- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Static NAT with Port Translation
- LIVEcommunity
- Discussions
- General Topics
- Re: Static NAT with Port Translation
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-20-2016 04:18 AM
Dears,
I'm migrating some NAT rules from Cisco ASA to PAN Firewall. I don't know how to migrate a static NAT with Port Translation like the follwing example:
static (dmz,outside) tcp Public_IP 443 Private_IP 80 netmask 255.255.255.255
this static in ASA means the outside connection will be directed to the public IP and the port of 443 and ASA will divert the request to the private IP on port.
do you have any on how to do over PaloAlto
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-21-2016 02:51 PM - edited 09-21-2016 02:53 PM
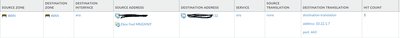
Nat Rule:
Source Zone: untrust
Dest Zone: untrust (same)
Dest int: none
Source address: any (you will filter by the security rule)
Dest Address: Public IP assigned to the internal server Service: http/https or whatever service you are publishing
Translated Packet
Source Translation: None
Destination Translation:Private ip of the server
Destinaton port: destination port of the server, if left blank it will be the same as the one specified in the "Service" above, in your case it will be the internal port where the service is responding,
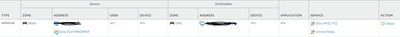
Sec Policy:
Source Zone: untrust
Desintation Zone: trust (or the zone where the server being published sits)
Destination Address: THE PUBLIC IP assigned
Appliatication/port: The port that is responding externally (not the internal port where the internal server is responding)
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-20-2016 04:50 AM
hello,
This guy helped me to understand NAT policy configuration with port translation:
https://www.youtube.com/watch?v=aVXzzZEgIA4
Thx,
Myky
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-20-2016 04:51 AM - edited 09-20-2016 04:53 AM
Hi,
This would be a destination NAT, so you would configure a NAT rule that has an original packet source & destination zone of 'outside' , destination address of your public IP and the port the outside user is connecting to.
You would then configure in the translated packet part of the rule the destination side, put in the private IP & port that the traffic is to be translated to.
You can watch this video to help as well:
For the security rule, you will need to use the source zone of the pre-NAT zone, in this case 'outside' and the destination zone will be the post-NAT zone, DMZ.
hope this helps,
Ben
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-20-2016 06:55 AM
Remember to create the Policy rule to allow the traffic that is being NATed. Your destination zone will be the DMZ, put your destination IP has to be the public IP. In your configuration, you may run into an ssl issue. The client are requesting a secured connection on port 443 and you are serving them a non-secured connection on port 80.
The above videos will make it clear as well.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-20-2016 07:58 AM
Remember to create the Policy rule to allow the traffic that is being NATed. Your destination zone will be the DMZ, but your destination IP has to be the public IP. In your configuration, you may run into an ssl issue. The client are requesting a secured connection on port 443 and you are serving them a non-secured connection on port 80.
The above videos will make it clear as well.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-21-2016 02:51 PM - edited 09-21-2016 02:53 PM
Nat Rule:
Source Zone: untrust
Dest Zone: untrust (same)
Dest int: none
Source address: any (you will filter by the security rule)
Dest Address: Public IP assigned to the internal server Service: http/https or whatever service you are publishing
Translated Packet
Source Translation: None
Destination Translation:Private ip of the server
Destinaton port: destination port of the server, if left blank it will be the same as the one specified in the "Service" above, in your case it will be the internal port where the service is responding,
Sec Policy:
Source Zone: untrust
Desintation Zone: trust (or the zone where the server being published sits)
Destination Address: THE PUBLIC IP assigned
Appliatication/port: The port that is responding externally (not the internal port where the internal server is responding)
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-22-2016 08:07 AM
Dears,
Thanks all for clarifying a soluton for such NAT scenario.
I think there sholuld be a document for different NAT scenarios to compare between ASA and PAN.
Thanks all.
- Mark as New
- Subscribe to RSS Feed
- Permalink
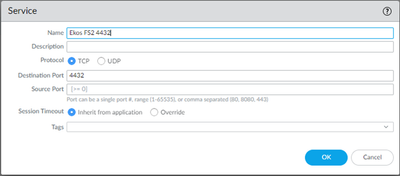
10-17-2023 10:23 AM
I am attempting to do NAT and PAT from WAN IP:4432 to Internal via a WAN IP to Internal IP:443 address. My packets are getting caught in the interzone policy. can anyone shed some light on the issue?
NAT
Policy
drop
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-18-2023 10:51 AM
Palo Alto Engineer helped me find my error. It was when I created a custom service I put in source port instead of leaving it blank. When creating a service for NAT port translation, the source port needs to be blank:
Thank you Palo support!
- 1 accepted solution
- 12364 Views
- 8 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- GRPC status UNAVAILABLE in intelligent offload in VM-Series in the Private Cloud
- Policy processing order in General Topics
- Configuration for GUI access through public IP in Next-Generation Firewall Discussions
- Bi-direction Nat logic in Next-Generation Firewall Discussions
- Dynamic ports to Static in General Topics