- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Troubleshooting SSL decryption failure of a website
- LIVEcommunity
- Discussions
- General Topics
- Troubleshooting SSL decryption failure of a website
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-10-2018 10:14 AM
Hello.
We are using panOS 8.0.7 , Pan-DB URL filtering, and SSL decryption.
We are K12 education and use many Chromebooks in the organization.
We are trying to use a system called Clever to have our students log into their Chromebooks by scanning a QR code. The problem is I cannot get the program to work. (https://clever.com/)
I know the issue is with the SSL decryption because if I exclude the device from decryption, things works correctly and I am prompted to scan my QR code. With decryption turned on, I get a hung screen and can't proceed to the next step of login.
I have worked with Palo TAC and Clever support and haven't been able to get it working.
I have many URLs excluded from decryption that Google and Clever say need to be bypassed from decyption as well.
My next thoughts would be to run some packet captures, but I'm not that familiar with Wireshark analysis. I am thinking I need to look at the headers to see if there are any other URLs which I don't have in my exclude list.
Under the traffic logs, for the sessions, I can see some entries are being decrypted. In the URL filtering logs, I can see the sessions are not being decrypted.
Anyone have any thoughts on this, or would be willing to help out?
Dan
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-16-2018 10:02 AM
Hello,
You are correct, adding URL's is the same for either. Here is hte breakdown of what I suggested:
*.domain.com = will allow anything infront of hte domain.com ,i.e. www.domain.com, mail.domain.com, etc.
domain.com = will allow anything if it doesnt have a prefix, i.e. domain.com, domain.com/whatever, etc.
So one just allows for a prefix prior to the domain name. While I cannot find the article, its best practice to perform it the way i have it outlined.
Hope that clears things up and glad its working for you!
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-10-2018 02:08 PM
Hello,
Sounds like you on are on the correct path. I'm sure many of us are willing to help, but would need to see the pcaps or any other information you are willing to share. I would agree that its probably a quick redirect somewhere that is causing the issue.
Try looking at the Unified logs from a client and see if that can tell the whole story.
Hope that helps.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-12-2018 09:10 AM
OK.
I can do a packet capture on the Palo with and without decryption turned on, so I'd hae 2 sets of captures (drop, firewall, transmit, receive)
Which ones would you like me to upload here?
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-12-2018 09:17 AM
Hello,
Do you have the unified logs of the attempts made with SSL on and off? I think that may be a better start. Sorry for the confusion.
Please filter them by the source IP of the client making the attempts.
If you would rather perform this live via webex or something. Let me know when you might have time.
Regards,
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-12-2018 01:37 PM
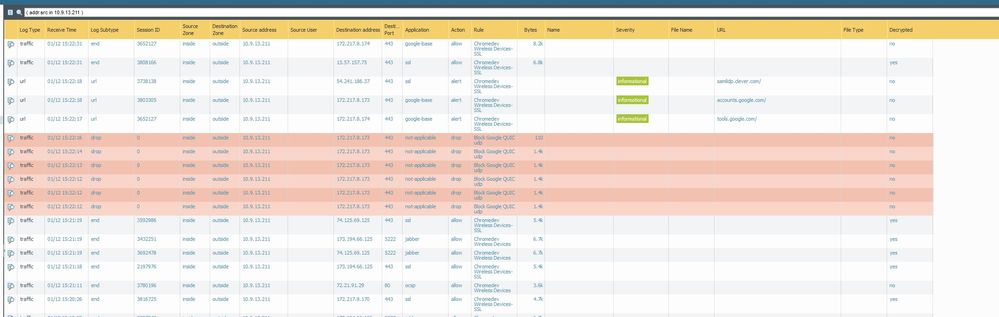
Here are the 2 screenshots. I've got the excel files also, but don't know how to upload them.

- Mark as New
- Subscribe to RSS Feed
- Permalink
01-12-2018 01:56 PM
Hello,
How are you bypassing decryption? For example when I know its a website, I create a custom URL and add the sites I dont want to decrypt there. And then create a decryption policy above my decrypt everything and set it to no decrypt.
I'm assuming you have clever.com and *.clever.com listed as no decrypt?
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-12-2018 02:13 PM
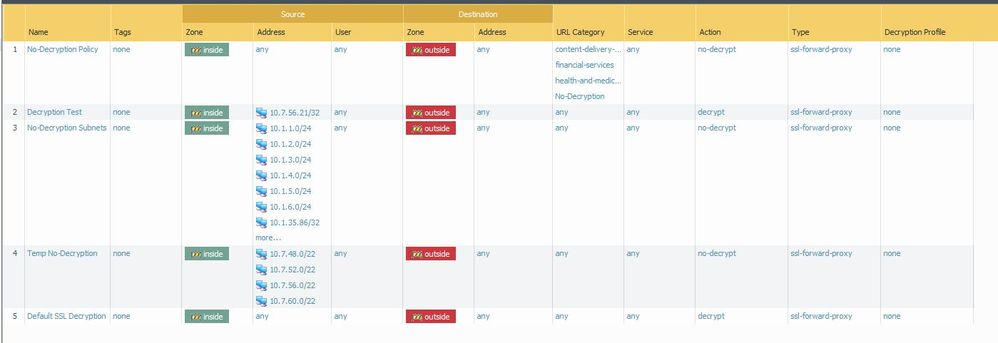
On the second line from the top in the fail screenshot, there is traffic to 13.57.157.75 that was decrypted, when I looked it up, it belonged to clever.com.
https://www.virustotal.com/en/ip-address/13.57.157.75/information/
https://www.virustotal.com/en/domain/clever.com/information/
I would say it might be a no decrypt rule that is not getting hit for some reason.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-16-2018 06:59 AM
Hello.
I've got all of my URLs in a custome URL category called "no decrypt". I've got my decryption rules with the no decryption up top
Decryption rule #1 is for bypass. All other traffic gets decrypted by rule #5. Rules 2-4 don't apply in this situation.
I also just verified that I have the following in my "no-decryption" URL category:
*.clever.com
*.clever.com/
I wasn't sure if I needed both URLs in a decryption bypass rule, so I have both.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-16-2018 07:18 AM
Hello,
The No-Decrypt URL should be"
*.clever.com
clever.com
Regards,
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-16-2018 09:41 AM
OK.
I think that fixed it.
I'm confused now about how to enter URLs into the Palo -
for adding URLs to a custom category rules, I read here on Palo's site to enter them as
*.domain
*.domain/
to catch everything. This would be if I wanted to recategorize a URL from a blocked to an allowed custom-URL category. Or vice-versa.
I thought adding them to a no-decryption rule would be the same thing.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-16-2018 10:02 AM
Hello,
You are correct, adding URL's is the same for either. Here is hte breakdown of what I suggested:
*.domain.com = will allow anything infront of hte domain.com ,i.e. www.domain.com, mail.domain.com, etc.
domain.com = will allow anything if it doesnt have a prefix, i.e. domain.com, domain.com/whatever, etc.
So one just allows for a prefix prior to the domain name. While I cannot find the article, its best practice to perform it the way i have it outlined.
Hope that clears things up and glad its working for you!
- 1 accepted solution
- 11526 Views
- 10 replies
- 1 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- stream timeout in General Topics
- Newsletter: Cloud Delivered Security Services, Oct-2025 in Advanced Threat Prevention Discussions
- Question regarding Signal messaging application in General Topics
- How to trigger a "Response page" on Palo Alto NGFWs using URL filtering & Decryption in Next-Generation Firewall Discussions
- Anyone experiencing slow websites with PANOS patched for CVE-2024-0012/CVE-2024-9474? in General Topics