- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Detecting / mitigating Cryptolocker
- LIVEcommunity
- Discussions
- General Topics
- Re: Detecting / mitigating Cryptolocker
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Detecting / mitigating Cryptolocker
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-15-2013 06:13 AM
Hello,
my customer is worried about Cryptolocker infections in the network - CryptoLocker Ransomware Infections | US-CERT. Do you happen to have any best practices or general tips on how to use PAN tools to detect and prevent Cryptolocker from infecting hosts?
Cheers,
Tuomo
- Labels:
-
Networking
-
Panorama
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-15-2013 06:36 AM
There are some preliminary notes at the research center saying to monitor crilock events.
And of course to make sure smtp is locked down for outbound access.
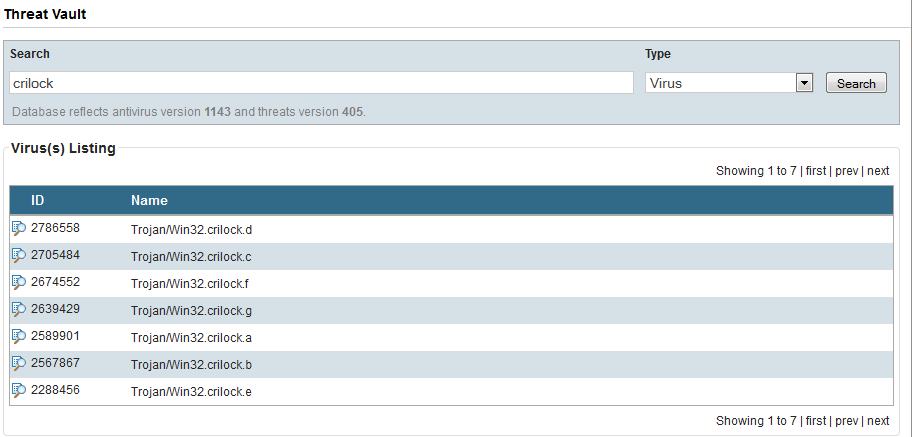
Steve
ACE PanOS 6; ACE PanOS 7; ASE 3.0; PSE 7.0 Foundations & Associate in Platform; Cyber Security; Data Center
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-18-2013 11:33 AM
Thanks for posting this. How do I confirm that the PA is scanning for these viruses?
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-05-2013 07:55 AM
The threat center has posted additional information in this blog.
http://researchcenter.paloaltonetworks.com/2013/11/palo-alto-networks-can-stop-cryptolocker/
ACE PanOS 6; ACE PanOS 7; ASE 3.0; PSE 7.0 Foundations & Associate in Platform; Cyber Security; Data Center
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-06-2013 04:43 AM
Hi
I'm thinking that I have properly configured security policies against Cryptolocker.
According to above link:
URL filtering policies in combination with File Blocking policies (block all files from unknown domains) adds an additional layer of protection, keeping the payload from being delivered.
How to realize that?
Could someone share their settings?
With regards
Slawek
- 4126 Views
- 5 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!



