- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Authentication error after upgrading to 7.0.x
- LIVEcommunity
- Discussions
- General Topics
- Re: Authentication error after upgrading to 7.0.x
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-30-2016 02:48 PM
Hi,
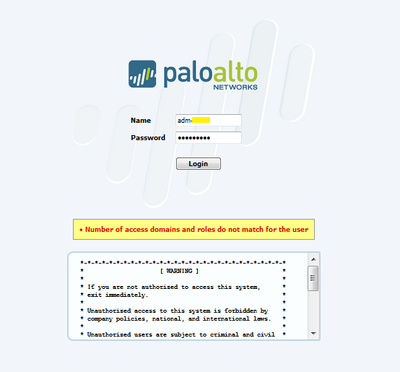
I've one issue after upgrading for one of my client from 6.1.6 to 7.0.7 regarding Radius authentication. Authentication was successful till we upgrade to the new version. After the upgrade we are getting the error “Number of Access Domains and roles doesn't match for the user". Only local admins can log in but not Radius admins.
When I checked the error in community articles I found it related to Panorama as "access domains" only available in Panorama when we are using Radius authentication but they don't have Panorama 🙂
I've read another article when they said after version 7.0 PA is using CHAP then fallback to PAP, then I've changed the used protocol to PAP only using the following:
> set authentication radius-auth-type PAP
But I’m still getting the same error.
Then I checked the authd.log and found the following:
2016-12-27 15:39:03.411 +0400 debug: pan_authd_radius_set_auth_type(pan_authd_radius.c:67): Set PAP (only) request type to ip:port=10.110.255.122:1812
2016-12-27 15:39:39.984 +0400 debug: pan_auth_request_process(pan_auth_state_engine.c:1540): Receive request: msg type PAN_AUTH_REQ_REMOTE_INIT_AUTH, conv id 1, body length 2156
2016-12-27 15:39:39.984 +0400 debug: pan_auth_request_process(pan_auth_state_engine.c:1563): Trying to authenticate: <profile: "", vsys: "", username "adm-admin">
2016-12-27 15:39:39.984 +0400 debug: _get_auth_prof_detail(pan_auth_util.c:925): "adm-admin" is an admin user
2016-12-27 15:39:39.984 +0400 debug: _get_admin_authentication_profile_by_name(pan_auth_util.c:505): Got auth prof "Radius" for admin user "adm-admin"
2016-12-27 15:39:39.984 +0400 debug: _get_authseq_profile(pan_auth_util.c:809): Auth profile/vsys (Radius/shared) is NOT auth sequence
2016-12-27 15:39:39.984 +0400 debug: pan_auth_cache_user_is_allowed(pan_auth_cache_allowlist_n_grp.c:260): This is a single vsys platform, group check for allow list is performed on "vsys1"
2016-12-27 15:39:39.984 +0400 debug: pan_auth_cache_user_is_allowed(pan_auth_cache_allowlist_n_grp.c:271): user "adm-admin" is in allow list of auth prof/vsys "Radius/shared"
2016-12-27 15:39:39.984 +0400 debug: _authenticate_by_localdb_or_remote_server(pan_auth_state_engine.c:1068): Authenticating user "adm-admin" with <profile: "Radius", vsys: "shared">
2016-12-27 15:39:39.984 +0400 debug: pan_auth_service_get_svr_ids(pan_auth_service.c:630): find auth server id vector for Radius-shared
2016-12-27 15:39:39.984 +0400 debug: pan_authd_radius_create_req_payload(pan_authd_radius.c:191): username: adm-admin
2016-12-27 15:39:39.984 +0400 debug: pan_make_radius_request_buf(pan_authd_radius_prot.c:412): RADIUS request type: PAP
2016-12-27 15:39:39.985 +0400 debug: pan_make_radius_request_buf(pan_authd_radius_prot.c:444): framed-ip-address is zero. Skip it.
2016-12-27 15:39:40.169 +0400 debug: pan_authd_radius_parse_resp_payload(pan_authd_radius.c:241): resp_code = RAD_ACCESS_ACCEPT
2016-12-27 15:39:40.169 +0400 debug: pan_authd_radius_parse_resp_payload(pan_authd_radius.c:262): access domain = superuser
2016-12-27 15:39:40.169 +0400 debug: pan_auth_service_recv_response(pan_auth_service_handle.c:1185): Got response for user: "adm-admin"
2016-12-27 15:39:40.169 +0400 debug: pan_auth_response_process(pan_auth_state_engine.c:2337): auth status: auth success
2016-12-27 15:39:40.169 +0400 debug: pan_auth_response_process(pan_auth_state_engine.c:2355): username: adm-admin, username_only: adm-admin
2016-12-27 15:39:40.169 +0400 debug: pan_auth_response_process(pan_auth_state_engine.c:2391): local admin acct for remote user 'adm-admin' exists
2016-12-27 15:39:40.169 +0400 debug: pan_auth_response_process(pan_auth_state_engine.c:2397): Authentication success: <profile: "Radius", vsys: "shared", username "adm-admin">
2016-12-27 15:39:40.169 +0400 debug: pan_auth_send_auth_resp(pan_auth_server.c:321): Succeed to cache role/adomain /superuser for user adm-admin
2016-12-27 15:39:40.169 +0400 authenticated for user 'adm-admin'. auth profile 'Radius', vsys 'shared', server profile 'Cisco-ACS-SERVER', server address '10.110.255.121', From: 10.1.132.161.
2016-12-27 15:39:40.169 +0400 debug: _log_auth_respone(pan_auth_server.c:240): Sent SUCCESS auth response for user 'adm-admin' (exp_in_days=-1 (-1 never; 0 within a day))
2016-12-27 15:39:41.251 +0400 debug: pan_auth_request_process(pan_auth_state_engine.c:1540): Receive request: msg type PAN_AUTH_REQ_GROUP, conv id 41, body length 32
2016-12-27 15:39:41.251 +0400 debug: pan_db_funcs_request_process(pan_auth_state_engine.c:906): init'ing group request (authorization)
2016-12-27 15:39:41.251 +0400 debug: pan_authd_handle_group_req(pan_auth_state_engine.c:745): start to authorize user "adm-admin"
2016-12-27 15:39:41.251 +0400 debug: pan_auth_mgr_get_userinfo(pan_auth_mgr.c:1014): Found userinfo (name/role/ado) cache entry: adm-admin//superuser
2016-12-27 15:39:41.251 +0400 debug: pan_authd_handle_group_req(pan_auth_state_engine.c:856): Sent authorization response for user "adm-admin": role/domain="/superuser"; expiring_in_days=-1; rem_grace_period=-1, rem_login_count=-1
Authentication is successful as the logs said but it’s not completing the authorization for some reason.
Anyone have any idea about this issue?
Regards,
Sharief
Sharief
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-18-2017 01:27 AM
Tried to play with user modifier and domain but its not working also.
Now the case is escalated to TAC Support and they couldn't find a proper root cause and pushing me to use TACACS+.
Regards,
Sharief
Sharief
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-03-2017 02:57 PM
Hello,
I'm sure you have done this by now, but you may want to contact support. I dont recall having issues when I upgraded and had radius auth.
Regards,
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-04-2017 01:45 AM
Hi Otakar,
Yup. Already contacted Support, they are analyzing this at the moment.
Regards,
Sharief
Sharief
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-04-2017 10:55 AM
Looks like the radius server is sending radius attribute #4 (for access domains) instead of number #3 (for predefined roles). According to your logs the role is blank but the access domain (ADO) is "superuser" (predefined role)
access domain = superuser Found userinfo (name/role/ado) cache entry: adm-admin//superuser Sent authorization response for user "adm-admin": role/domain="/superuser"
- PaloAlto-Panorama-Admin-Role: Attribute #3 - This can either be a default admin role name or a custom admin role name on Panorama.
- PaloAlto-Panorama-Admin-Access-Domain: Attribute #4 - This is the name of an Access Domain configured on Panorama as created under Panorama > Access Domains.
If you want to configure admins with access domains you can follow the next guide,
You can place a packet capture to analyze the radius responses at the top of my head they should be on clear text,
https://live.paloaltonetworks.com/t5/Management-Articles/Tcpdump-Packet-Capture-Truncated/ta-p/63047
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-05-2017 12:19 AM
Hi glastra1,
Actually it shouldn't send any attributes with #3 or #4 cause we are not using Panorama.
Also the Radius server was working just fine before upgrading to 7.0.7
Regards,
Sharief
Sharief
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-05-2017 05:34 AM
It could also be sending attribute number 2, anyway make sure is sending the right attribute depending on your needs and run packet captures just to double check.
There are 5 attributes:
- PaloAlto-Admin-Role: Attribute #1 - This can either be a default admin role name or a custom admin role name.
- PaloAlto-Admin-Access-Domain: Attribute #2 - This is used when a Palo Alto Networks device has multiple vsys. This is the name of an Access Domain as created under Device > Access Domains.
- PaloAlto-User-Group: Attribute #5 - This is the name of a group to be used in an Authentication Profile.
regards,
Gerardo.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-05-2017 10:43 AM
In your Authentication Profile, what are the values for 'User Domain' and 'Username Modifier'?
I do remember having an issue going from 6.1 to 7.0 and I'm also using radius with Cisco ACS. I think I might have changed the value in one of these fields.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-09-2017 04:06 AM
Hey RFalconer,
You mean the username and domain in the authentication profile of radius as I understand.
Good idea, let me try to change this.
Regards,
Sharief
Sharief
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-18-2017 01:27 AM
Tried to play with user modifier and domain but its not working also.
Now the case is escalated to TAC Support and they couldn't find a proper root cause and pushing me to use TACACS+.
Regards,
Sharief
Sharief
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-12-2020 03:10 PM
I had same error. Try deleting the radius setting and re-add again. Do the same on RADIUS too.
Not sure which device is creating this issue. But we had same issue on couple devices and it worked both times.
- 1 accepted solution
- 9833 Views
- 9 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- XSIAM V3.4 upgrade - anyone having issues? in Cortex XSIAM Discussions
- Geo blocking after GP login in GlobalProtect Discussions
- New cert GP cert prompt for people testing Yubikeys for windows logon in GlobalProtect Discussions
- PAN-OS HA UGRADE PATH in Next-Generation Firewall Discussions
- Assistance with LDAP Authentication in General Topics