- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
ALG (Application Layer Gateway) and Oracle
- LIVEcommunity
- Discussions
- General Topics
- ALG (Application Layer Gateway) and Oracle
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
ALG (Application Layer Gateway) and Oracle
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-19-2017 07:47 AM
Hi,
I've an application who has to query an Oracle database to get information from it. There is a PaloAlto firewall between my application and the DB.
I actually reach the database, but I can't collect the information that I need. Making a quick tcpdump of incoming packets on the server in which my application is running, I noticed on wireshark that, on the response packet of the DB, there is this error: Malformed Packet: TNS.
There is no "deny" on the firewall, I was wondering if it can be related to the ALG functionality. Making some research online I found threads like these, in which is clearly said that the solution is to disable the ALG:
http://packetpushers.net/sqlnet-a-k-a-oracle-tns-and-firewalls/
https://forums.juniper.net/t5/SRX-Services-Gateway/Oracle-TNS-packet-drop-issue/td-p/159316
The documentation of PaloAlto states:
Palo Alto Networks firewall provides NAT ALG support for the following protocols: FTP, H.225, H.248, MGCP, MySQL, Oracle/SQLNet/TNS, RPC, RSH, RTSP, SCCP, SIP, and UNIStim.
But it is not clear which is the default behavior of the firewall with these services. It actually performs NAT ALG on all of the services listed, even if you do not specify to use it?
Furthermore, I saw also that you can disable ALG module just on SIP application. And what if ALG is performed even on the services listed above and you want to disable it?
Is there someone who is able to help me on this matter?
Thanks in advance
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-19-2017 08:08 AM
Depending on the application's behavior the ALG accomodates returning packets requiring a pinholed port or 'special' NAT processing, like for example FTP where a new session is set up from the server to the client to provide a data channel
If your implementation requires a different methodology than the protocol standard, the ALG could mess things up
In the first place you could try disabling ALG and secondly you could try an app override to a custom app which will disable all content inspection of the traffic in case non-standard (or a new incarnation/update/version that we have not incorporated yet) implementation is being used
in the case of the latter, please reach out to support so we can update our App-ID database
I'm not quite sure what your question is regarding SIP. Each protocol has it's own decoder and ALG, so disabling one does not interfere with another
PANgurus - Strata & Prisma Access specialist
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-19-2017 08:26 AM - edited 10-19-2017 10:31 AM
@reaper wrote:
In the first place you could try disabling ALG
The problem is, is it possible to disable ALG just for a single policy? As far as I understand reading the guide (I don't have the access to the PA firewall), it's possible to disable ALG just in case of SIP applications (that's why I mentioned SIP in my previous question).
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-19-2017 11:44 AM
Sip is just a common example but all the other apps can be accessed and altered in exactly the same way
PANgurus - Strata & Prisma Access specialist
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-19-2017 03:41 PM
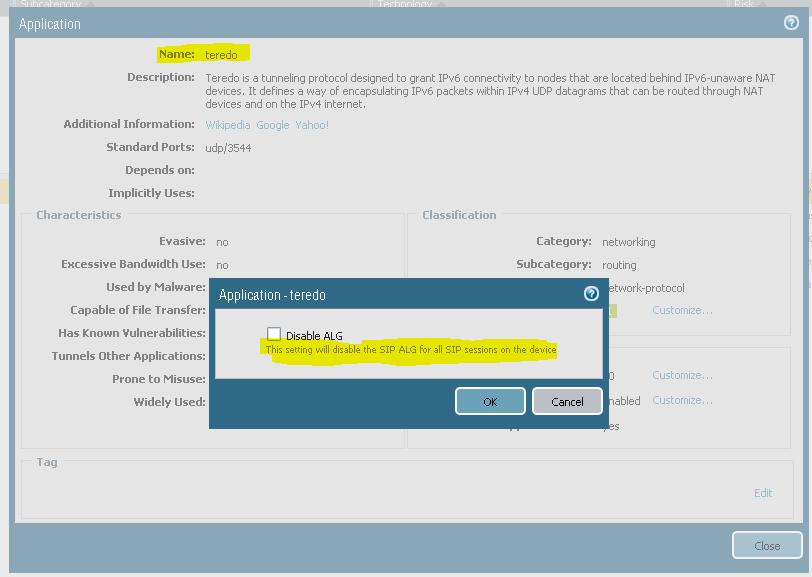
Looks like ALG can be disabled only in specific applications.
In other cases you can use Application Override.
# set shared alg-override application sccp application sccp sip application sip teredo application teredo unistim application unistim <name> <name>
Palo Alto Networks certified from 2011
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-19-2017 03:44 PM - edited 10-19-2017 03:45 PM
I wonder if it is typo in GUI that it mentiones SIP ALG in all cases?
Palo Alto Networks certified from 2011
- 8894 Views
- 5 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Global Protect Client Crash 6.3.3 in GlobalProtect Discussions
- Redirecting from 3rd party auth provider back to GlobalProtect Clientless VPN application in GlobalProtect Discussions
- Customize Authentication Complete URL in General Topics
- GlobalProtect VPN blocks/discards pakets to broadcast in GlobalProtect Discussions
- Technical Inquiry – Does PA-400 Series Support USG/BSG Functionality? in General Topics