- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Newb Question: Searching Security Policies by Name (w/ Filter Operators)
- LIVEcommunity
- Discussions
- General Topics
- Re: Newb Question: Searching Security Policies by Name (w/ Filter Operators)
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-12-2017 08:15 AM
Hello!
Brand new to PAN, but diving into it as part of onboarding at with a new employer.
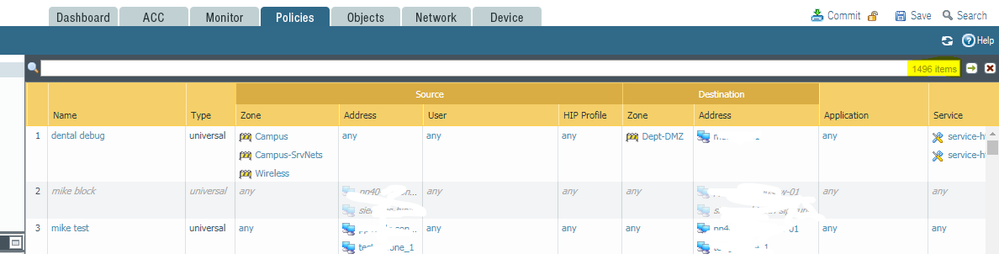
Our company has quite a few security policies (169) compared to the scale of networks I'm used to managing in my past roles (maybe 6-12 on the high end!). So, I'm keen on using the search bar to effectively sort, filter, find, and make sense of these.
I've noticed that the Log search bar (Monitor > Logs) has a little + icon that brings up the Add Log Filter dialog to help with building a more refined filter. Very cool. But, this button/ feature doesn't seem to exist in the search bar for policies (Policies > Security in particular).
Since most of our policies are named consistently, I'm trying to filter on name. For example "show me all security policies with names starting with 'VPN'" or "show me all policies with names that don't include the strings 'vpn' or 'gp'", etc. You get the idea. I've gleened the basic search operands and syntax from using the Filter tool in the Logs, so I've been trying to figure out a filter term to filter based on policy names, but I'm having 2 problems:
- 1) I can't find/figure out a search operand for "includes" (name includes 'vpn')
- 2) I don't see and can't find a wildcard option (name eq '*vpn*')
I know, I know. I can use tags and the Tag Browser to better accomplish this... but tags don't seem to be in use here (yet). While I'd like to add tags to policies for this purpose, I'm thinking there HAS to be basic search functionality to do this right now via the search bar based on naming convention. No?
All help is appreciated! Thanks!
Model PA-3020
Software Version 7.1.7
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-13-2017 12:44 AM
@locampo the 'neq' operand should help filter out unwanted matches
if you tag all your policies you could tag your VPN rules and then (tag/member neq 'vpn'), for example
there's a difference in search facilities because the logs are a database you can query while the policies are a search in XML
you could open a feature request with your local sales contact to have the 'query/filter builder' added to the policies
PANgurus - Strata specialist; config reviews, policy optimization
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-12-2017 09:16 AM - edited 07-12-2017 09:21 AM
Ignore my post, as l don't know the answer, just wanted to share the biggest security policy config from one of our customers that I have ever seen:
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-12-2017 10:31 AM
If it's in the policy name then just type it in bud. One of the very few fields where you don't actually have to do anything special for search.
As far as show me everything besides something that includes VPN; I honestly have no idea. You can do that in the CLI by utilzing the '| except VPN' option but that will search for 'VPN' anywhere within the policy not just the rulename.
As a side note are you using tags for your policies? That makes things easier to manage.
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-12-2017 01:34 PM - edited 07-12-2017 01:35 PM
Thanks, that's helpful. I think I did realize that you could just search with plain text when I first was using the search feature, but once I found the filter operands I wanted to do more sophisticated searching using the actual filter parameters and forgot you could do that.
So, this would work if I wanted to view all VPN policies or all policies named "block [whatever]".
But, I'm still very interested if there is a way to omit with an except or negate clause, such as "not ('vpn')", which doesn't seem to work. I am thinking maybe this just isn't possible in the search box for policies? But there's nowhere I can find a complete document / list of operands and search terms that will work here, so it's frustrating because I don't KNOW whether or not it's actually possible. Clearly some level of filtering is posible in this field and I found some very incomplete info on PA's site that demonstates this. But there's nowhere I've found a full list of the possibilities.
I have trouble believing there isn't documentation on this that I'm just not finding. Even Evernote (a freemium consumer-oriented product), for example, has comprehensive documentation of their supported search syntax and search grammar. I would have to imagine that Palo Alto would have as good or better documentation than Evernote.
Anyone know?
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-12-2017 02:15 PM
I did find this:
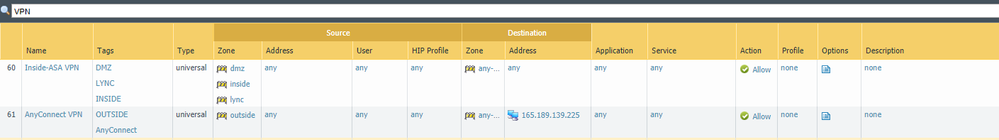
Seems like "contains" is the operand I'm looking for to search names using a string match. So:
(name contains 'vpn') and (name contains 'public')
would return a policies that included both strings only.
Unfortunately, I'm not having luck using the NOT term for negation. As in
not (name contains 'vpn')
Strange. Anyone know?
And still keen on any official, comprehensive resource that explains search terms and syntax if such documentation exists...
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-13-2017 12:44 AM
@locampo the 'neq' operand should help filter out unwanted matches
if you tag all your policies you could tag your VPN rules and then (tag/member neq 'vpn'), for example
there's a difference in search facilities because the logs are a database you can query while the policies are a search in XML
you could open a feature request with your local sales contact to have the 'query/filter builder' added to the policies
PANgurus - Strata specialist; config reviews, policy optimization
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-13-2017 06:49 AM
Thanks. So, if I'm understanding you correctly, there's no real way to negate a statement using "contains" to filter out policies based on a string match, correct? If my only options are eq, neq, and contains, then we are limited in searching for full name matches (eq = a full match of the whole name), excluding out full matches (neq = filter out everything that matches the whole name exactly), or searching for a partial match (contains = search for names containing a string). But no way to filter out names containing one or more strings based on a pattern match. Is that right?
I do realize that tags are a better way to manage multiple policies, but I haven't been with my organization for even a full month yet and it seems the current organizational scheme for security policies was to use consistent naming conventions and tags have not been used. I would like to go ahead and tag the policies moving forward, but for now I still only have read-only access to our production PA equipment, so filtering based on name is the quick and (for the moment, only) choice. Plus, it's something I'm used to doing in CLI's by piping output of commands to grep or findstr or similar pattern matching faculties (and also in tools like Evernote). So, I was hoping there was a way.
Thanks for your help, @reaper!
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-14-2017 04:45 AM
That's correct
PANgurus - Strata specialist; config reviews, policy optimization
- 1 accepted solution
- 12288 Views
- 7 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- RQL Query Works in Investigate > Search but Fails in Policy Definition (Terraform v1.5.7 Example Included) in Prisma Cloud Discussions
- Newsletter: Cloud Delivered Security Services, Oct-2025 in Advanced Threat Prevention Discussions
- How can I search a particular source&destination address in lots of security policys? in General Topics
- Group-based authorization for Azure SAML users in GlobalProtect Discussions
- Search security policies of network or related IPs in General Topics