- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
SSL decryption inconsistency
- LIVEcommunity
- Discussions
- General Topics
- Re: SSL decryption inconsistency
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
SSL decryption inconsistency
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-09-2015 06:50 AM
Hi,
I have enabled decryption on a small group for testing purposes. I have a simpel 2 rule setup, first exluding financial, health and custom white listed and then decrypt everything else.
I have a hard time finding out why the same site in the same browser on different pc's behave differently. For example my colleague got ERR_SSL_PROTOCOL_ERROR on https://reddit.com with chrome while at the same time it was ok on my pc, also with chrome. How do I examine those kinds of errors?
Further, I lack more how to's and best practises in general regarding ssl decryption. Like how you should maintain the firewalls list of trusted CA's, both changed and revoked CA's.
Any tip you have about seting it up and adminstering ssl decryption is appreciated!
Regards
Magnus
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-09-2015 08:44 AM
Refer to the following document for configuing decrytion.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-10-2015 12:26 AM - edited 09-10-2015 12:28 AM
We run 6.0.10 on 3020 in passive/active HA.
There are some helpful stuff in that link but most of it for the setup.
Could there be mismatches between certs in windows (7/8) and in palo?
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-10-2015 01:43 AM
A couple of things from my own experience with testing decryption (6.0.14 on the GWs) -
- After changing the decryption policy it can need to rebuild the certificate cache as sites are accessed, so you are best to leave off testing for 5 mins or so otherwise you can get odd results
- Browser cache can also produce different results (yes - I know SSL results shouldnt be cached, just passing on what I found) so if you get odd results be sure to CTL + F5
Might help ?
Nick.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-10-2015 04:51 AM
The policy has been running for a few months so I guess caching isn't a problem.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-15-2015 07:37 AM
Do all the clients have the trusted cert that was uploaded into the PAN? I know we perform this and chose and internal cert since it was already deployed to all of our clients. We then had to export a cert to the PAN that allowed the PAN to be a subordinate to the CA so it could genereate certs on the fly for the ssl decrypt.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-16-2015 07:27 AM
You may want to look at:
I know this is for 7.0.2 but the question is if this potential bug may have found it's way into newer versions of 6.0.x and 6.1.x.
You could try upgrading to 6.0.11 and see if it helps as well.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-16-2015 07:30 AM
Sounds like a case with support maybe in order...
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-29-2015 02:15 PM
Did you ever resolve this issue? We have had decryption in place as per the PA suggested method for about a year now. For some reason about 2 weeks ago we started getting really strange behaviour. We started randomly getting ERR_SSL_PROTOCOL_ERROR and ERR_SSL_FALLBACK_BEYOND_MINIMUM_VERSION messages. This is to users that have previously had no issues. I've started to whitelist (no decrypt) specific sites that constantly have this problem but it is a pretty frustrating.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-01-2015 01:29 AM - edited 10-01-2015 01:31 AM
Not really. Still find it hard to find the scarlet thread in all this. Assuming ssl decrypt is setup and a trusted certificate is used these are the parameters I mainly think are in play.
Version of pan-os (protocol, cipher support and cert store)
Trust store in client os (outdated and revoked certs)
Which browser (internet explorer tends to be "better" but more unsecure?)
Version of browser (older versions work better, see above)
As far as I understand chrome and firefox is implementing more and more security features regarding ssl. That means dropping support for some fallbacks that used to work before. Actually most of the problems lately is becuase browsers has dropped support for sites with unsecure configuration, ie support for outdated protocols and ciphers etc.
I still get cases though were the same browser and the same site on different client gives different results. That might be due to the client os cert store but I' not sure and I don't know how to best handle the clients cert store.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-01-2015 12:00 PM - edited 10-01-2015 12:13 PM
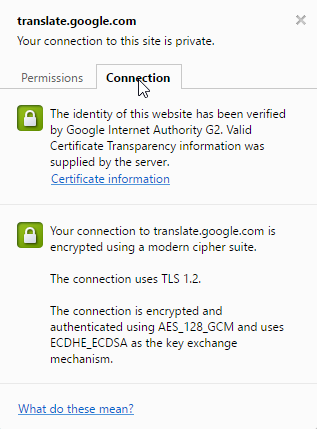
I'm running 6.1.3 and I've recently noticed that when I go to https://translate.google.com sometimes it's being decrypted and sometimes not. It seems more not. I'm going to upgrade to 6.1.7 and see if it helps. It should be decrypted.
In Chrome I notice that the cipher suite seems to change. I just test again, and it's not decrypting again and this is the cipher suite (which correct me if I'm wrong is not supported by PA decryption)
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-05-2015 12:38 AM
Similar issues here.
Usually we see that a first visit to a page is not decrypted but subsequent visits are.
Also the fact that PAN-OS doesn't support Diffie-Hellman ciphers and sites massivly switching to then, we are left in a situation were we are trying to keep up with adding them to our exception list.
So far for "insight" and "visibility"
- 9426 Views
- 14 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Prisma Access Explicit Proxy — Anti‑Spyware behavior when DNS bypasses Prisma (logging subtype + test methodology) in Prisma Access Discussions
- Unable to block download and upload for chatgpt and messengers in Next-Generation Firewall Discussions
- Decryption suddenly failed for all Webpages using Sectigo Certs in General Topics
- Chatgpt enteprise login only in Next-Generation Firewall Discussions
- Which AWS Instance Type Meets VM-300 Requirements? Documentation Seems Inconsistent in VM-Series in the Public Cloud