- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Nominated Discussion: URL Filtering Profile Set to Allow Ransomware
- LIVEcommunity
- Articles
- General Articles
- Nominated Discussion: URL Filtering Profile Set to Allow Ransomware
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
on 10-05-2022 11:38 AM - edited on 10-05-2022 12:37 PM by jennaqualls
This article is based on a discussion,URL set to allow Ransomware, posted by @Schneur_Feldman and answered by @Astardzhiev, @BPry and @Adrian_Jensen. Read on to see the discussion and solution!
Can anyone please explain why Palo Alto Networks would release a Ransomware URL Category and put the default to allow?
It's going to be a pain logging into every single client of ours that uses Palo and changing Ransomware URL Category to block. Is there a way to automate it? What would the CLI command be?
Palo Alto Networks doesn't have visibility into how, why and where you are using your URL filtering profiles. They give you the tools, it is your decision how to use them.
The CLI command would be:
- Locally managed firewall
set profiles url-filtering <profile-name> block ransomware
- Panorama managed firewall
set device-group <device-group-name> profiles url-filtering <profile-name> block ransomware
There are couple of ways to automate such change and depending on your environment:
- Export firewall running config; search and edit the XML defining any URL filtering profile; import, load and commit the edited config
- Similar as above but for Panorama config, modifying any URL filtering in all available device-groups
From your comment it seems you support multiple different clients, which probably require different ways to connect and different credentials. So you are probably better using the XML API. You may want to check python framework, which could save you some time (connecting and authenticating to the device).
To further expand on this, Palo Alto Networks can't identify what you're using a profile for. If I have devices segmented off into a malware research zone and utilize a subset of my machines for those purposes, I absolutely wouldn't want Palo Alto Networks to modify my profiles to block a newly introduced category for a subset of machines where I would actually want to allow the traffic.
If you're managing multiple clients I'd really recommend looking at the benefits of utilizing Panorama to manage all of them, or better yet managing them directly through the XML configuration file and templating some of the configuration yourself if you can't get approved to purchase Panorama. The API here can also be a major help, but if you're not comfortable with it it's not going to be a quick fix since you'll need to be parsing results and using that information in additional changes.
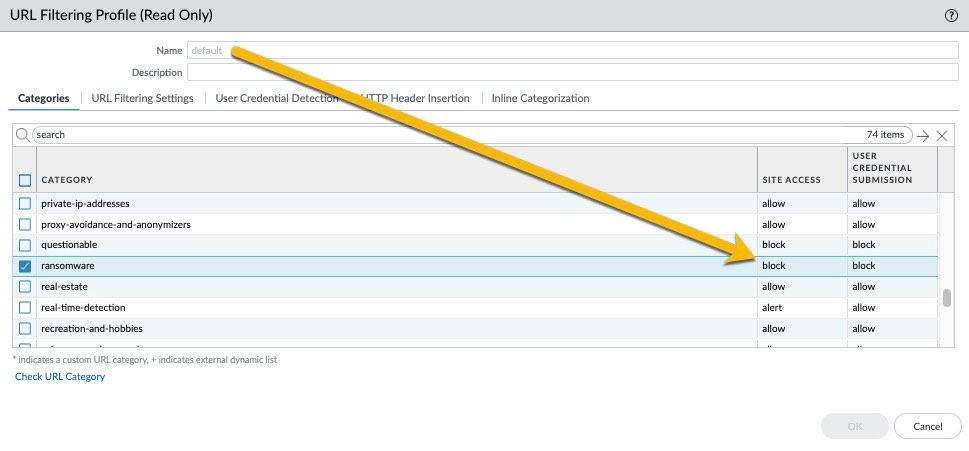
NOTE: The new "ransomware" category is blocked in the "default" URL Filtering category. But as you pointed out correctly it is not blocked by default in custom URL Filtering categories because Palo Alto Networks doesn't know what you are using custom categories for.
If I may add my 2 cent here.
While I can agree on the fact that Palo Alto is not aware of what a URL filtering profile is used for.
A new category like ransomware should at least be implemented as "alert" for all URL filtering profiles that are detected
Palo Alto is all about security. therefore to me as a customer. I would expect such a URL category to be blocked by default, or that I would have to manually enable that new URL category.
Now in regards to Encrypted-DNS i see how that might be a more tricky case and I could understand to have it as "Alert" only.
But what I would never want from a newly created URL category, to be implemented in my URL Profiles set to "ALLOW" that is by far the worst of them all.
Regards
Alex
Hi @AlexNC ,
Thank you for your feedback. I understand your concern.
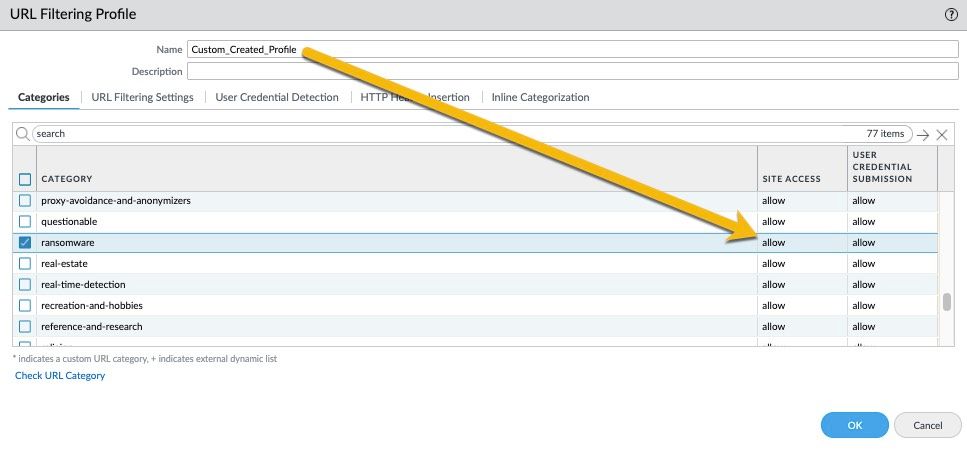
I do want to emphasize that the new "ransomware" category is blocked in the default URL Filtering profile. Current design sets it to a default allow on custom created URL filtering profiles only (same for all other categories).
One can easily adjust the action on all categories at once and set it to alert for example.
That being said, new categories will also get a default allow action. Customers are informed well in advance and usually a placeholder is created weeks in advance to allow customers to make the necessary adjustments in time.
- 4543 Views
- 2 comments
- 3 Likes
- Nominated Discussion - Sorting Question in General Articles
- Nominated Discussion: Action=Allow While NATDestinationIP=0.0.0.0 in General Articles
- Nominated Discussion: How to View Correlated Logs on the Firewall in General Articles
- Nominated Discussion: Why You Need Security Profiles in General Articles
- Nominated Discussion: URL Filtering in TLS v1.3 in General Articles
-
"Address Objects"
1 -
10.0
1 -
10.1
1 -
10.2
2 -
ACC
1 -
Active-Passive
1 -
AD
1 -
address objects
1 -
admin roles
1 -
Administration
6 -
Administrator Profile
1 -
Advanced URL Filtering
2 -
Advanced WildFire
1 -
AI
1 -
AI Security
1 -
AIOPS
1 -
Ansible
1 -
antivirus
1 -
API
1 -
App-ID
1 -
applications
2 -
APS
1 -
Asset Management
1 -
Authentication
6 -
Authentication Profile
1 -
Authentication Sequence
1 -
automatically acquire commit lock
1 -
Automation
3 -
AWS
3 -
Basic Configuration
4 -
Beacon
1 -
best practices
6 -
Block List
1 -
categories
1 -
certificates
1 -
Certification
1 -
Certifications
1 -
Certifications & Exams
1 -
CLI
5 -
CLI command
3 -
Cloud Automation
1 -
Cloud Identity Engine
1 -
Cloud NGFW
1 -
Cloud Security
1 -
Collector Group
1 -
Commit and Push
1 -
Commit Process
1 -
Configuration
8 -
Configuration and Management
3 -
Configure Next Generation Firewall
1 -
console
1 -
Cortex
1 -
Cortex Data Lake
2 -
Cortex XDR
3 -
CPSP
1 -
Custom Signatures
3 -
cyber elite
1 -
cyberelite
11 -
dag
1 -
DDoS
1 -
Debug
1 -
debugging
2 -
Default Policy
1 -
discussions
1 -
EDL
2 -
education
1 -
Education and Training
1 -
Education Services
1 -
Educational Services
1 -
Effective Routing
1 -
Endpoint
1 -
export
1 -
failover
1 -
FAQ
1 -
file upload
1 -
Filtering
2 -
Firewall
2 -
Firewall VM-Series
2 -
Focused Services
3 -
Focused Services Proactive Insights
2 -
gateway
1 -
Gateway Load Balancer
2 -
GCP
2 -
GCP Firewall
1 -
geolocation
1 -
Getting Started
1 -
GitHub
1 -
Global Protect
1 -
Global Protect Cookies
1 -
GlobalProtect
7 -
GlobalProtect App
1 -
globalprotect gateway
1 -
GlobalProtect Portal
2 -
google
2 -
Google Cloud
3 -
google cloud platform
2 -
Hardware
2 -
Header Insertion
1 -
High Availability
1 -
How to
1 -
HTTP
1 -
https
1 -
Hybrid Cloud
1 -
ike
3 -
import
1 -
Installation & Upgrade
1 -
IoT
1 -
IPSec
4 -
IPSec VPN Administration
1 -
kerberos
1 -
Layer 2
1 -
Layer 3
1 -
Learning
1 -
licenses
1 -
local user
3 -
Log Cluster Design
1 -
Log Collection
3 -
Log Collector Design
2 -
Logging
1 -
login
1 -
Logs
3 -
Management
8 -
Management & Administration
5 -
MFA
1 -
Microsoft
1 -
Microsoft 365
1 -
Migration
1 -
minemeld
4 -
multi factor authentication
1 -
multi-factor authentication
1 -
multi-vsys
1 -
NAT
1 -
NetSec
1 -
NetSec Newsletter
1 -
Network Security
34 -
Network Security Management
1 -
network-security
1 -
Networking
1 -
newsletter
2 -
Next Generation Firewall
4 -
Next-Generation Firewall
42 -
next-generation firewall. network security
1 -
Next-Generation Firewall. NGFW
6 -
NGFW
30 -
NGFW Configuration
11 -
NGFW Newsletter
1 -
Nominated Discussion
1 -
Objects
2 -
OTP
1 -
PA-3200 Series
1 -
PA-400
1 -
pa-440
2 -
PA-5400 series
1 -
PA-800 Series
1 -
pa-820 firewall
1 -
Packet Buffer
1 -
packet debug
1 -
packet diag
1 -
PAN-OS
16 -
PAN-OS 10.2
1 -
PAN-OS 11.0
1 -
PAN-OS Prisma Access
1 -
Panorama
11 -
Panorama Configuration
2 -
PBF
1 -
PCNSA
1 -
PCNSE
1 -
performance
2 -
policies
2 -
policy
3 -
Policy Based Forwarding
1 -
Prisma Access
5 -
Prisma AIRS
1 -
Prisma SD-WAN
1 -
proactive insights
2 -
Radius
1 -
Ransomware
1 -
region
1 -
Registration
1 -
reporting and logging
1 -
RestAPI
1 -
Risk Management
1 -
Routing
1 -
SAML
1 -
SASE
1 -
script
2 -
SD WAN
1 -
SDWAN
1 -
Search
1 -
Security Advisory
1 -
Security automation
1 -
security policy
4 -
security profile
1 -
Security Profiles
2 -
Selective Push
1 -
Session Packet
1 -
Setup & Administration
8 -
Site-to-Site VPN
1 -
Split Tunneling
2 -
SSL
1 -
SSL Decryption
2 -
SSL Forward Proxy
1 -
SSO
1 -
Strata Cloud Manager
1 -
Strata Logging Service
2 -
Support Guidance
1 -
syslog
1 -
system modes
1 -
Tag
2 -
tags
2 -
Terraform
2 -
Threat
1 -
threat log
1 -
Threat Prevention
1 -
Threat Prevention License
1 -
Tips & Tricks
1 -
TLS
1 -
traffic_log
1 -
Traps
1 -
Troubleshoot
2 -
Troubleshoot. logs
1 -
Troubleshooting
6 -
tunnel
2 -
Tutorial
2 -
Unified Monitoring
1 -
upgrade
1 -
upgrade-downgrade
2 -
url categories
1 -
URL Filtering
2 -
URL-Filtering
1 -
User ID Probing
1 -
User-ID
1 -
User-ID & Authentication
1 -
User-ID mapping
1 -
userid
1 -
VM Series
1 -
VM-Series
7 -
VM-Series on AWS
3 -
VM-Series on GCP
2 -
VPC Flow logs
1 -
VPN
3 -
VPNs
4 -
Vulnerability
2 -
Vulnerability Protection
1 -
WildFire
2 -
Wildfire License
1 -
wmi
1 -
XDR
1 -
xml
2 -
XML API
2
- Previous
- Next




