- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Tracking an infected computer
- LIVEcommunity
- Discussions
- General Topics
- Re: Tracking an infected computer
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-03-2014 12:18 PM
I got a notice from my ISP that we have a Conficker infected system (downadup) but I am coming up with nothing when I try to find it. The less than helpful info I recieve is the first octet of the target IP (38) and source port 61494, which map to hundreds of system. I also have a destination port of 80, again very helpful. The firewall is NATing for about 2000 systems. Has anyone used their panos box to track a system before and if so what did you do? We have ESET deployed for anti-virus and it is not showing anything right now. We could be missing a system though. I am still fairly new to my PA-3020 box so use small words please.
I have been using the threat log and tried the pre-built reports. The Monitor Logs are amazing but I can't seem to narrow the search enough to find the problem. I only have the URL filter and threat prevention license on 5.0.9
Thanks,
Todd
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-04-2014 09:23 AM
Hello Todd
The simplest way is to make a filter in Thread log
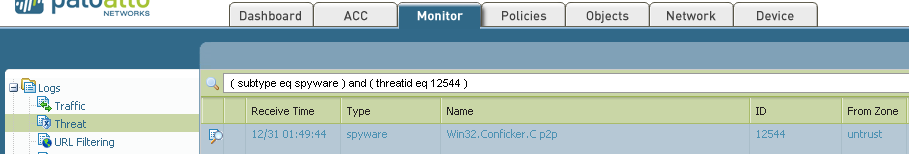
I'm not sure that every variant of Conficker has 12544 id, so You can remove "and ( threatid eq 12544 )"
Of course You mast have Thret prevention profile added to security rule that is allowing traffic from You networks to Internet.
Regards
SLawek
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-03-2014 01:28 PM
Hello Todd,
Is there any related information pops up under Monitor > Threat logs...?
Also please apply below mentioned command to stop suppressing repetitive logs on PAN FW.
# set deviceconfig setting logging log-suppression no
Thanks
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-04-2014 09:23 AM
Hello Todd
The simplest way is to make a filter in Thread log

I'm not sure that every variant of Conficker has 12544 id, so You can remove "and ( threatid eq 12544 )"
Of course You mast have Thret prevention profile added to security rule that is allowing traffic from You networks to Internet.
Regards
SLawek
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-07-2014 11:55 AM
Thanks SLawek,
I finally figured it out with your help. I ran the Threats report and found all the Suspicious DNS Query results I had been unable to find before. Each one has a different ID code that I was able to search for in the Threat log as you describe with great success. Looks like I should be able to trace this after all.
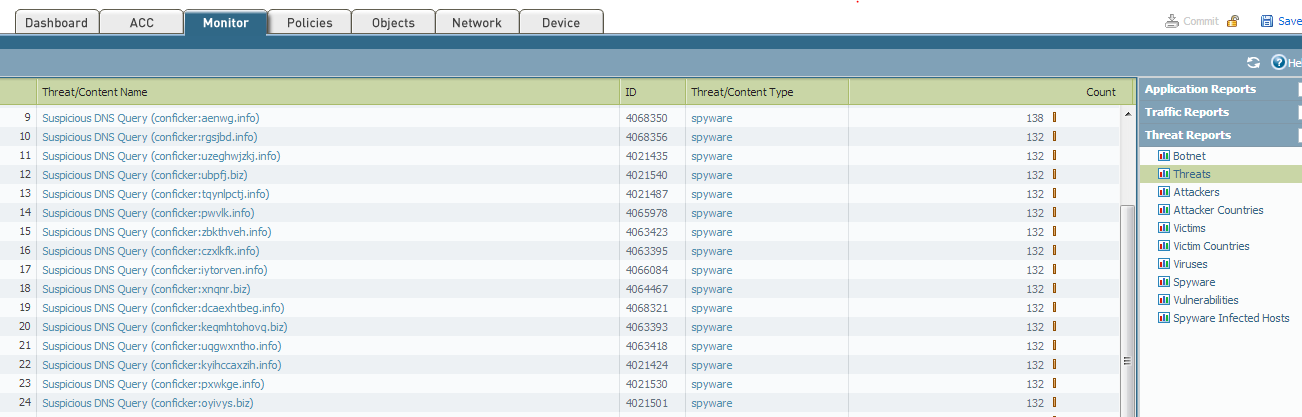
-Todd
- 1 accepted solution
- 4000 Views
- 3 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- USB Flash Drives in Cortex XSIAM Discussions
- Cortex XDR is unable to block USB viruses - the reason is unknown. in Cortex XDR Discussions
- Force logoff of user during isolation of endpoint in Cortex XDR Discussions
- How to best interpret blocked URL events for malware and C2 in Next-Generation Firewall Discussions
- GlobalProtect install restrictions in General Topics



