- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Best option for a Vwire with tagged and untagged traffic
- LIVEcommunity
- Discussions
- General Topics
- Re: Best option for a Vwire with tagged and untagged traffic
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Best option for a Vwire with tagged and untagged traffic
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-09-2023 10:24 PM
Best option for a Vwire with tagged and untagged traffic.
Hello Livecommunity guys, how are you ? I hope everything's OK.Thank you very much as always for the collaboration.
Whats is the best option when it comes to setting up a Vwire environment with tagged and untagged traffic, ie.
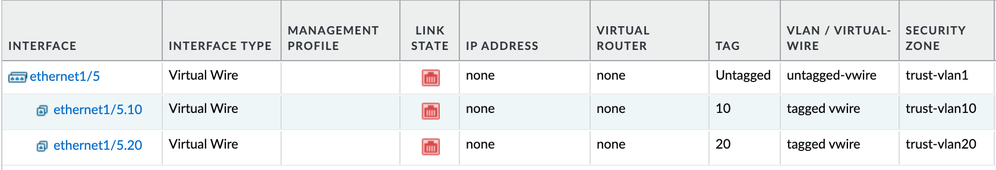
VLANS=====1 Untagged, vlan + 20,30,40=============CoreTrunk=======1 Untagged, vlan tagged:20,30,40 Palo Alto Vwire========1 Untagged, vlan + 20,30,40==========Switch01AB========
What is the best option when using untagged and tagged traffic, thinking about the best visibility and detail of the traffic, that is:
Which is the best option:
1.-Set up subinterfaces with tag 20,30 and 40. and Set up some subinterfaces with TAG 0 (VLAN ID "0" Zero as the documentation indicates that indicates untagged traffic).
2.- Build subinterfaces with tag 20, 30 and 40 and then build a classic, traditional vwire, using and referencing the physical interfaces, by default which already allows untagged traffic (without specifying vlan tags).
3.- Or simply better everything in a Vwire allowing in the Tagged Allow 0-4094 (or allowing "0" for untagged traffic) and then putting the TAGs of 20,30 and 40, that is, this is how the vlans would be tagged of vwire "0",20,30,40. With this scheme, visibility and control are lost.
Which would be the best Vwire options, when you have L2 and L3 interfaces with subinterfaces, just let the untagged traffic pass through the physical interface, not the sub-interfaces, this applies to L2 and L3 interfaces/subinterfaces, but for Vwire you have to use VLAN ID 0, which identifies the tagged traffic. In my opinion, the best option or options would be options 1 and 2, since 3 loses all visibility, the best option would be 1, subinterfaces even with ID 0 for untagged traffic.
What do you think, what do you think is the best option based on your experience, based on your point of view.
Thank you for your comments, for your collaboration, for your time and for the good vibes.
Link/details Supporting Documentation - Virtual Wire - Palo Alto VLAN ID 0 untagged:
"Virtual wire interfaces by default allow all untagged traffic. You can, however, use a virtual wire to connect two interfaces and configure either interface to block or allow traffic based on the virtual LAN (VLAN) tags. VLAN tag 0 indicates untagged traffic.
You can also create multiple subinterfaces, add them into different zones, and then classify traffic according to a VLAN tag or a combination of a VLAN tag with IP classifiers (address, range, or subnet) to apply granular policy control for specific VLAN tags or for VLAN tags from a specific source IP address, range, or subnet."
https://docs.paloaltonetworks.com/pan-os/10-1/pan-os-networking-admin/configure-interfaces/virtual-wire-interfaces/vlan-tagged-traffic
"You can also use IP classifiers for managing untagged traffic. To do so, you must create a sub-interface with the vlan tag “0”, and define subinterface(s) with IP classifiers for managing untagged traffic using IP classifiers."
https://docs.paloaltonetworks.com/pan-os/10-1/pan-os-networking-admin/configure-interfaces/virtual-w... %20also%20use%20IP%20classifiers%20for%20managing%20untagged%20traffic.%20To%20do%20so%2C%20you%20must%20create%20a%20sub%2Dinterface%20with%20the%20vlan%20tag%20%E2% 80%9C0%E2%80%9D%2C%20and%20define%20subinterface(s)%20with%20IP%20classifiers%20for%20managing%20untagged%20traffic%20using%20IP%20classifiers
.
Stay tuned
Best regards
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-11-2023 06:56 AM
you can create vwire subinterfaces to hit on a tag, so that you can apply different zones per vlan, the base interface will accept untagged packets while the subinterfaces handle the tagged packets. on the untagged vwire object just leave the vlan tags blank, or set it to 0, on the tagged vwire object set your vlans separated by commas
PANgurus - Strata specialist; config reviews, policy optimization
- 2626 Views
- 1 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Anti-Spyware Behaviour and Inline Cloud Analysis in General Topics
- Why would what worked in Sophos would not work with PA in General Topics
- same subnet multiple VRs not working in General Topics
- PPPoE disconnect randomly in General Topics
- Dynamic User Group Auto Remediation configuration in Next-Generation Firewall Discussions