- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Exposing Videoconference - "Incomplete" traffic allowed
- LIVEcommunity
- Discussions
- General Topics
- Re: Exposing Video conference - "Incomplete" traffic allowed
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-24-2017 10:53 AM - edited 05-24-2017 10:55 AM
I have tried to expose Videoconference system behind Palo Alto.
Unfortunately using App ID in security policy I have seen Palo Alto allows a lot of "incomplete" traffic.
That's really an issue: When enabling h.323 in security Policy App id engine starts to allows every port in order to find something related to this protocol and obviously you will see in the traffic log incomplete as" session end-reason".
Which is the best practice in this kind of situation?
Thanks in ⎌advance
D!Z
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-26-2017 09:49 AM
You can apply zone protection on whatever zone you wish, and really you should have one for your DMZ and your OUTSIDE zones if you have both. Depending on how you have things setup would indicate what zone your traffic shows, but you can verify this in your traffic log by (addr in publicip) and seeing what your destination zone is for traffic going to that address.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-24-2017 10:55 AM
Do you have one public ip or range?
Do you SNAT traffic out from same IP that videoconference system from internet connects to you?
Palo Alto Networks certified from 2011
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-24-2017 10:58 AM
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-24-2017 11:23 AM
Can you share more details on how you are actually doing the NAT. H.323 shouldn't be allow every port by any means as H.323. Is this a Polycom unit that you are having troubles with?
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-25-2017 01:26 AM
Nope!
That's the issue
H.245 is a control channel protocol used with[in] H.323 communication sessions, and involves the line transmission of non-telephone signals.
Category:
collaboration
Subcategory:
voip-video
Technology:
client-server
Risk:
3
Standard Ports:
tcp/dynamic
How can I proceed with this protocol?! Should I Enable everything?!
Anybody has this issue before?
Thx
Luca
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-25-2017 01:40 AM
I think the only way to proceede is to define a port range with who has configured the Videoconference system and put that range in the NAT bidirectional rule.
Do you agree?
D!ZZZ
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-25-2017 05:20 AM - edited 05-25-2017 05:21 AM
Well tcp/dynamid does not mean that you permit application traffic on all ports.
You permit TCP 3way handshake on any port but if traffic that follows does not match application that is permitted then session is dropped by Palo.
Bad thing is that if you permit all tcp ports in then attackers can do port scan from outside.
Good example is that you never permit application SMTP and port ANY towards your email server because this will permit anyone outside to scan all ports on your mail server to identify what services are running.
Palo Alto Networks certified from 2011
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-25-2017 07:17 AM
Exactly
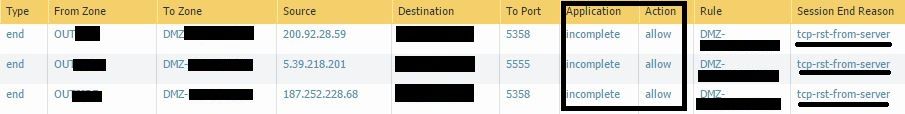
I'm worried about "port scan" because PA in order to identify an Application, allow the first packets to the server (SYN, SACK).
So I've seen from traffic a lot of attempt from outside to Videoconference server, allowed by Palo Alto:
NOTE** As you can see the reset is coming from server and packet is allowed
D!ZZ
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-25-2017 07:23 AM
Obviously that's a Palo Alto's default behavior .. But when you got an application such as h.245 that has defined as standard port "tcp/dynamic" .. You'll got an issue, because PA's starts to allow first packet (SYN, SACK) in order to identify h.245 application (A LOT OF PACKETS coming in)!
That's not great... 😞
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-25-2017 08:03 AM
Well there is not much that Palo can do - application is designed that way.
If you have video conference only with limited peers you can add their public IP into rule where you permit this traffic in from.
Or create External Dynamic List that pulls Video conference peer IP's from intranet site.
When people in company plan Video conference they just update intranet site and add peer to the list.
No firewall side reconfiguration needed.
Palo Alto Networks certified from 2011
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-25-2017 08:16 AM
Also
I'm tryng to configure a strong "Zone protection" profile..
🙂
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-25-2017 08:54 AM
Don't jump to strong Zone Protection immidiately.
Go in steps.
From my experience.
Company with 2 sites.
Strict ip and port scan restrictions in Zone protection.
Guy from one site tried to call to guy at other site.
He used Skype that likes to probe what open ports other peer has.
And firewall of site 1 blacklisted site 2. VPN and all intra company traffic were blocked.
Now with newer releases you can exclude some ip's in Zone protection so this helps 🙂
Palo Alto Networks certified from 2011
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-26-2017 07:42 AM
Do you think it's possible to apply "zone protection" on DMZ? Or I have to apply this profile on the "OUTSIDE" zone?
I have tried to apply it on DMZ, and test it (configured minimum threshold) with a port scan via NMAP.. No threat logs generated.
On which zone "zone protection" has to be applied?
BR
D!Z
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-26-2017 09:49 AM
You can apply zone protection on whatever zone you wish, and really you should have one for your DMZ and your OUTSIDE zones if you have both. Depending on how you have things setup would indicate what zone your traffic shows, but you can verify this in your traffic log by (addr in publicip) and seeing what your destination zone is for traffic going to that address.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-26-2017 11:11 AM
@TheRealDiz As @BPry mentioned you should enable Zone protection to both zones.
Traffic that is initiated from wan towards DMZ is checked by Zone protection profile on wan (ingress) zone.
Palo Alto Networks certified from 2011
- 1 accepted solution
- 9739 Views
- 14 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Connecting Cortex XSOAR to Internal Cloud Hosted Panorama for Prisma Access Integration in Cortex XSOAR Discussions
- some of endpoints might be exposed to risk due to report-only policies in Cortex XDR Discussions
- CPE for the Conferences or Summits in General Topics
- Checkov Secrets Framework Scanning exposes secrets in junit test output in Prisma Cloud Discussions
- How to configure ingress to Azure Load Balancers with PaloAlto-secured network in VM-Series in the Public Cloud