- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Two ISP connections - one primary / one guest network
- LIVEcommunity
- Discussions
- General Topics
- Re: Two ISP connections - one primary / one guest network
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-16-2013 08:41 AM
Hello,
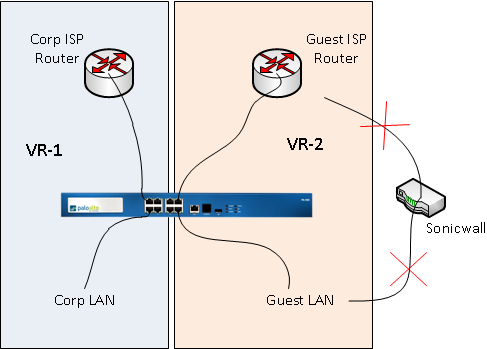
Today we have one interface designated as a WAN interface that manages our IPsec tunnels, GP Portal/Gateway, NAT for Websites, and business web browsing and needs. We have a second internet connection that we use for a guest network that goes through a really old Sonicwall (Different IP range/provider from our main WAN (untrust) link). I'm wanting to move the guest network to our PAN and setup a network zone, DHCP and hand off all the traffic to our wireless controller.
I'm seeing a lot of documentation on setting up dual ISPs for redundency, etc. This isn't quite what I am looking for. I just want to setup another untrust to trust configuration with it's own VR to pass client traffic to and from the internet. Is that as simple as my configuration needs to be or am I missing something? Thanks.
- Labels:
-
Configuration
-
Networking
-
Set Up
-
Troubleshooting
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-17-2013 12:57 PM
Hello, you are essentially correct. There are several ways to do this, but in keeping as close to your proposed solution here is what I would suggest-
Create two new zones, untrust-b and trust-b, create an L3 interface for each zone with an IP address (I would use the Sonicwall's LAN and Sonicwall WAN IP). Create new virtual router, put both interfaces in that VR, config default gateway in that VR pointing to same Default gateway as sonicwall had) Create security policy to allow inbound and outbound traffic, create NAT rules, configure DHCP on new trust L3 interface.
Move cables from Sonicwall LAN and WAN interfaces to your newly configured PA trust and untrust interfaces, Commit.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-16-2013 10:10 AM
Hi,
If i understand your question correctly. You are trying to move your guest network traffic to PAN.
In order to do that you can create a policy based forwarding and make sure you put in the source address range in the policy.
So only traffic that goes through this link is the guest network.
Here is a document that explains how to configure policy based forwarding
https://live.paloaltonetworks.com/docs/DOC-3220
Hopefully this helps.
Thank you
Numan
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-16-2013 10:35 AM
Not exactly.
We have our Main WAN link as described above. This is a service link provided a major internet provider and is a /26 network.The Guest network is a local ISP that is providing a /28. Currently we have the PAN handling our main WAN link, the /26. We have a really old Sonicwall that is handling the local ISP of /28. The /28 (guest network) is vlanned and separated from our corporate network and there is no access from either network into the other.
What I am trying to accomplish is to keep these both networks separated but managed on the same firewall. Traffic from either the corporate LAN or guest network will never merge.
I'm thinking that all I should have to is setup another virtual router, a untrust interface, trust interface, and network zone.
Is this correct? How can I clarify more?
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-17-2013 12:57 PM
Hello, you are essentially correct. There are several ways to do this, but in keeping as close to your proposed solution here is what I would suggest-
Create two new zones, untrust-b and trust-b, create an L3 interface for each zone with an IP address (I would use the Sonicwall's LAN and Sonicwall WAN IP). Create new virtual router, put both interfaces in that VR, config default gateway in that VR pointing to same Default gateway as sonicwall had) Create security policy to allow inbound and outbound traffic, create NAT rules, configure DHCP on new trust L3 interface.
Move cables from Sonicwall LAN and WAN interfaces to your newly configured PA trust and untrust interfaces, Commit.

- Mark as New
- Subscribe to RSS Feed
- Permalink
01-17-2013 01:02 PM
Wow! Thank you! Yes this is exactly what I am trying to accomplish! Thank you for confirming this. This is what I had in mind, and thought it was as simple as this but in wanting to confirm, I could not find much information. Thanks! I'll give it a shot.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-17-2013 01:12 PM
Just out of curious - what are the other ways?
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-17-2013 01:29 PM
You are welcome.
You have VLANs so you can use sub interfaces rather than using a physical interface, you can do PBF to direct traffic from the guest LAN to their ISP, now with version 5.0.1 you can direct traffic recieved on one interface (ISP) to return traffic to that same ISP, before you could not do that.
If you have the physical interfaces the dual VR route is fine.
Good luck.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-17-2013 01:32 PM
Ah - very cool. That may be what I need in the next year (network switch upgrade and move to vlans) and for another project here soon at another location. This is good to know for 5.0.x as I am still working with 4.1. Thanks again.
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-09-2020 12:35 AM
Can I do this without virtual system?
- 1 accepted solution
- 10792 Views
- 8 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Announcing the Unified Incident Framework (UIF) in Strata Cloud Manager in Strata Cloud Manager
- password not working in active device in General Topics
- UserID Redistribution Filters working weirdly in Next-Generation Firewall Discussions
- Decrypt Error When Connecting to GlobalProtect via 3rd Party Office Network in General Topics
- NGFW Blocking Router Login Traffic After Policy Update – Requesting Guidance in Next-Generation Firewall Discussions



