- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Firewall Unable to connect to ISP Router
- LIVEcommunity
- Discussions
- General Topics
- Re: Firewall Unable to connect to ISP Router
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-17-2023 02:43 AM
I m setting up a small office network where the endpoints are connecting to a switch that is in turn trunked to a PA220 Firewall . The firewall external interface is configured with a static IP address within the same range as the ISP IP router .
However it appears that neither the ISP router or the Palo can receive arp entries off each other let alone ping each other
The ISP provider has also confirmed the internet connectivity is working fine .
Can anyone please advise ?
Thanks
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-20-2023 06:04 AM
Hi @HassanThiam ,
I am glad the Internet is working now. If my answer helped you get the ping working, please accept it as the solution.
With regard to the VPN, we would be glad to help on this thread, but technically it is a different topic.
A good place to start with IPsec is the green lights under Network > IPSec Tunnels, and Monitor > Logs > System. As @Raido_Rattameister mentioned, NO_PROPOSAL_CHOSEN means the crypto settings do not match and the tunnel is not up.
Thanks,
Tom
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-17-2023 05:15 AM - edited 01-17-2023 05:15 AM
If you configure same public IP and gateway on your laptop and connect ISP cable directly to laptop can you get to internet or see arp from ISP?
If yes we can help you troubleshoot Palo.
If not then ISP needs to check their config.
Palo Alto Networks certified from 2011
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-17-2023 07:00 AM
Hi
Thanks for the feedback . Unfortunately at the time, I was unable to configure my laptop IP address and Gateway because of admin restrictions ( working to get elevated privileges at the moment ) . The ISP sent an engineer onsite to check internet reachability and he confirmed connectivity to the ISP default gateway by plugging a device directly into the router .What are the sort of config that could prevent the firewall from seeing the router ?
Thanks
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-17-2023 07:37 AM
ISP provides connectivity over access port right (not tagged/trunk port)?
Ask ISP if speed/duplex is set to auto/auto or if they have hardcoded those settings.
If second option you need to match your side.
Palo Alto Networks certified from 2011
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-17-2023 09:49 AM
Hi
I will enquire with the ISP about the speed/duplex settings , I would have thought they will be set to auto
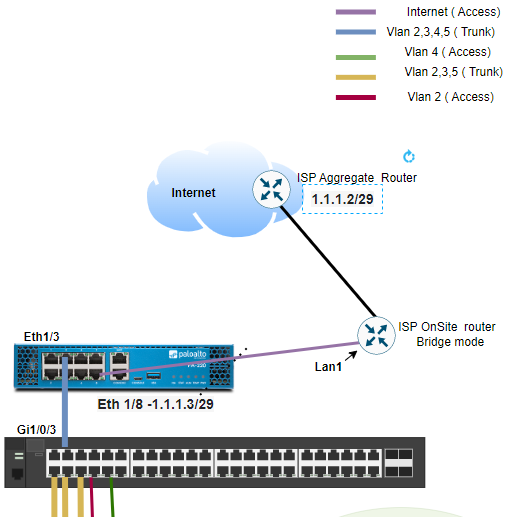
Yes the connectivity is provided through an access port . As per the attached topology the firewall connect to an Onsite router that only function in bridge mode with so layer 3 communication is between the firewall and the aggregate router .
The ISP engineer that visited the site confirmed the Internet was working by plugging a portable device into the Onsite router ( LAN 1) and could get to the ISP Aggregate Router using IP addresses within the same range .
Let me know if you have any further suggestions
Thanks in advance
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-19-2023 02:31 AM
Good Morning ,
I can now confirm I have Internet connectivity but I have set up a VPN with an ASA that s not coming up . The outside interface of the Palo is up and can ping the ASA outside interface .
Any advice will be greatly appreciated
Thanks
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-19-2023 04:12 AM
Hi @HassanThiam ,
- Do you have an interface profile applied to your interface connected to the ISP that allows pings?
- https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000ClMmCAK
- Otherwise pings will not be allowed, and an ARP request will not be sent.
- Do you source your pings from the IP applied to the interface connected to the ISP?
- https://live.paloaltonetworks.com/t5/blogs/tips-amp-tricks-how-to-ping-from-the-cli/ba-p/468784
- Otherwise the pings will be sourced from the management IP address.
- Again, no ARP request will be sent out the ISP interface.
- Do you see the pings in the traffic logs (Monitor > Logs > Traffic)?
- Pings from an interface will be allowed by the intrazone-default rule.
- Logging will need to be enabled on the rule. https://docs.paloaltonetworks.com/best-practices/9-1/data-center-best-practices/data-center-best-pra...
- You can also enable logging on the interzone-default rule. Then you should see all IP traffic through the data plane, allowed or dropped.
- Logs confirm the NGFW is attempting to send pings.
- Have you verified the NGFW is not receiving ARP by using the "show arp" command on the CLI?
- You should see a MAC address (received) or incomplete (not received).
- The incomplete times out fairly quickly. The command needs to be run as soon as the ping is done.
Thanks,
Tom
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-20-2023 01:45 AM
Hi Tom
Thanks for the feedback .
- Do you have an interface profile applied to your interface connected to the ISP that allows pings?
- https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000ClMmCAK
- Otherwise pings will not be allowed, and an ARP request will not be sent.
- Yes I do have an interface management profile that accept pings
- Do you source your pings from the IP applied to the interface connected to the ISP?
- https://live.paloaltonetworks.com/t5/blogs/tips-amp-tricks-how-to-ping-from-the-cli/ba-p/468784
- Otherwise the pings will be sourced from the management IP address.
- Again, no ARP request will be sent out the ISP interface.
- When I source it from the Management interface it doesn't work but works from the NGFW outside interface
- Do you see the pings in the traffic logs (Monitor > Logs > Traffic)?
- Pings from an interface will be allowed by the intrazone-default rule.
- Logging will need to be enabled on the rule. https://docs.paloaltonetworks.com/best-practices/9-1/data-center-best-practices/data-center-best-pra...
- You can also enable logging on the interzone-default rule. Then you should see all IP traffic through the data plane, allowed or dropped.
- Logs confirm the NGFW is attempting to send pings.
- Yes I can see the pings from the traffic logs
- Have you verified the NGFW is not receiving ARP by using the "show arp" command on the CLI?
- You should see a MAC address (received) or incomplete (not received).
- The incomplete times out fairly quickly. The command needs to be run as soon as the ping is done.
- To be confirmed
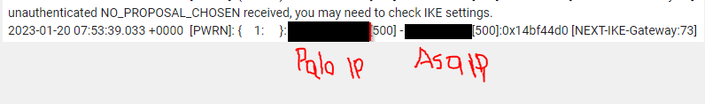
As per the topology I can t get the tunnel to the ASA working although the IKE parameters seem to match . The outside interface of the Palo can ping the ASA though . From an ASA perspective I can t see nothing on the logs .
This s the message I get from the NGFW .
Any help will be greatly appreciated
Thanks
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-20-2023 05:21 AM
Crypto settings don't match.
Do you manage ASA side as well to check config?
"show vpn-sessiondb detailed l2l" is helpful to use on ASA side.
If you can't get this info then next step is to turn Palo side to passive mode and figure out what ASA is negotiating with using packet capture.
Palo Alto Networks certified from 2011
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-20-2023 06:04 AM
Hi @HassanThiam ,
I am glad the Internet is working now. If my answer helped you get the ping working, please accept it as the solution.
With regard to the VPN, we would be glad to help on this thread, but technically it is a different topic.
A good place to start with IPsec is the green lights under Network > IPSec Tunnels, and Monitor > Logs > System. As @Raido_Rattameister mentioned, NO_PROPOSAL_CHOSEN means the crypto settings do not match and the tunnel is not up.
Thanks,
Tom
- 1 accepted solution
- 8490 Views
- 9 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Prisma Access with ECMP in Prisma Access Discussions
- CIE for user/group mapping for firewall on-premise in General Topics
- Alarm contacts /Power supply PA-1420 in General Topics
- SCM Essentials Questions in Strata Cloud Manager
- Unable to reach Palo Alto - Global Protect Portal. in GlobalProtect Discussions