next step.
Step 2. Obtain & Import Configuration
MineMeld does already come with Prototypes for each of the O365 services but you would normally need to create a miner for each of these from those Prototypes, along with 3 processors and 3 outputs (one each for IPv4 addresses, IPv6 addresses and URLs respectfully). To save you the hassle we've created a set of configurations you can import. Unzip the attached file MMO365-API_ConfigFiles.zip to get the following collection of configurations.
- o365-api-any-any.txt
- o365-api-skype-usgovdod.txt
- o365-api-sharepoint-usgovdod.txt
- o365-api-exchange-usgovdod.txt
- o365-api-skype-usgovgcchigh.txt
- o365-api-sharepoint-usgovgcchigh.txt
- o365-api-exchange-usgovgcchigh.txt
- o365-api-skype-china.txt
- o365-api-sharepoint-china.txt
- o365-api-exchange-china.txt
- o365-api-skype-germany.txt
- o365-api-sharepoint-germany.txt
- o365-api-exchange-germany.txt
- o365-api-skype-ww.txt
- o365-api-sharepoint-ww.txt
- o365-api-exchange-ww.txt
- o365-api-any-usgovdod.txt
- o365-api-any-usgovgcchigh.txt
- o365-api-any-china.txt
- o365-api-any-germany.txt
- o365-api-any-ww.txt
In this document we'll use the configuration named "o365-api-any-any.txt" that will set a graph to mine all ServiceAreas in all O365 Instances. But you might choose to use the any configuration that better suits your needs.
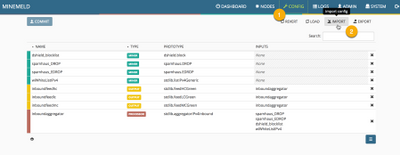
Browse to https://Your-MM-IP-address/ (obtained above) and sign in with the username admin and password minemeld. Next click CONFIG at the top followed by IMPORT.
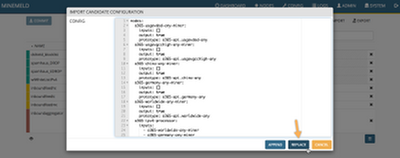
Take into account that this procedure will replace any configuration you might have with this new collection of nodes. Your old configuration will be lost.
Accept to replace the candidate configuration, followed by clicking the COMMIT button and waiting some time for the engine to restart.
Step 3. Review Connection Graph and retrieve Feed Base URLs
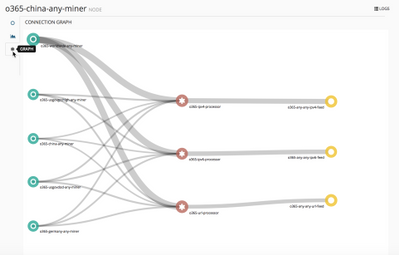
After giving the MineMeld engine a few minutes to restart, click “Nodes” in the banner at the top of the interface and then, click any of the nodes in the list.
Then click the Graph tab (asterisk sign) to bring up the Connection Graph which should look like this:
Here you see each of the miner nodes on the left scraping Microsoft’s dynamically updated endpoints (as described in Managing Office 365 endpoints), the processor nodes that receive URLs, IPv4 and IPv6 addresses, and finally the 3 output nodes that publish a URL that your firewall can poll for an External Dynamic List (EDL).
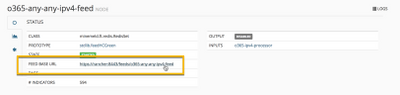
Click each of the output notes and make a note of the Feed Base URL.
Step 4. Consume MineMeld’s output
Follow the instructions in the article Connecting PAN-OS to MineMeld using External Dynamic Lists to connect your PAN-OS Device with the lists provided by MineMeld
Step 5. Create a URL Filtering Profile
This will allow you to limit your access onto to the URLs in the O365-URLs dynamic list, which you’ll apply to your security polic(ies) allowing O365 later. Add a URL filtering profile, and block all categories (hint: Click the top checkbox to select all items, then click the Action banner in the list, and then click “Set Selected Actions,” then block to block all categories at once). Scroll to the bottom and allow only the external dynamic list of O365 URLs.
Step 6: Create Security Policies
Now that we have EDLs and a URL profile in place it’s time to modify/create our security policies. In the example below, we are allowing our Office 365 apps for all known users in the trust zone. The destination zone has been set to untrust zone but with the IPv4/6 lists as destination addresses.
The following is the set of screenshots that ilustrate how the security policy should be created.
FAQ
What applications should I list in the policy?
App-IDs that you may find detected during use of Office 365 (depending on the clients and product sets being used)
- activesync
- mapi-over-http
- ms-exchange
- ms-office365
- ms-onedrive
- rpc-over-http
- soap
- ssl
- stun
- web-browsing
- webdav
- ms-office365
- office-live
- office-on-demand
- outlook-web-online
- ms-lync-online
- ms-lync-online-apps-sharing
- sharepoint-online
- ms-lync-online-file-transfer
What if there's still some O365 activity that is NOT hitting my new security policy?
You may find (from using a catch-all rule with logging) that some sessions are not hitting this O365 rule when they should be. The reason is because Microsoft use CDN networks, which are outside of the IPv4/v6 ranges Microsoft use, like CloudFront for some applications in O365. To allow access to the CDNs that do not match the security policy above, simply create a second security policy that allows from trust to untrust, from the same set of applications in the previous rule, and a destination address of any. In the Service/URL category tab, insert the custom URL category from Step 5. The FQDNs will be present in that URL category and thus match this second rule
How do I filter 3rd party URLs from the endpoint list?
There are 2 ways of doing this.
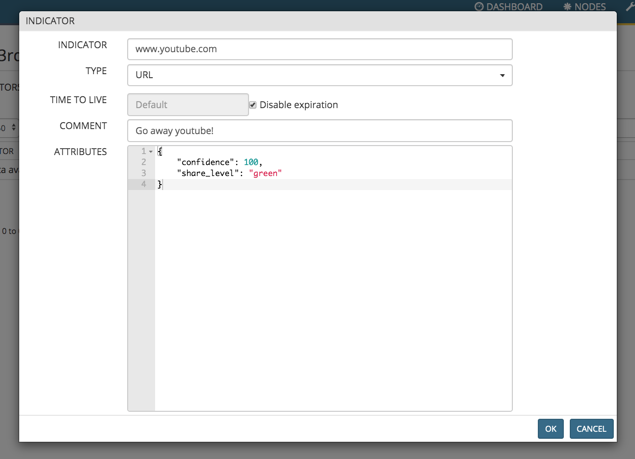
Use a local Miner. This works on any Miner version:
- create a new Miner based on stdlib.localDB to be used a whitelist. The name of the Miner should start with "wl", example: wlSneaky3rdPartyURLs
- connect the Miner to the URL aggregator for the O365 URL and commit
- on the Web UI, under Nodes click on the new Miner and click on the table icon on the left
- add the undesired URL in the indicator list (www.youtube.com in our case) and disable expiration. Click OK
- The undesired is now removed from the URL list
Select only required endpoints. This requires MineMeld version 0.9.62+. An easy way to automatically remove all the 3rd party URLs is selecting only the O365 URLs marked as required by MSFT. MineMeld translates this attribute in the internal o365_required_list attribute (a list) and we can create a filter based on that:
- go to the prototypes, search feedHCWithValue and click NEW (not CLONE)
- give to the new prototype a meaningful name
- paste this config:
infilters:
- actions:
- accept
conditions:
- __method == 'withdraw'
name: accept withdraws
- actions:
- accept
conditions:
- contains(o365_required_list, 'true') == true
name: accept o365 required indicators
- actions:
- drop
name: drop all
store_value: true
- use the new prototype to build a new output node and connect it to the URL aggregator
- only required URLs will be placed in the new output node
-
Hi, thanks for this post.
I think a quick update needs to be done on Step 5
If i am setting "block" in the URL filtering for every other categories than EDL, I got access denied for a lot of things. F
or example, teams's URL teams.microsoft.com is matching the category "computer-and-internet-info", same for skype with "pip.skype.com" which is in category "internet-communication-and-telephony" etc.
Hi @BriceCRUNCHANT what you are experiencing is due the fact PANOS, in case of a given URL matching multiple categories, choses the one with the most severe action - https://live.paloaltonetworks.com/t5/Management-Articles/URL-Filtering-Order/ta-p/59334
It is safe to enable other categories like "computer-and-internet-info" and "internet-communication-and-telephony" (Step 5) because URL's in these categories will only be allowed if the content is provided from the O365's IPv4/IPv6 address space.
Hi @benslade, the O365 endpoints (AKA the new REST API for MS O365 endpoints) is documented in https://support.office.com/en-gb/article/managing-office-365-endpoints-99cab9d4-ef59-4207-9f2b-3728e...
If you follow the document you'll find the URL to check for available O365 instances. At the moment of writing this comment, the list does not contain a specific instance for UK Public. That means that "o365-api-any-any.txt" will definitely cover your case but that you can also try "o365-api-any-ww.txt" if you need to harden your policy.
[
{
"instance": "Worldwide",
"latest": "2018080200"
},
{
"instance": "USGovDoD",
"latest": "2018073100"
},
{
"instance": "USGovGCCHigh",
"latest": "2018063000"
},
{
"instance": "China",
"latest": "2018073000"
},
{
"instance": "Germany",
"latest": "2018063000"
}
]
Ciao to all, this is Marco. I'm asking an help about a paloalto 850 and minemeld.
I have 2 different internet connections attached to the firewall.
One is dedicate to servers traffic and office365. (and this is the default for the firewall)
One is dedicate to web browsing. (this is configured using a PBF).
After implementing minemeld, 365 traffic go away to te default connection (and is right).
The problem is on SKYPE4BUSINESS. Only chat is working. Audio and video calls, desktop sharing and sending request of contacts (to both skype and skype4business) are not working.
Please have you some suggestions?
Thanks indeed.
Ciao ciao,
Marco
Hi @ConfindustriaBG,
have you been able to discover the reason that is blocking your users from using audio and video in Skype call? I guess it is because you're not enabling all needed applications (stun ...) but there may be many other explanations.
Hi,
If you've got problems importing these configuration files, make sure you're running MineMeld 0.9.50 as it'll not work with 0.9.36 for example.
If you need to upgrade, run "sudo /usr/sbin/minemeld-auto-update" and it should be ok.
Just a note on the suggesting of importing of the Office 365 config and overwriting your existing config which is a bit bizarre!!!
When this article says "Take into account that this procedure will replace any configuration you might have with this new collection of nodes. Your old configuration will be lost." it literally means ANY config... no matter if its an existing security feed config etc, it will be ovewritten!!!
HOWEVER, fear not...
1. You should have taken a backup of the system before-hand right? E.g:
* A VM snapshot if running on a VM.
* An export of the existing config to a text file.
2. Even if you do choose to OVERWRITE your config, you can roll it back by immediately pressing REVERT button in the Config section.
3. Despite what the article says, you do not need to OVERWRITE, but you can APPEND the config instead if you wish, therefore keeping your existing configs and complimenting them with the Office 365 config. - Just make sure you miners, processors and outputs aren't clashing.
Remember - you can REVERT.
Once you're happy, then you can COMMIT.
RLJFRY - You sir, should get a promotion for the above comment. Thank you
How are people proceeding with existing versions of minemeld that are not running .50 release? Is it suggested to stick with your initial deployments, or have you gone to updating your minemeld instance and utilized the directions cited here?
We are seeing one of our sync servers trying to hit amazon ip's, and it's not matching policy. It's hitting the CDN part that is mentioned below. How are people handling this knowing that your URL list is allowing sites like dropbox/itunes/ and other 3rd party items? Are people literrally only placing the URL profile and a desination of any for this?
What if there's still some O365 activity that is NOT hitting my new security policy?
You may find (from using a catch-all rule with logging) that some sessions are not hitting this O365 rule when they should be. The reason is because Microsoft use CDN networks, which are outside of the IPv4/v6 ranges Microsoft use, like CloudFront for some applications in O365. To allow access to the CDNs that do not match the security policy above, simply create a second security policy that allows from trust to untrust, from the same set of applications in the previous rule, and a destination address of any. In the Service/URL category tab, insert the custom URL category from Step 5. The FQDNs will be present in that URL category and thus match this second rule
Hi guys, looks like there is an issue with the URL processor. Please could you check this out as it breaks OneNote.
The original input from Microsoft includes for instance two URLs "cdn.onenote.net" and "site-cdn.onenote.net" under "id": 271, and these two are aggregated to "*cdn.onenote.net" which is invalid as the wildcard and charaters cannot be in the same token.
In total there are 11 entires like this and the FireWall log shows that it skipped exactly 11
"Office365-URL, 1, 1 url) Valid entries(578) lines skipped(11)"
*broadcast.officeapps.live.com *cdn.onenote.net *excel.officeapps.live.com *onenote.officeapps.live.com *powerpoint.officeapps.live.com *view.officeapps.live.com *visio.officeapps.live.com *word-edit.officeapps.live.com *word-view.officeapps.live.com
*-files.sharepoint.com *-myfiles.sharepoint.com
I know this is an old post, replying to benefit other users.
We ran into the same issue, talked to Support and this is expected behavior.
If you add "?v=panosurl" to the end of the Minemeld URL then you will get a list better formated to use on the firewall.
For example it will convert "*cdn.onenote.net" to two entries; "onenote.net" and "*.onenote.net".
I just needed the list, Thank you. I just followed the directions I found online and got it up and running at this point.
I do have another question. Can I have multiple configs? When I imported the config from the .zip, it says I overwrote what was in there. Does that mean you can only have one config. Meaning only the o365 config. I was hoping to incorporate many others, i.e. Apple services/ip addresses. That is my second question. Is there a safe enable for Apple?
Hi,
The worldwide url and any-any list contains sites like youtube.com. How can i remove them?
I've read you have to disable "INTEGRATIONS" in the miner, but this didn't work. It did remove some entries, but youtube is still present
Microsoft states all url's need to be excluded from ssl decryption so using this list wil leave those 3rd parties also encrypted.
Last time I looked the "disable integrations" code looked for the string "integration" in the "notes" attribute. To filter out youtube and others the regex /integration|(3|thi)rd[- ]part(y|ies)/i has to be applied to this attribute.
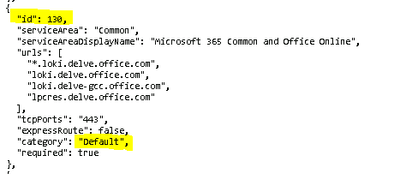
Microsoft states that categories "Required" and "Allow" are incompatible with SSL decryption. All the integration stuff has:
"category": "Default",
"required": false,
So you could decrypt them. Altenatively you can specify URLs AND IP addresses in the "No Decryption" rule because MS does not list/know the IP addresses of those 3rd party services. Of course this would also affect MS services hosted on Akamai and other non-MS CDNs.
And how would one configure this regex ? Maybe you can attach an example config?
thanks in advance
This would be in the python code of the miner.
It would be great if we could implement this ourselves in nodes input or output conditions, but I don't know if this is possible. Can someone point to more detailed documentation, please?
Found this solution to remove youtube:
But the palo alto implementation is flawed.
The best way to filter out youtube and other 3rd parties, and select only "required" endpoints is building an output node with the right filters applied to the endpoints. I will add this to the article, something similar to:
infilters:
- actions:
- accept
conditions:
- __method == 'withdraw'
name: accept withdraws
- actions:
- accept
conditions:
- contains(o365_required_list, 'true') == true
name: accept o365 required indicators
- actions:
- drop
name: drop all
store_value: trueHello,
I face the same issue than this topic: https://live.paloaltonetworks.com/t5/MineMeld-Discussions/AutoFocus-MineMeld-with-Office-365/td-p/26...
A customer asks for decrypting OneDrive (Sharepoint) traffic (despite if it is not recommended by MS). Thus I've created new nodes depending on the 'o365-api.worldwide-sharepoint' prototype but I see in my outputs the URLs/IPv4/IPv6 belonging to the "Sharepoint" serviceArea + from the "Common" serviceArea.
Do you know a way to exclude the "Common" area from the miner?
Thanks
Hello, I have my minemeld running now and wanted to add o365. I followed the description here and it looks basically OK, but my o365 miner all have a red exclamation mark. The error says endpoints.office.com read timeout. In my firewall log I don´t see any blocked access to this site and the spamhaus default miner is also working.
What am I doing wrong?
---edit---
I think you can forget my post - I just found the URLs on a Microsoft website and they actually time out at the moment...
---edit---
Brgds Andreas
I echo comments by Deas.h
I have minemeld installed and have imported the o365-api-any-any.txt Office365 script but now have 5 miners that have a red exclamation mark against them.
States read timed out going to endpoints.microsoft.com, however I can manually browse to endpoints.microsoft.com
The firewall is not blocking anything but I can not get the miners to work
What am I doing wrong?
Cheers
Wozza
@Warren_Norman we are experiencing the same odd issue, it doesn't seem to be related to MineMeld as most of the MineMeld instances works as expected.
Could you try running this from MineMeld shell:
curl "https://endpoints.office.com/version?clientrequestid=3fb1f126-e221-490f-857e-c4332d38979a"
I also think there is no problem with minemeld. It is related to Microsoft. But who/where can we report this issue?
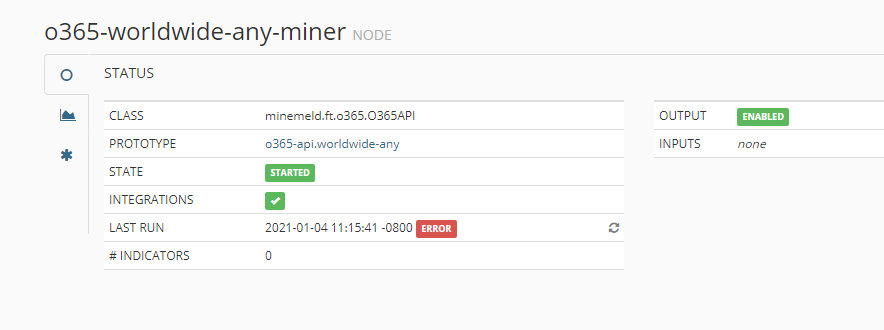
In the meantime the "o365-worldwide-any-miner" miner was able to download once 13 hours ago. And now only read timeout again.
And I found this on GitHub: https://github.com/PaloAltoNetworks/minemeld/issues/49 So this is a Microsoft issue. Why now and why for such a long time???
The curl command is doing now nothing for about 10 minutes...
Brgds Andreas
@Deas.h I have been in touch with Microsoft during the weekend, it seems that this is happening only on some specific locations/IPs around the world and it was difficult to reproduce.
@Deas.h, @Warren_Norman Could you send me an email to lmori at paloaltonetworks.com if you don't mind sharing your details with Microsoft?
Thanks!
Luigi
@lmori I run that and got 'TCP connection reset by peer', strange thing is I pasted that url into my browser and was able to download the json file?
@ccarter I had a hard time as well, its right before the comments section! I even searched for it and could not find it.
Minemeld should also use categorize parameters from new Endpoints and better usage with split tunneling configurations.
https://github.com/PaloAltoNetworks/minemeld-node-prototypes/issues/120
@daniel.sneto MineMeld is already exposing the parameters for each Endpoint and those can be used to create split tunnelling configs.
Hi @lmori thanks for you help.
Can you explain better how can we use this categories also on Minemeld?
Just a FYI about these o365 Feeds - they include URL's from other vendors, like Google, Evernote, Dropbox and some others. We exempt the o365 from TLS decryption, and I found that our enforcement of Non-Company domains for G-suite were being allowed (i.e. personal Gmail) Previously, personal G-mail had been denied using HTTP Header insertion on the PA, but looking into things further, these MS o365 URL list is brining in the following URL's from Google, which was causing no-decrypt on these, bypassing our policy for non company domain Gmail. I had to add these to the dynamic URL exception list to get things working again. In our case, it was the following URL's being brought in:
accounts.google.com
mail.google.com
play.google.com
www.google-analytics.com www.googleapis.com
Not sure what MS is trying to do here. They must be trying to do some integration with Google from O365?
Hi,
I successfully imported the txt file to minemeld but I am getting this error
"__init__() got an unexpected keyword argument 'server_hostname'"
the feeds and indicators are not able to pull any IP addresses.
Please let me know what I can do to resolve the issue
can someone please provide step by step configuration of Mine mild into Palo alto Firewall for dynamic updates of office 365.
Thanks
- 220309 Views
- 44 comments
- 11 Likes
-
"Address Objects"
1 -
10.0
2 -
10.1
2 -
10.2
3 -
8.1
1 -
9.0
1 -
9.1
1 -
ACC
1 -
Active-Passive
1 -
AD
1 -
address objects
1 -
admin roles
1 -
Administration
6 -
Administrator Profile
1 -
Advanced URL Filtering
2 -
Advanced WildFire
1 -
Alibaba
2 -
Alibaba Cloud
3 -
Ansible
1 -
antivirus
1 -
API
2 -
applications
2 -
APS
1 -
Asset Management
1 -
Authentication
6 -
Authentication Profile
1 -
Authentication Sequence
1 -
automatically acquire commit lock
1 -
Automation
3 -
AWS
6 -
Azure
1 -
Basic Configuration
4 -
Beacon
2 -
Beacon2020
1 -
Best Practices
2 -
Block List
1 -
categories
1 -
certificates
1 -
Certification
1 -
Certifications
1 -
Certifications & Exams
1 -
CLI
4 -
CLI command
3 -
Cloud Automation
1 -
Cloud Identity Engine
1 -
Cloud NGFW
1 -
Cloud Security
1 -
Collector Group
1 -
Commit Process
1 -
community news
1 -
Configuration
9 -
Configure Next Generation Firewall
1 -
console
1 -
Cortex
1 -
Cortex Data Lake
2 -
Cortex XDR
5 -
COVID-19
1 -
CPSP
1 -
cyber elite
1 -
Cyberelite
11 -
dag
2 -
Debug
1 -
debugging
2 -
Default Policy
1 -
Deployment
1 -
discussions
1 -
EDL
3 -
education
2 -
Education and Training
2 -
Education Services
2 -
Educational Services
1 -
Effective Routing
1 -
Endpoint
1 -
ESXi
1 -
Events
1 -
expedition
1 -
export
1 -
failover
1 -
FAQ
1 -
Filtering
2 -
Firewall
2 -
Firewall VM-Series
2 -
Focused Services
2 -
Focused Services Proactive Insights
1 -
gateway
1 -
Gateway Load Balancer
3 -
Gateway Loadbalancer
2 -
GCP
5 -
GCP Firewall
1 -
geolocation
1 -
Getting Started
1 -
GitHub
1 -
Global Protect
1 -
Global Protect Cookies
1 -
GlobalProtect
8 -
GlobalProtect App
1 -
globalprotect gateway
1 -
GlobalProtect Portal
2 -
google
2 -
Google Cloud
3 -
google cloud platform
4 -
GWLB
3 -
Hardware
2 -
hash
1 -
Header Insertion
1 -
High Availability
1 -
How to
1 -
HTTP
1 -
https
1 -
Hybrid Cloud
1 -
ike
3 -
import
1 -
Installation & Upgrade
1 -
IoT
2 -
IoT Security
1 -
IPSec
4 -
IPSec VPN Administration
1 -
kerberos
1 -
Kubernetes
1 -
Layer 2
2 -
Layer 3
1 -
Learning
1 -
licenses
1 -
local user
3 -
Log Cluster Design
1 -
Log Collection
1 -
Log Collector Design
1 -
Log Forwarding
1 -
Log4Shell
1 -
Logging
2 -
login
1 -
Logs
3 -
Malware
1 -
Management
8 -
Management & Administration
5 -
MFA
1 -
microsoft
2 -
Microsoft 365
1 -
minemeld
24 -
multi factor authentication
1 -
multi-factor authentication
1 -
multi-vsys
1 -
NetSec
1 -
NetSec Newsletter
1 -
Network Security
37 -
network-security
1 -
Networking
1 -
New Apps
1 -
News
1 -
newsletter
2 -
Next Generation Firewall
3 -
Next-Generation Firewall
42 -
next-generation firewall. network security
1 -
Next-Generation Firewall. NGFW
4 -
ngfw
26 -
NGFW Configuration
10 -
NGFW Newsletter
1 -
Objects
2 -
Oracle Cloud
1 -
Oracle Cloud Infrastructure
1 -
OTP
1 -
PA-3200 Series
1 -
PA-400
1 -
pa-440
2 -
PA-5400 series
1 -
PA-800 Series
1 -
pa-820 firewall
1 -
Packet Buffer
1 -
packet debug
1 -
packet diag
1 -
PAN-OS
17 -
PAN-OS 10.2
1 -
PAN-OS 11.0
1 -
PAN-OS 9.1
1 -
Panorama
8 -
Panorama 8.1
1 -
Panorama 9.1
1 -
Panorama Configuration
2 -
Panorama HA
1 -
PBF
1 -
PCNSA
2 -
PCNSE
2 -
policies
2 -
policy
3 -
Policy Based Forwarding
1 -
Prisma
1 -
prisma access
5 -
Prisma SD-WAN
1 -
proactive insights
2 -
QRadar
1 -
Radius
1 -
Ransomware
1 -
region
1 -
Registration
1 -
Release Notes
1 -
reporting and logging
1 -
Risk Management
1 -
Routing
1 -
SAML
1 -
SASE
2 -
script
2 -
SD WAN
1 -
SD-WAN
1 -
SDWAN
1 -
Search
1 -
Security Advisory
1 -
Security automation
1 -
security policy
4 -
security profile
1 -
Security Profiles
2 -
Session Packet
1 -
Setup & Administration
7 -
Site-to-Site VPN
1 -
Split Tunneling
1 -
SSL
1 -
SSL Decryption
2 -
SSL Forward Proxy
1 -
SSO
1 -
Strata Logging Service
2 -
Support Guidance
1 -
syslog
1 -
Tag
2 -
Tags
2 -
Terraform
2 -
TGW
3 -
threat log
1 -
Threat Prevention
2 -
Threat Prevention License
1 -
Threat Prevention Services
1 -
Tips & Tricks
2 -
tls
1 -
traffic_log
1 -
Transit Gateway
1 -
Traps
1 -
Troubleshoot
2 -
Troubleshoot. logs
1 -
troubleshooting
5 -
tunnel
2 -
Tutorial
2 -
Ubuntu 16.04
1 -
Unified Monitoring
1 -
Upgrade
2 -
upgrade-downgrade
3 -
url categories
1 -
URL Filtering
2 -
URL-Filtering
1 -
User ID Probing
1 -
User-ID
1 -
User-ID & Authentication
1 -
User-ID mapping
1 -
userid
1 -
VM Series
1 -
VM-Series
15 -
VM-Series on AWS
6 -
VM-Series on GCP
2 -
VPC Flow logs
1 -
VPN
2 -
VPNs
4 -
Vulnerability Protection
1 -
Webinar
1 -
WildFire
3 -
Wildfire License
1 -
wmi
1 -
XDR
1 -
xml
2 -
XML API
2
- Previous
- Next