- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
issues with ssh access from macos/ linux
- LIVEcommunity
- Discussions
- General Topics
- Re: issues with ssh access from macos/ linux
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
issues with ssh access from macos/ linux
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-05-2023 04:44 PM
Hi folks I am having issues with access via ssh from macos/ linux pcs
pc ~ % ssh admin@10.10.10.1
Unable to negotiate with 10.10.10.1 port 22: no matching host key type found. Their offer: ssh-rsa
I can access it using this modified command:
ssh -oHostKeyAlgorithms=+ssh-rsa admin@10.10.10.1
I have added these options to ssh profile, restarted ssh server/ rebooted as well for testing, but still getting same results
Unable to negotiate with 10.10.10.1 port 22: no matching host key type found. Their offer: ssh-rs
Does anyone know what needs to be configured on the palo alto to resolve ssh compatibility issues?
thank you
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-07-2023 06:13 PM
Hi @nevolex ,
Is this a VM-Series FW hosted in the public cloud?
Stay Secure,
Jay
Don't forget to Like items if a post is helpful to you!
Please help out other users and “Accept as Solution” if a post helps solve your problem !
Read more about how and why to accept solutions.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-18-2023 02:52 AM
Did you select the SSH Service Profile you just made on Device\Setup\Management\SSH Management Profile Settings? And then restart the ssh server. (it will tell you to do so after commit)
I've just made the same setting for the same reason and missed this step.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-18-2023 06:45 PM
Hello,
For a successful ssh connection at least one mutually-supported choice for each parameter, OpenSSH considers SSH-RSA as a weak algorithm and it has been deprecated since OpenSSH 8.8, it is still supported but disabled by default.
Can you try to connect to the FW by adding the following to your command line: -oHostKeyAlgorithms=+ssh-rsa
Network Security Engineer
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-19-2023 02:32 PM
This is a problem for us as well. Is there a way to have the PA appliance generate keys using SHA2+? I've tried setting the server profile to use ECDSA 256+ and the connection still fails,.. likely because the SSH server is still trying to present the RSA version... I would have expected this to use ECDSA only, and not try and present ssh-rsa keys to the client... eg.
debug2: reserved 0
debug1: kex: algorithm: ecdh-sha2-nistp384
debug1: kex: host key algorithm: (no match)
Unable to negotiate with <redacted> port 22: no matching host key type found. Their offer: ssh-rsa
ssh {
profiles {
mgmt-profiles {
server-profiles {
default_high_security {
ciphers [ aes256-cbc aes256-gcm aes256-ctr];
kex [ ecdh-sha2-nistp384 ecdh-sha2-nistp521];
mac [ hmac-sha2-256 hmac-sha2-512];
session-rekey {
data default;
interval default;
packets default;
}
default-hostkey {
key-type {
ECDSA 384;
}
}
}
}
}
}
regenerate-hostkeys {
mgmt {
key-type {
ECDSA {
key-length 256;
}
}
}
}
mgmt {
server-profile default_high_security;
}
}
[edit deviceconfig system ssh]
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-22-2023 04:01 AM
This worked. Thank you!
Palo Alto Networks® | 3000 Tannery Way | Santa Clara, CA. 95054 | Mobile: +1-650-743-6232
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-03-2024 03:02 PM
This changed in PanOS 10.2 and higher, you can verify using "nmap --script ssh2-enum-algos -sV -p 22 192.168.1.1" you will find that:
| server_host_key_
| ssh-rsa
| rsa-sha2-512
| rsa-sha2-256
But PanOS 10.2 only has
| server_host_key_
| ssh-rsa
you need to tell your ssh client to use the larger key size algorithm
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-03-2024 03:11 PM
adjusting the HOSTKEY to ALL doesn't help, because ALL=ECDSA or RSA, but the only RSA Hostkey Algorithms in PanOS 10.2 and higher are RSA 2048, 3072, or 4096 (known as ssh-rsa) The only way to connect is to tell the SSH client to step up to rsa 2048 or more, or go with ECDSA.
- Mark as New
- Subscribe to RSS Feed
- Permalink
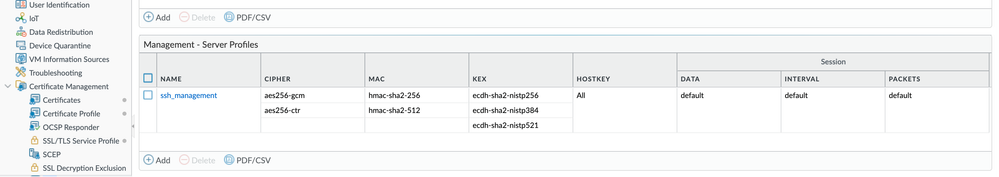
11-15-2024 08:47 PM
Make sure to restart ssh service, this will not work without it:
admin@whatever> set ssh service-restart mgmt
Here's the rest of my config:
[edit deviceconfig system ssh]
admin@whatever# show
ssh {
profiles {
mgmt-profiles {
server-profiles {
management {
ciphers aes256-gcm;
kex ecdh-sha2-nistp256;
mac hmac-sha2-256;
default-hostkey {
key-type {
all;
}
}
}
}
}
}
mgmt {
server-profile management;
}
}
Tested this in version 11.1.4-h
- 15324 Views
- 8 replies
- 1 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- PAN-OS HA UGRADE PATH in Next-Generation Firewall Discussions
- SD-WAN with ION's running 6.5.1-b5 performance issues in Prisma SD-WAN Discussions
- Error when calling “Get number of users at location(s)” API in Prisma SASE Aggregate Monitoring APIs in Prisma Access Discussions
- Strange Gateway change issue on network with Prisma Access GP Client in GlobalProtect Discussions
- SilverFort compatibility with Panorama VM-Series in General Topics