- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Create test syslog
- LIVEcommunity
- Discussions
- General Topics
- Re: Create test syslog
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-23-2015 07:30 AM
I want to know when our PBF rule hits by sending an email when sees the syslog. I want to test this but don't want to actually fail traffic over. There are test commands on the cli but haven't been able to find how to create a false syslog. Please let me know how to create a false syslog.
Thank you
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-05-2016 04:39 PM
So far, Palo Alto does not have capability to selectively filter system logs or alerts. Mostly such type of alerts can be implemented in some external NMS solutions.
This needs to be a feature request. I see there are feature requests already for both functionalities, i.e. ability to filter events and option to send alert on PBF monitoring events. Kindly check with the Palo Alto SE for the roadmap.
BR
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-23-2015 12:17 PM
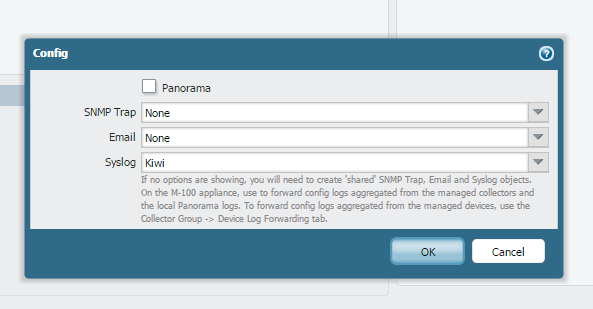
In "Log Settings" --> "Config" you can set that to send to your syslog server. Make a configuration change which should send that to your syslog server.
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-23-2015 02:30 PM - edited 12-23-2015 02:32 PM
If you want to test if your firewall is sending the logs to the syslog or not.
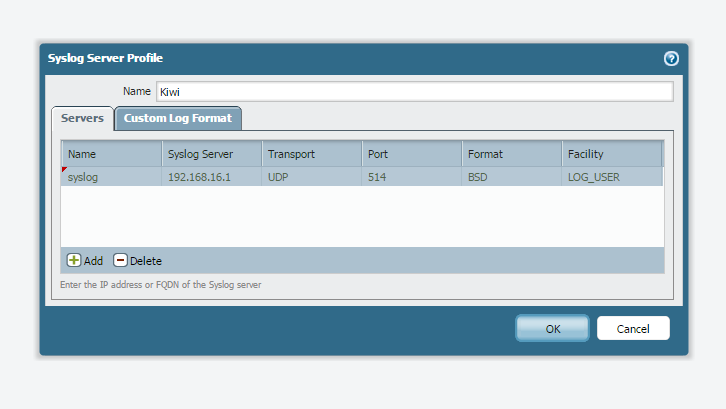
Step1 Configure syslog server Device>server profile configure the syslog
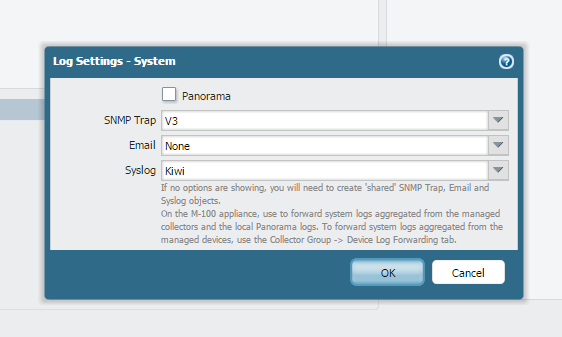
Step2. Log setting. select the syslog server profile for
system>information severity or for config
Step 3 Do a commit
Now if you navigate through the firewall tabs a system log of information severity will generated and firewall should send the logs to syslog. If you have selected the syslog for config as well then you will get the syslog for any config change.
Make sure the reachablilty to syslog is there. Check the service route if reachability is not there.
Hope this helps!
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-05-2016 02:28 PM
Thanks for the reply.
I'm not trying to make a "config" change show up to my syslog server. I want to get a system event regarding a PBF rule to sent the alert to my email.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-05-2016 02:30 PM
I want to know when our PBF rule hits by sending an email when sees the system log.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-05-2016 04:39 PM
So far, Palo Alto does not have capability to selectively filter system logs or alerts. Mostly such type of alerts can be implemented in some external NMS solutions.
This needs to be a feature request. I see there are feature requests already for both functionalities, i.e. ability to filter events and option to send alert on PBF monitoring events. Kindly check with the Palo Alto SE for the roadmap.
BR
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-06-2016 08:56 AM
Thank you, this would be really helpful. I've had feature request in the past, I'll add to the list.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-11-2016 12:40 PM - edited 01-11-2016 12:43 PM
Look into 'Swatch', its a relic but works. Send events to syslog as outlined then on your Linux host enable Swatch to parse syslog data (one or more log files) and send an alert on any keyword/event ID, etc. I use this for PAN URL, system and threat logs along with Cisco ASA log events. There are a lot of Swatch options including thresholds to suppress repeat events.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-11-2016 12:46 PM
I appreciate everyone's help. I believe where I was off was our threats send emails directly from the fw to to us. The fw will send complete syslogs but unable to parse out specific objects/strings. I'll have our solarwinds send over the specifics.
Thanks again.
- 1 accepted solution
- 15388 Views
- 8 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Assistance with LDAP Authentication in General Topics
- Prisma Access CIE and User-ID mapping not working for groups in Prisma Access Discussions
- Prisma cloud API access key permissions in Prisma Cloud Discussions
- XDR as "SIEM" (challenge for discussion) in Cortex XDR Discussions
- Unable to reach Palo Alto - Global Protect Portal. in GlobalProtect Discussions