- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Filter Query Lexicon
- LIVEcommunity
- Discussions
- General Topics
- Re: Filter Query Lexicon
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-07-2015 01:18 PM
Hi there,
Is there a document that contains the dictionary of terms, and the description of the syntax of the PANOS filter query language?
I've looked through the knowledge base, but I didn't find anything that looks like a syntax document.
This would be specifically for using the filter query in the PANOS 6.0 GUI. I'm not concerned with the CLI syntax.
Thank you!
- Labels:
-
Management
-
Panorama
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-07-2015 02:30 PM
You can just click on + (add filter) symbol under Monitor --> Traffic or Threat or URL etc. and then use Add log filter to get desired results.
Helpful doc: How to Add, Save, Load, and Clear Log Filters
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-07-2015 02:22 PM
Just to clarify, you mean for filtering logs from the GUI under 'Monitor' ?
Example:
Monitor > Traffic
( addr.src in 172.16.81.2 ) and ( app eq dns )
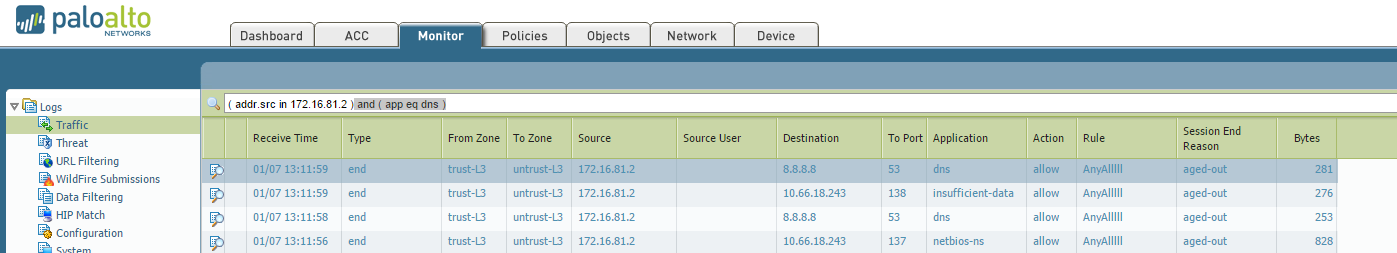
I don't see a KB article for this either. This may be due to how easy it is to just click any of the logs and it will populate the proper filter syntax for you. If you wanted to filter for a source IP address, you could click the source IP under any of the logs, then simply change the IP address in the search bar and click the green arrow to "Apply Filter".
Note: There are some KBs that do exist about this, but they are for very specific filters that you cannot easily figure out.
Example - Filtering Traffic Logs for Only Unidentified Users
Please do not forget to mark this thread as 'Answered' or mark any 'Helpful answered provided by any of our responses.
Thanks!
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-07-2015 02:30 PM
To truly appreciate the capability of this box i would recommend logging and alerting everything ![]() then tune out false positive or severity . Below is based on 6.0 but 6.1 has some additional http fields it can log.
then tune out false positive or severity . Below is based on 6.0 but 6.1 has some additional http fields it can log.
easiest thing to do is use the gui to do a filter then write it down but its pretty simple once you get it going and replace the eq with a contains or neq for negate (you could also put a ! to negate the filter) geq greater than or equal , leq less than or equal , (neq "") or (contains"") for is present .
You could also start with the ACC then move to the traffic logs once filters are setup.
Each log (traffic, threat,url,datafilter etc..) can have their specfic syntax . Also the syntax may overlap with the custom reports but not always. The syntax also doesnt' match doesnt' match up 100% with the traffic filters.
from traffic logs its : category-of-app eq media
for example from a custom report to filter app category of media syntax is : category-of-name eq media
same with sub categories
subcategory-of-app eq photo-video in traffic logs , subcategory-of-name eq photo-video in custom reports
The two mentioned also aren't available as a selectable attribute in the Add log filter gui
You can also enter some attributes that are NOT available in the dropdown ![]()
Some interesting filter examples in the traffic log
1. photo-video downloads greater than 100mb
subcategory-of-app eq photo-video and bytes_received geg 100000000
2. bytes sent greater than 1mb to destination country no US
bytes_sent geg 1000000 and dstloc neq US
3. filter for app category of media application NOT rtmp
category-of-app eq media and app neq rtmp
You can also nest multiple search terms
4. Any ip of from subnet 192.168.0.0/16 in source or dest , application is ssl and dest port is NOT 443
addr in 192.168.0.0/16 and app eq ssl and port.dst neq 443
5. looking for destination port 80 or 8080 that is not application web-browsing
((port.dst eq 80) or (port.dst eq 8080)) and app neq web-browsing
Some interesting filter examples in the threat log
If a device is managed by panorama there is a field 'URL' that shows up but this is actually additional info such as a file etc.. in the custom report the attribute value is 'misc' . Even if a device is not managed by the firewall you can filter for misc . In a detailed log view under 'threat detail' you'll also see the option of URL . In panorama you can simply look at the URL field in the threat logs
1. To see if a medium severity or higher threat has any value for url / misc
severity geq medium and misc neq ""
2. Virus that matches smtp
subtype eq virus and app eq smtp
3. threats that are not a virus that contains a .doc or .docx file name (only the data filtering logs lets you filter by file type / threatid for a file so searching by file ext could provide some useful data)
!(subtype eq virus) and ((misc contains .doc) or (misc contains .docx))
Some interesting filter examples in the URL log
1. find a url that partially matches vpn.
url contains vpn.
2. category malware and application ssl or port 443
category eq malware and ((app eq ssl) or (port.dst.eq 443))
Now for some interesting filter examples in the Data Filtering
1. Findout if people are downloading pirated movie / tv shows via http .
filename that contains hdtv (commonly used for illegal ripped hdtv shows), threatid eq 52104 (threat id to match file type mp4)
More info http://en.wikipedia.org/wiki/Pirated_movie_release_types
filename contains hdtv and threatid eq 52104
2. All file types PE that were not part of a software update category
subcategory-of-app neq software-update and threatid eq 52060
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-07-2015 02:30 PM
You can just click on + (add filter) symbol under Monitor --> Traffic or Threat or URL etc. and then use Add log filter to get desired results.
Helpful doc: How to Add, Save, Load, and Clear Log Filters
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-07-2015 02:58 PM
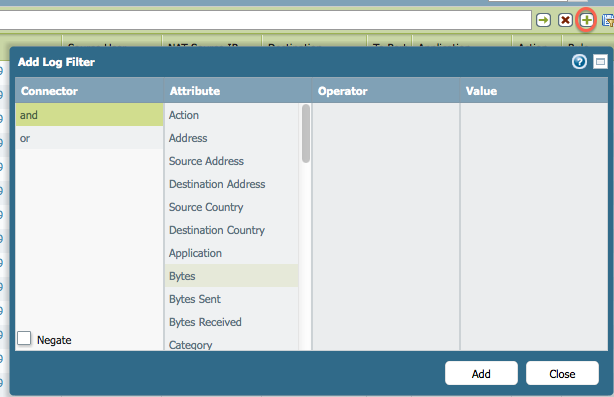
I don't know of a list, but the wizard for the filter is pretty easy to setup whatever you need,
Hit the Plus icon + on the right and then use the menu to construct your desired filter settings.
ACE PanOS 6; ACE PanOS 7; ASE 3.0; PSE 7.0 Foundations & Associate in Platform; Cyber Security; Data Center
- 1 accepted solution
- 8990 Views
- 4 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Problem with Conditional Task Not Matching XQL Output in Cortex XSIAM Playbook in Cortex XSIAM Discussions
- XQL question in Cortex XSIAM Discussions
- RQL Query Works in Investigate > Search but Fails in Policy Definition (Terraform v1.5.7 Example Included) in Prisma Cloud Discussions
- xql query for process in Cortex XDR Discussions
- Traffic Logs missing from subset of datetime range when using certain filters? in General Topics



