- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
ERR_HTTP2_PROTOCOL_ERROR
- LIVEcommunity
- Discussions
- General Topics
- Re: ERR_HTTP2_PROTOCOL_ERROR
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
ERR_HTTP2_PROTOCOL_ERROR
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-08-2021 07:09 AM
Hi,
We have recently upgraded our PA3200 to 10.1.2 and while we try to access a few sites are not accessible. SSL Decryption has been disabled globally. Still, while we access the URL from our network on any browser we get the above error. I have tried adding the URL in the SSL Decryption exclusion list to see if that resolve the issue it did not work. Any help would be appreciated.
Best Regards,
Pradeep
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-08-2021 01:48 PM
Hello,
Do you have Strip ALPN enabled? This article will show you how to disable it, so if your settings are similar, its disabled globally.
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000PLpSCAW
Regards,
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-09-2021 04:49 AM
Hi Otakarklier,
The article is showing how to disable HTTP2 inspection when the decryption profile is enabled but in our case, we have disabled the SSL decryption globally.
Br,
Pradeep
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-09-2021 07:10 PM
Are you 100% sure that you aren't decrypting the traffic and have you verified that in your traffic logs on the firewall? The only reason I'm really bringing it up again is because without decryption the firewall shouldn't be causing any disruption with your HTTP/2 traffic at all. Outside of a website rightly having issues with HTTP/2, I've never seen that error on a firewall that isn't actively decrypting traffic.
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-10-2021 04:50 AM
Hi BPry,
Thanks for the reply. I have checked the traffic logs and the URL filter logs both traffic is passing the firewall and there is no decryption profile applied as SSL decryption is disabled globally. Also, we did a pcap on the firewall and found only http1.1 traffic passing at that instance.
Br,
Pradeep
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-11-2021 10:48 AM - edited 11-11-2021 10:56 AM
I would reach out to the service provider and ask them about this on their server:
"Having cross-signatures means that each of our RSA intermediates has two certificates representing the same signing key. One is signed by DST Root CA X3 and the other is signed by ISRG Root X1. The easiest way to distinguish the two is by looking at their Issuer field.
When configuring a web server, the server operator configures not only the end-entity certificate, but also a list of intermediates to help browsers verify that the end-entity certificate has a trust chain leading to a trusted root certificate. Almost all server operators will choose to serve a chain including the intermediate certificate with Subject “R3” and Issuer “ISRG Root X1”. The recommended Let’s Encrypt client software, Certbot, will make this configuration seamlessly."
The DST root is allegedly expiring and being retired (haven't verified this myself), cross-signing isn't something the networking teams adopted at scale, so in the event you don't have the full chain of certificates in your PAN-OS store (please go verify), the service will always show as unreachable as it will never present as valid because the firewall sees an expired intermediate when there's a valid co-signed path in parallel where the trust store chain lookup didn't follow. Same is true of any device without all certificates (browsers, servers, etc.).
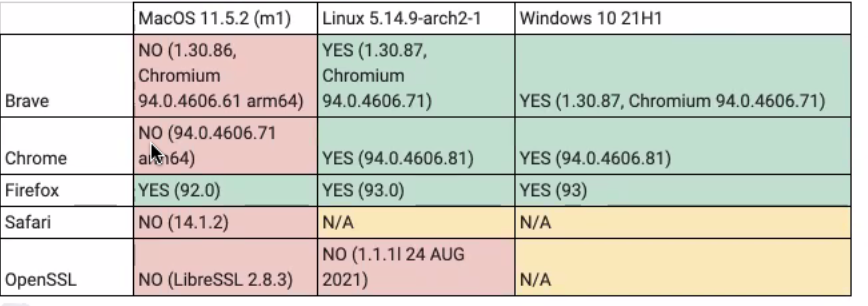
I've also attached a screenshot of which browsers (mixed bag) support cross-signing natively as well. Ultimately, decryption is hard but I think your answer lies in ensuring a full certificate chain is fully imported, trusted, etc.
I'm not convinced it's a remote service, nor am I unconvinced it's the firewall, in either case hope this context helps.
- 11512 Views
- 5 replies
- 1 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!