- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
How to setup No-IP Dynamic DNS on Palo Alto PAN-OS 9.0.12
- LIVEcommunity
- Discussions
- General Topics
- How to setup No-IP Dynamic DNS on Palo Alto PAN-OS 9.0.12
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
How to setup No-IP Dynamic DNS on Palo Alto PAN-OS 9.0.12
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-25-2020 01:59 PM - edited 12-26-2020 07:10 AM
Good day all,
I spent quite some time figuring out how to setup the No-IP dynamic DNS service on my PA-220 running PAN-OS 9.0.12 and I want to share how I did it as it wasn't a straightforward process for me and I am sure it isn't for others either.
Why do you want to do this?
This will allow you to use a fully qualified domain name (FQDN) to refer to an outside address. This can be incredibly useful if you use DHCP to receive an external address, because without using a FQDN you would need to update each instance of that external IP when your address changes. This will allow the service running on the firewall to check in with No-IP and update the IP address if it changes. By default it checks in daily.
What you need
PAN-OS 9.0.0 or higher (I am using 9.0.12 and have not tested it on earlier versions)
Signed up for a dynamic DNS service through No-IP
A Windows 10 PC (you could do this from a different OS but the specific examples below will need to be modified; however, the overall process will be the same and hopefully you find the process helpful)
References
Palo Alto Dynamic DNS help pages
Step 1 - Creating a No-IP account and a hostname
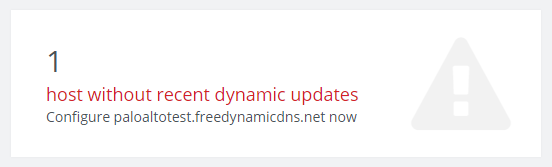
Sign up for a No-IP user account and create a dynamic DNS hostname. In my example I am using paloaltotest.freedynamicdns.net as the host. By default it will create an "A" record which is what I want as I am using IPv4. I haven't tried this is IPv6, but it would likely work with an "AAAA" record as this is also supported by No-IP. You can also used their managed DNS service using your own domain and update an A record using their dynamic DNS service.
You can verify that the hostname has been created by clicking on the "No-IP Hostnames" menu in the Dashboard.
The IP address will default to the IP of the computer you created the hostname from.
You can also verify that the host hasn't received any updates from the main dashboard for the No-IP service (you see this when you log in). Once we have setup the service on the Palo Alto this will change.
Step 2: Obtaining the SSL certificates for the No-IP Dynamic DNS service.
You will need to download the SSL certificates from No-IP and install them onto your Palo Alto firewall. Normally this would be pretty trivial, but it isn't possible to visit their registration site from a web browser. To get around this we can use OpenSSL and download the certificate from the command line. Below are the steps to do this.
If you don't already have OpenSSL, you can obtain binaries for your system from the OpenSSL website. In my example, I use the Win 64 OpenSSL v1.1.1i Light version from Shining Light Productions. I chose this for no specific reason other than it was the first in the list. After you have installed the binaries, you will need to open the ""Win64 OpenSSL Command Prompt" from your Windows Start Menu.
The output on the newly opened command prompt should look something like this:
Win64 OpenSSL Command Prompt
OpenSSL 1.1.1i 8 Dec 2020
built on: Tue Dec 8 20:54:45 2020 UTC
platform: VC-WIN64A
options: bn(64,64) rc4(16x,int) des(long) idea(int) blowfish(ptr)
compiler: cl /Z7 /Fdossl_static.pdb /Gs0 /GF /Gy /MD /W3 /wd4090 /nologo /O2 -DL_ENDIAN -DOPENSSL_PIC -DOPENSSL_CPUID_OBJ -DOPENSSL_IA32_SSE2 -DOPENSSL_BN_ASM_MONT -DOPENSSL_BN_ASM_MONT5 -DOPENSSL_BN_ASM_GF2m -DSHA1_ASM -DSHA256_ASM -DSHA512_ASM -DKECCAK1600_ASM -DRC4_ASM -DMD5_ASM -DAESNI_ASM -DVPAES_ASM -DGHASH_ASM -DECP_NISTZ256_ASM -DX25519_ASM -DPOLY1305_ASM -D_USING_V110_SDK71_ -D_WINSOCK_DEPRECATED_NO_WARNINGS -D_WIN32_WINNT=0x0502
OPENSSLDIR: "C:\Program Files\Common Files\SSL"
ENGINESDIR: "C:\Program Files\OpenSSL\lib\engines-1_1"
Seeding source: os-specific
C:\Users\yourusername>
Input the command to grab the certificate:
openssl s_client -connect dynupdate.no-ip.com:443
You will notice that the domain for the update service is is no-ip.com and NOT noip.com. If you visit dynupdate.no-ip.com with a web browser you will find that you get auto-forwarded to noip.com, which makes it very hard to download the certificate from something like a web browser.
After you fund the command, it will output a bunch of text such as the following:
CONNECTED(0000019C)
depth=1 C = GB, ST = Greater Manchester, L = Salford, O = Sectigo Limited, CN = Sectigo RSA Domain Validation Secure Server CA
verify error:num=20:unable to get local issuer certificate
verify return:1
depth=0 CN = *.no-ip.com
verify return:1
---
Certificate chain
0 s:CN = *.no-ip.com
i:C = GB, ST = Greater Manchester, L = Salford, O = Sectigo Limited, CN = Sectigo RSA Domain Validation Secure Server CA
1 s:C = GB, ST = Greater Manchester, L = Salford, O = Sectigo Limited, CN = Sectigo RSA Domain Validation Secure Server CA
i:C = US, ST = New Jersey, L = Jersey City, O = The USERTRUST Network, CN = USERTrust RSA Certification Authority
---
Server certificate
-----BEGIN CERTIFICATE-----
MIIFsTCCBJmgAwIBAgIQSGWWp5Bo5ALtPf3YF0FXlDANBgkqhkiG9w0BAQsFADCB
jzELMAkGA1UEBhMCR0IxGzAZBgNVBAgTEkdyZWF0ZXIgTWFuY2hlc3RlcjEQMA4G
A1UEBxMHU2FsZm9yZDEYMBYGA1UEChMPU2VjdGlnbyBMaW1pdGVkMTcwNQYDVQQD
Ey5TZWN0aWdvIFJTQSBEb21haW4gVmFsaWRhdGlvbiBTZWN1cmUgU2VydmVyIENB
MB4XDTIwMTAyNjAwMDAwMFoXDTIxMTAyNjIzNTk1OVowFjEUMBIGA1UEAwwLKi5u
by1pcC5jb20wggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQCuugOgTd8W
JNNpQKSZBYUqT5jP8b4u7HsuFg3NLygAX+Tpw1td0N1ypuTvPO4CswV8TEiRNNVb
pH5Z6jHlCe/s/z6G5ZWYnW22mPKyWPQLAQJUHGLfHK2J/gH0Ja47/UwnxVgaDxxe
hN2mxL/8/REr3V6a9R1+UXmRyYt1Xxl9V4kVJDZBUqKhSJXRJNZTV7qmOEIEJWtV
lE3MTJifkiMwh98m+D1gxZXdtnQ1tJqGRsm2MU6znilpZEXMTuixG3plwNBnVCpx
FvWESvp7XXAEU07dQbE8BMa1HJHnbXPg449skOmIkFWy+kbX5M5iBFX/tNgoLZzd
98AuVkRBDsENAgMBAAGjggJ/MIICezAfBgNVHSMEGDAWgBSNjF7EVK2K4Xfpm/mb
BeG4AY1h4TAdBgNVHQ4EFgQU0+tscIVxPAT9bssXwDHDIfG39SQwDgYDVR0PAQH/
BAQDAgWgMAwGA1UdEwEB/wQCMAAwHQYDVR0lBBYwFAYIKwYBBQUHAwEGCCsGAQUF
BwMCMEkGA1UdIARCMEAwNAYLKwYBBAGyMQECAgcwJTAjBggrBgEFBQcCARYXaHR0
cHM6Ly9zZWN0aWdvLmNvbS9DUFMwCAYGZ4EMAQIBMIGEBggrBgEFBQcBAQR4MHYw
TwYIKwYBBQUHMAKGQ2h0dHA6Ly9jcnQuc2VjdGlnby5jb20vU2VjdGlnb1JTQURv
bWFpblZhbGlkYXRpb25TZWN1cmVTZXJ2ZXJDQS5jcnQwIwYIKwYBBQUHMAGGF2h0
dHA6Ly9vY3NwLnNlY3RpZ28uY29tMCEGA1UdEQQaMBiCCyoubm8taXAuY29tgglu
by1pcC5jb20wggEFBgorBgEEAdZ5AgQCBIH2BIHzAPEAdgB9PvL4j/+IVWgkwsDK
nlKJeSvFDngJfy5ql2iZfiLw1wAAAXVmloKcAAAEAwBHMEUCICR5OTujKnepdKx/
KMHAYrCllzxUbNpcE+Mst3ZUhRN/AiEAyDZnMRn/ASBC+0zrYECMwZ3kgiVe1zLk
/r/C7moPUOkAdwCUILwejtWNbIhzH4KLIiwN0dpNXmxPlD1h204vWE2iwgAAAXVm
loPfAAAEAwBIMEYCIQDpEx7EMietEAvyGfDz7A0J82HNxCKyrihg+cWDbO70fAIh
AIQYsh4CFT+nq3px3Kv69Vmr1TWtvS58O969XNnevY0AMA0GCSqGSIb3DQEBCwUA
A4IBAQBQ0HTYRE012ek02wph8nPaIw+zTfYCeL8bb20wvmDWi1PSxUV7i7jBB+Nc
1ClWxk3DIfdfVy8+bHgaBpEh5CM5dLCDB7ll5Bh97BZtXHuM+KNW/ga2TIIE45Lb
hK7H9qUOg/2Gu8SV5t+Ofs2fO2J9OSH/m2EZ/vZ3dRxmwN1IQwXf97aBQPq8QqVi
wzNUt7Lcf28XEBxYgGFayKIGNaioWyr4GLf5VVH28gk0aIHjKMOTXw8RVd583+0f
aXQUqac4QW9DhwvAihMftrQ1FqlPa9S7/wulHv/4iexUHwheP3+zM10BX14wUsXK
WaNkZ56ATcL3SA8HCZYeGc4ImzhS
-----END CERTIFICATE-----
subject=CN = *.no-ip.com
issuer=C = GB, ST = Greater Manchester, L = Salford, O = Sectigo Limited, CN = Sectigo RSA Domain Validation Secure Server CA
---
No client certificate CA names sent
Peer signing digest: SHA256
Peer signature type: RSA-PSS
Server Temp Key: X25519, 253 bits
---
SSL handshake has read 3515 bytes and written 401 bytes
Verification error: unable to get local issuer certificate
---
New, TLSv1.3, Cipher is TLS_AES_256_GCM_SHA384
Server public key is 2048 bit
Secure Renegotiation IS NOT supported
Compression: NONE
Expansion: NONE
No ALPN negotiated
Early data was not sent
Verify return code: 20 (unable to get local issuer certificate)
---
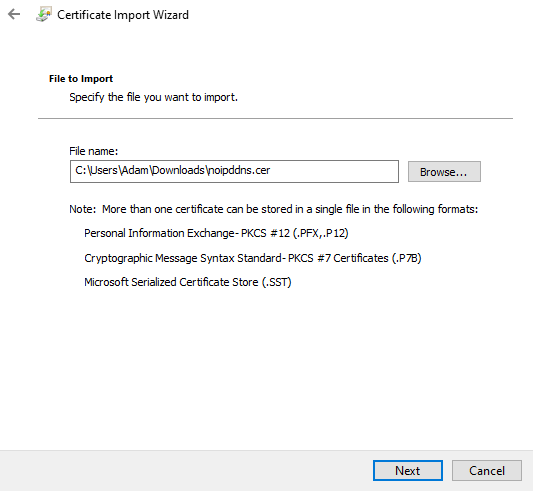
What we are interested in is the actual certificate. This is found at the -----BEGIN CERTIFICATE----- to -----END CERTIFICATE----- portion. What we can do is highlight this section (including the Begin Certificate and End Certificate portion into a text document and save it as noipddns.cer.
Next, we need to get the intermediate and root certificates as we will also need to install these on the Palo Alto firewall. An easy way to do this is to install the certificate that we just downloaded onto our PC and view the certificate chain and export those two certificates. To do this we need to open "Manage User Certificates" from the Windows control panel.
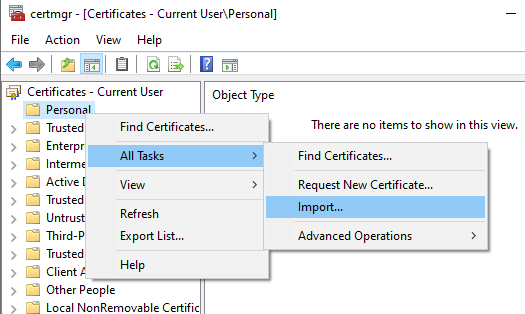
From the certificate manager, right click "Personal", select "All Tasks" and "Import...".
From the import wizard that opens, select "Next" which will take you to the "File to Import" screen, click "Browse" on the next screen and navigate to the certificate we saved earlier and then click "Next".
Save it in the personal certificate store, click "Next".
Click "Finish" on the next screen. You should get a notification that the import was successful. Click "OK".
You should now see the certificate.
Next we want to open the certificate to view the certificate path. Double click on *.no-ip.com to open the properties window and click on the "Certification Path" tab.
What we want to do next is export the intermediary and root certificates ("Sectigo RSA Domain Validation Secure Server CA" and "Sectigo" respectively). This way we can install them on the Palo Alto firewall. First let's export the intermediate certificate. Click on "Sectigo RSA Domain Validation Secure Server CA" and then click "View Certificate".
From there, click the "Details" tab, and then click "Copy to File".
This will bring up the Certificate Export Wizard. Click "Next" on the first screen. The following screen will give you options to export. Select "Base-64 encoded X.509 (.CER)" and click "Next".
Name it noipintermediate.cer and save it in the same location as the no-ip certificate we saved earlier.
Next we want to export the root "Sectigo" certificate. Follow the same steps as above, but select "Sectigo" to export and save it as noiproot.cer. You should now have exported three certificates.
Step 3 - Configuring the Palo Alto firewall
There are a few things that you need to keep in mind with the following steps. You need to have a working configuration where you are using DHCP on your external layer 3 interface. In my case it is ethernet1/1, yours may be different. I have been told that if you have access locked down, you need to ensure that the external interface can talk to the following addresses to conduct updates (I didn't have to do this, so I cannot vouch for this specific information):
dynupdate.no-ip.com. 47 IN A 52.9.108.157
dynupdate.no-ip.com. 47 IN A 54.219.9.206
Next you can log into your Palo Alto firewall and navigate to the certificates by going to "Device" -> "Certificate Management" -> "Certificates". We will install the three certificates here. Click "Import".
First I install the no-ip certificate. In my case I named it "NoIPCertificate".
You will need to do the same for the intermediate and root certificates that we saved. When you are done, your certificate tree should look like this:
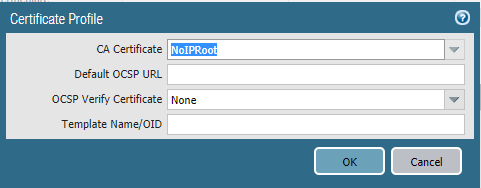
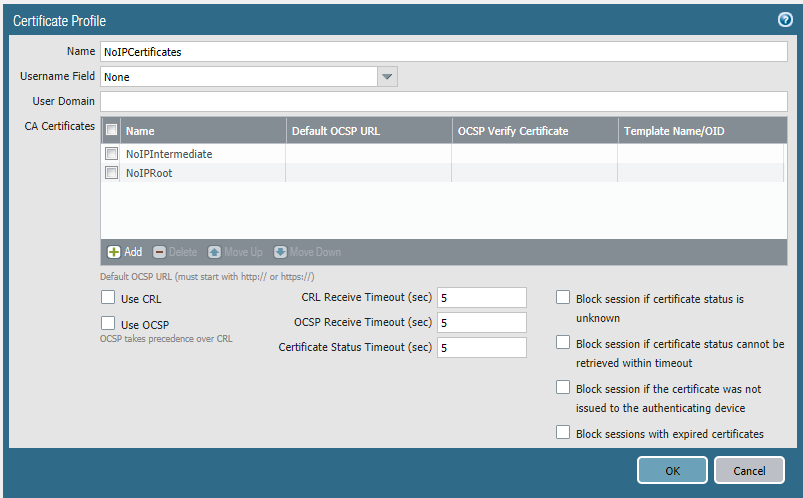
Next we can create a certificate profile. The link will be just under "Certificates" or you can get there by going to "Device" -> "Certificate Management" -> "Certificate Profile". Click "Add". I called the profile "NoIpCertificates". Click Add.
We will need to add the intermediate and root certificates.
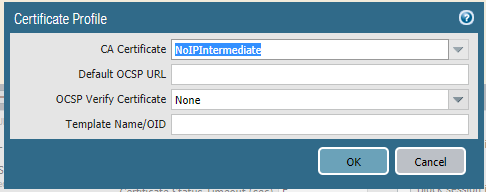
Once you have added them, it should look like this, click "OK".
Your profile should now show up in the list like this:
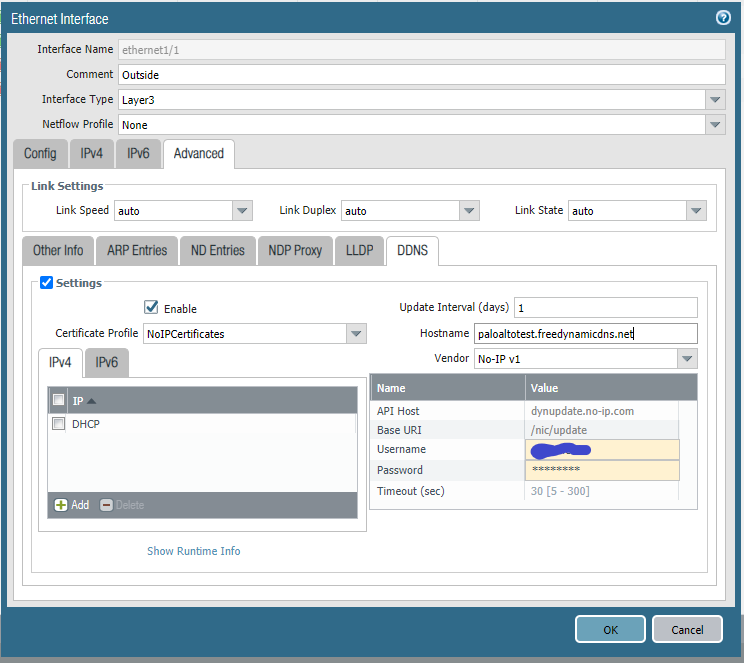
Next we can configure the Dynamic DNS service. As I stated above, my external IP is on ethernet1/1, yours may be different. Click on your appropriate interface.
From there click the "Advanced" tab:
From the advanced tab, click the "DDNS" tab.
Click, "Settings", "Enable", select the certificate profile we created, add the "DHCP" IP, select "No-IP v1" as the vendor, enter the hostname you are using (my example is being used below), and enter your No-IP username and password. Click "OK"
Next we will commit our changes and wait for them to be applied.
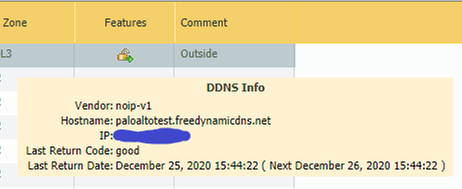
The interface page should refresh and you can now mouse-over the features icon for the interface and see the message.
If all is good, you should see something like this:
You can also verify that the service is working by viewing your No-IP Dashboard and seeing that the updates are being received:
Troubleshooting
If there is an error, you might see something like this:
Since "bad" isn't a terribly helpful return code, we can dig into the logs by navigating to "Monitor" -> "System" and doing a search for DDNS.
(description contains DDNS)
In the example below, we get a better server response that gives us a clue. In this case it returns "nohost". I check out the address, and see that there is a typo in the host name I provided.
You will want to ensure that the certificates remain valid. You will need to update them from time to time. You should see a certificate error in the logs once they have expired as they should be rejected when the service attempts to check in.
Result codes that you will receive back from No-IP can be found on their integration website. These will help you interpret what is happening.
In Closing
I hope that this can help someone out there. I spent quite some time trying to figure out the certificate portion of this as well as trying to understand what to enter where.
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-30-2020 09:02 AM
This is really great stuff! Thanks for posting this! 🙂
PANgurus - Strata & Prisma Access specialist
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-16-2021 09:51 PM
Anyone done this on v10, mine seems to be stuck on
admin@PA-220> show dns-proxy ddns interface name ethernet1/1
Interface: ethernet1/1
noip-v1
<domain name> (Public IP)
Last return code: initalizing
Last return date (hh:mm:ss):
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-27-2021 10:13 AM
Hi,
On the LAB you have select interface -(DHCP), But here we have PPOE link, what I need to select
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-27-2021 11:26 AM
No idea. I don't have an option to test out PPOE and to be honest, haven't touched PPOE for 10 or more years! Hopefully someone with some experience with PPOE connections can chime in.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-27-2021 11:27 AM
I haven't done this from scratch on v10 yet, but I did complete an upgrade and it worked without any modification. Are you still experiencing issues?
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-27-2021 11:16 PM
Guys, Today evening i am setting up on ppoe link, can you help me out with some show commands to verify the settings and connections for dyndns
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-03-2021 01:08 PM - edited 11-03-2021 01:11 PM
We are experiencing issues on v10 and currently seeking a solution.
DDNS has been 'initializing' without posting a failure in system logs for awhile.
Any additional troubleshooting paths?
show dns-proxy ddns interface name ethernet1/1
Interface: ethernet1/1
noip-v1
<ddns> ( <pubip> )
Last return code: initalizing
Last return date (hh:mm:ss):
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-29-2021 07:00 AM
I recently set up the DDNS function with No-IP, registering/setting the address for an address that had a cert (for the DDNS name) from No-IP. The firewall kept returning a "bad" status and the error "Server response: Peer certificate cannot be authenticated with given CA certificates'". I used the information above to grab the correct chain and the top level cert for the chain was already trusted in the "Default Trusted Certificate Authorities" section of the firewall. Although it was trusted already, I could not add it to the cert profile and the firewall did not use it as part of the check.
In order to fix the error, I had to export the top level CA cert from the default trusted CA list and re-import to the firewall. The top level CA cert was then shown in the chain, I was able to add it to the cert profile and the address registration to the DDNS name was successful.
Mike
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-10-2022 08:21 AM
Very helpful guide. Before I found this I wasted a lot of time and effort. Thank you very much! Worked on OS 10.1.3
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-15-2022 06:26 AM
Happy to hear that this was helpful. Too bad you hadn't found it earlier!
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-22-2023 02:48 AM
@nevolex ,
Configure DDNS for FW Interfaces
Kind regards,
-Kiwi.
Cheers,
Kiwi
Please help out other users and “Accept as Solution” if a post helps solve your problem !
Read more about how and why to accept solutions.
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-27-2023 09:16 PM
Do we have to buy the No-IP certificate before proceeding?
- 33225 Views
- 18 replies
- 18 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Can you configure clientless VPN in SCM ? in GlobalProtect Discussions
- Palo Alto Unable to Download Software Updates in Next-Generation Firewall Discussions
- How to disable firewall from contacting hawkeye.* in General Topics
- Request Advice – BGP Failover Route-Based IPsec VPN With WatchGuard (WG) in Next-Generation Firewall Discussions
- SNMP BULK REQUEST in Next-Generation Firewall Discussions